Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical
Which vulnerability assessment phase describes the scope of the assessment, identifies and
ranks the critical assets, and creates proper information protection procedures such as
effective planning, scheduling, coordination, and logistics?
Which of the following pen testing tests yields information about a company’s technology infrastructure?
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
Which of the following pen testing tests yields information about a company’s technology infrastructure?
Which of the following is an appropriate description of this response?
A penetration tester performs OS fingerprinting on the target server to identify the operating
system used on the target server with the help of ICMP packets.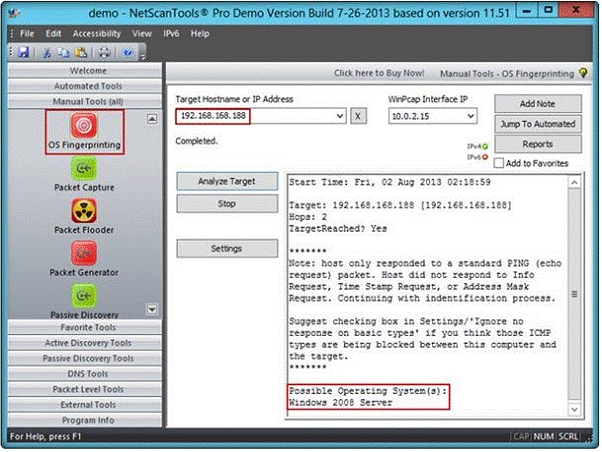
While performing ICMP scanning using Nmap tool, message received/type displays “3 – Destination Unreachable[5]” and code 3.
Which of the following is an appropriate description of this response?
What is the difference between penetration testing and vulnerability testing?
Which type of vulnerability assessment tool provides security to the IT system by testing for vulnerabilities
Which type of vulnerability assessment tool provides security to the IT system by testing for
vulnerabilities in the applications and operation system?
which port is unusual for both the TCP and UDP ports?
Traffic on which port is unusual for both the TCP and UDP ports?
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
Which of the following statements is true about Multi-Layer Intrusion Detection Systems
(mIDSs)?
What is the biggest threat to Web 2.0 technologies?
Hackers today have anever-increasinglist of weaknesses in the web application structure at
their disposal, which they can exploit to accomplish a wide variety of malicious tasks.
New flaws in web application security measures are constantly being researched, both by
hackers and by security professionals. Most of these flaws affect all dynamic web
applications whilst others are dependent on specific application technologies. In both cases,
one may observe how the evolution and refinement of web technologies also brings about
new exploits which compromise sensitive databases, provide access to theoretically secure
networks, and pose a threat to the daily operation of online businesses.
What is the biggest threat to Web 2.0 technologies?
What sort of vulnerability assessment approach starts by building an inventory of protocols found on the machi
What sort of vulnerability assessment approach starts by building an inventory of protocols
found on the machine?
you need to do in order to analyze HTTP and HTTPS request headers and the HTML source code?
During the process of fingerprinting a web application environment, what do you need to do
in order to analyze HTTP and HTTPS request headers and the HTML source code?


