Identify the correct formula for Return on Investment (ROI).
Identify the correct formula for Return on Investment (ROI).
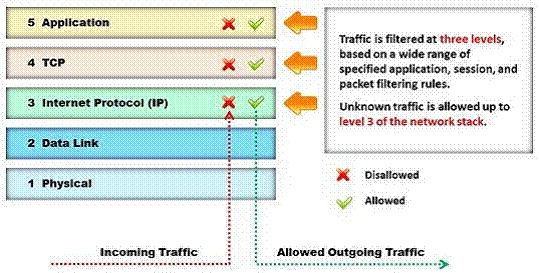
Identify the type of firewall represented in the diagram below:
Which of the following TCP flag combinations combines the problem of initiation, midstream, and termination fl
Due to illegal inputs, various types of TCP stacks respond in a different manner. Some IDSs
do not take into account the TCP protocol’s urgency feature, which could allow testers to
evade the IDS.
Penetration tester needs to try different combinations of TCP flags (e.g. none, SYN/FIN,
SYN/RST, SYN/FIN/ACK, SYN/RST/ACK, and All Flags) to test the IDS.
Which of the following TCP flag combinations combines the problem of initiation, midstream,
and termination flags with the PSH and URG?
Identify the person who will lead the penetration-testing project and be the client point of contact.
Identify the person who will lead the penetration-testing project and be the client point of
contact.
Which of the following social engineering techniques refers to this type of information theft?
A man enters a PIN number at an ATM machine, being unaware that the person next to him
was watching. Which of the following social engineering techniques refers to this type of
information theft?
What is the biggest source of data leaks in organizations today?
The Internet is a giant database where people store some of their most private information
on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS
attacks, website defacement, lost computers, accidental publishing, and more have all been
sources of major leaks over the last 15 years.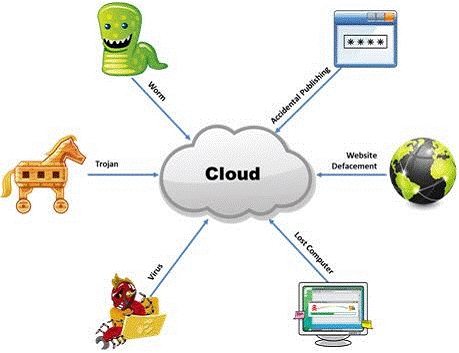
What is the biggest source of data leaks in organizations today?
What are you trying to accomplish here?
You have compromised a lower-level administrator account on an Active Directory network
of a small company in Dallas, Texas. You discover Domain Controllers through enumeration.
You connect to one of the Domain Controllers on port 389 using Idp.exe. What are you trying
to accomplish here?
Which of the following pen testing reports provides detailed information about all the tasks performed during
Choose the correct option to define the Prefix Length.
Which of the following attacks is an offline attack?
Which of the following attacks is an offline attack?