Which two tasks might improve the user experience? (Choose two
Refer to the Exhibit.
An administrator has deployed a new virtual machine on an ESXi 5.x host. Users are complaining of poor performance on the application running on the virtual machine. Performance tools display the results shown in the exhibit.
Which two tasks might improve the user experience? (Choose two.)
Which CHAP authentication mechanism is available for both software iSCSI and dependent hardware iSCSI, but not
Which CHAP authentication mechanism is available for both software iSCSI and dependent hardware iSCSI, but not for independent hardware iSCSI?
which two VMware products/technologies?
VMware vCenter Site Recovery Manager uses which two VMware products/technologies? (Choose two.)
Which three Storage I/O Control conditions might trigger the Non-VI workload detected on the datastore alarm?
Which three Storage I/O Control conditions might trigger the Non-VI workload detected on the datastore alarm? (Choose three.)
What can be done to inform an administrator when an unacceptably large number of virtual machines are being de
A group of virtual machines has been deployed using thin disks because of limited storage space availability. The storage team has expressed concern about extensive use of this type of provisioning.
What can be done to inform an administrator when an unacceptably large number of virtual machines are being deployed using thin-disk provisioning?
Which three actions can be taken by vCenter Server in response to the trigger without running a script?
An administrator would like to have vCenter take action any time a virtual machine is using over 90% of its available resources for five minutes or longer.
Which three actions can be taken by vCenter Server in response to the trigger without running a script? (Choose three.)
What happens if an administrator modifies permissions for the user so that they can no longer create alarms?
A user has permissions to create and manage alarms and tasks for a group of virtual machines.
What happens if an administrator modifies permissions for the user so that they can no longer create alarms?
Which two methods can be used to quickly identify the issue and immediately notify an administrator so that th
Recently, a network interface card in an ESXi 5.x host has been experiencing inconsistent connectivity states.
Which two methods can be used to quickly identify the issue and immediately notify an administrator so that the issue can be resolved? (Choose two.)
What change can the administrator make to correct the problem?
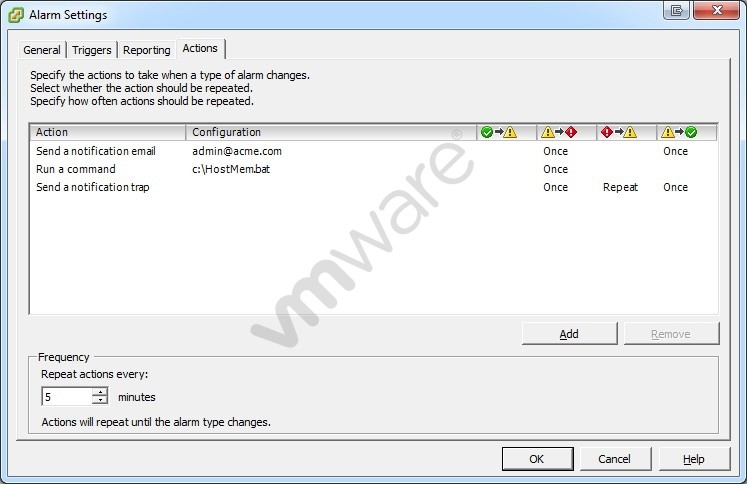
Refer to the Exhibit.
An administrator is seeing a warning on one of their hosts. The warning in the Triggered Alarms panel appears to come from a custom configured host alarm. The administrator has not seen any actions taken for this alarm even though the actions are configured in the alarm definition. The configured actions are shown in the exhibit.
What change can the administrator make to correct the problem?
Which three modifications must be made to the default settings in the alarm definition to satisfy the stated r
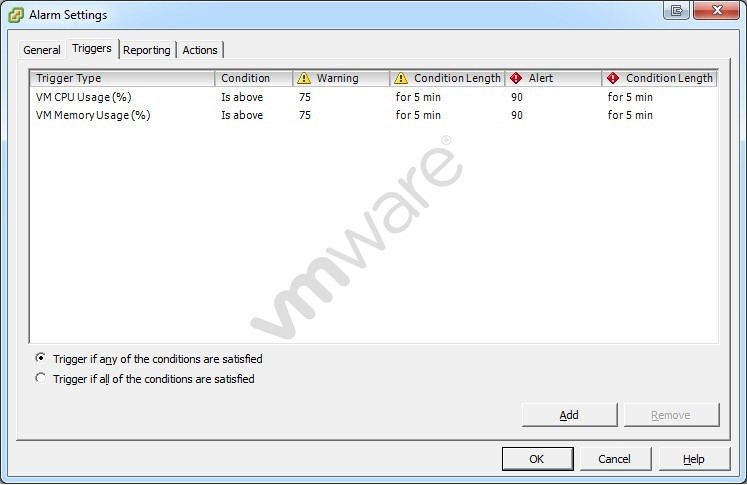
Refer to the Exhibit.
ACME Party Supplies Corporation has a requirement to monitor all virtual machines in a vSphere 5 environment for CPU and Memory usage. An administrator configures an alarm in vCenter Server to send an alert when any VM exceeds 65% memory utilization and 75% CPU utilization. The alarm should warn administrators if the virtual machine is within 10% of the defined thresholds. The alarm has been created with the default options as shown in the exhibit.
Which three modifications must be made to the default settings in the alarm definition to satisfy the stated requirements? (Choose three.)