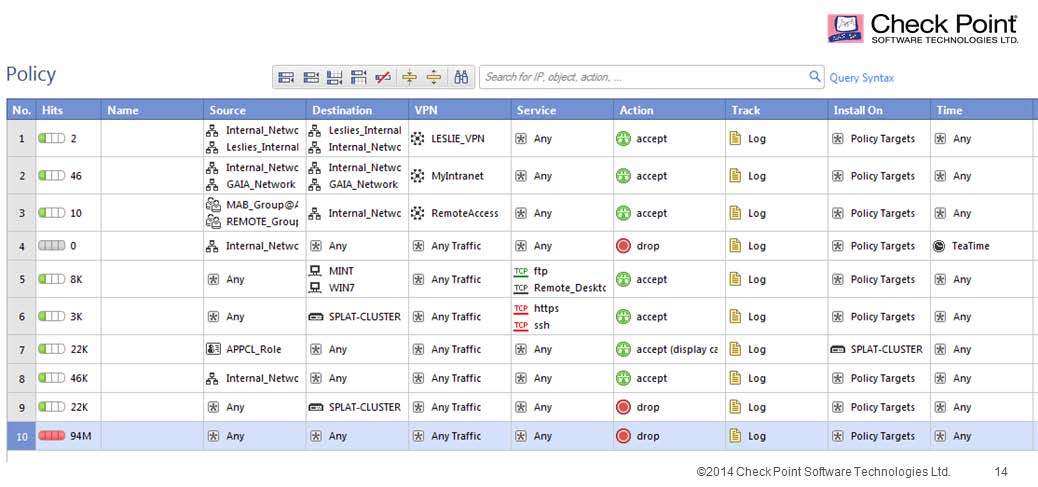
Consider the following Rule Base; What can be concluded in regards to SecureXL Accept
Templates?

A.
Accept Templates will be fully functional
B.
Accept Templates will be disabled on Rule #6
C.
Accept Templates will be disabled on Rule #4
D.
Accept Templates do not function with VPN communities in the Rule Base


When SecureXL is enabled, all packets should be accelerated, except packets that match the following conditions:
• The first packets of any new TCP session, unless a “template” exists.
• The first packet of any new UDP session.
• All packets that match a service that uses a Resource.
• Certain packets that match a service that is inspected by a SmartDefense/IPS or Web Intel features. For example, traffic where SSH protections are activated is not accelerated.
• All packets that are supposed to be dropped or rejected, according to the rule base (unless Drop Templates are enabled – refer to sk90861).
• All packets that match a rule, whose source or destination is the Gateway itself.
• All packets that match a rule with a Security Server (e.g., Anti-Virus, URL Filtering, Anti-Spam).
• All packets that match a rule with User Authentication or Session Authentication.
• Packets that are: not TCP not UDP ICMP GRE ESP
• CIFS packets.
• IPv6 packets (starting from R76, IPv6 traffic is accelerated).
• IPsec VPN Visitor Mode packets (remote users are restricted to HTTP and HTTPS traffic only).
• VPN Transport Mode packets – includes L2TP clients and GRE tunnels (when encrypting only the data layer of the original packet).
• VPN Multicast packets.
• All multicast packets (starting from R77.10, multicast traffic is accelerated).
• All fragmented packets.
• All packets with IP options.
• Packets that will be matched for ISP Redundancy (inbound/outbound interface is one of the interfaces configured for ISP Redundancy). In addition, refer to sk104679.
• TCP RST packets, when the “Spoofed Reset Protection” feature is activated.
• When using ClusterXL in Load Sharing mode with ‘Sticky Decision Function’ (SDF).
• Packets that violate stateful inspection paradigm or that are suspected to be spoofed.
• SecureXL is automatically disabled on PPP, PPTP and PPPoE interfaces.
0
0