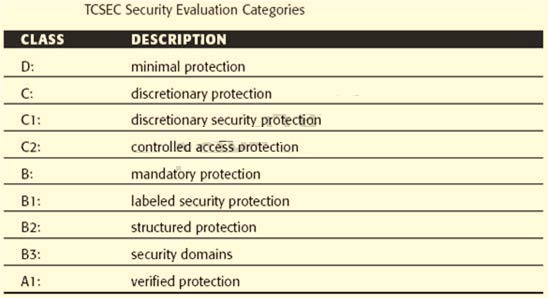
Which general TCSEC security class category describes that mandatory access policies be enforced in
the TCB? Exhibit:

A.
A
Verified protection; formal methods (A1) Source: DoD 5200.28-STD Department of Defense
Trusted Computer System Evaluation Criteria.
QUESTION 1889
What does the Spiral Model depict?
Aspiral that incorporates various phases of software development
B.
B
Mandatory protection (B1, B2, B3)
Aspiral that models the behavior of biological neurons
C.
C
Discretionary protection (C1&C2)
The operation of expert systems
D.
D
Minimal protection
Information security checklists
D.
D
Minimal protection
Information security checklists
C.
C
Discretionary protection (C1&C2)
The operation of expert systems
B.
B
Mandatory protection (B1, B2, B3)
Aspiral that models the behavior of biological neurons
A.
A
Verified protection; formal methods (A1) Source: DoD 5200.28-STD Department of Defense
Trusted Computer System Evaluation Criteria.
QUESTION 1889
What does the Spiral Model depict?
Aspiral that incorporates various phases of software development
A.
A
Verified protection; formal methods (A1) Source: DoD 5200.28-STD Department of Defense
Trusted Computer System Evaluation Criteria.
QUESTION 1889
What does the Spiral Model depict?
Aspiral that incorporates various phases of software development
B.
B
Mandatory protection (B1, B2, B3)
Aspiral that models the behavior of biological neurons
C.
C
Discretionary protection (C1&C2)
The operation of expert systems
D.
D
Minimal protection
Information security checklists
Explanation:
The Trusted Computer System Evaluation Criteria [Orange Book] defines major hierarchical classes of
security by the letters D (least secure) through A (most secure):The correct answer is a a spiral that incorporates various phases of software development. The other
answers are distracters.