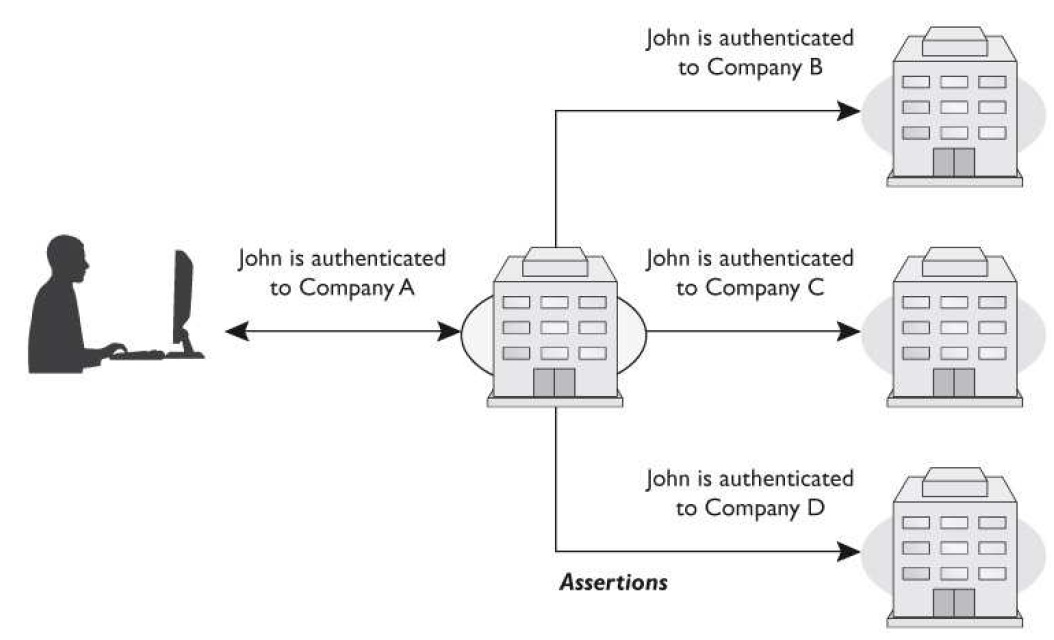
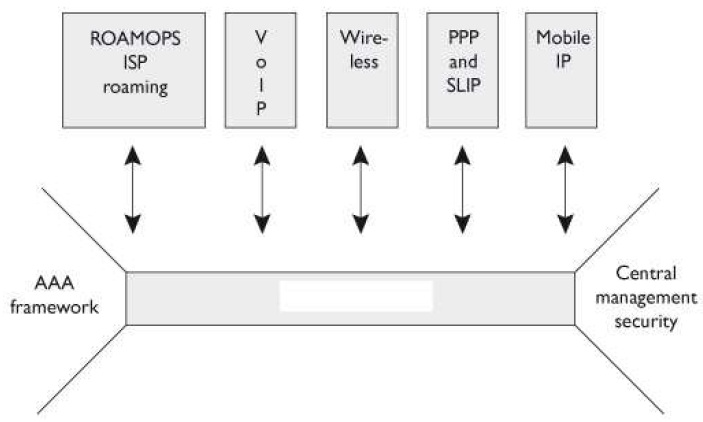
What technology within identity management is illustrated in the graphic that follows?
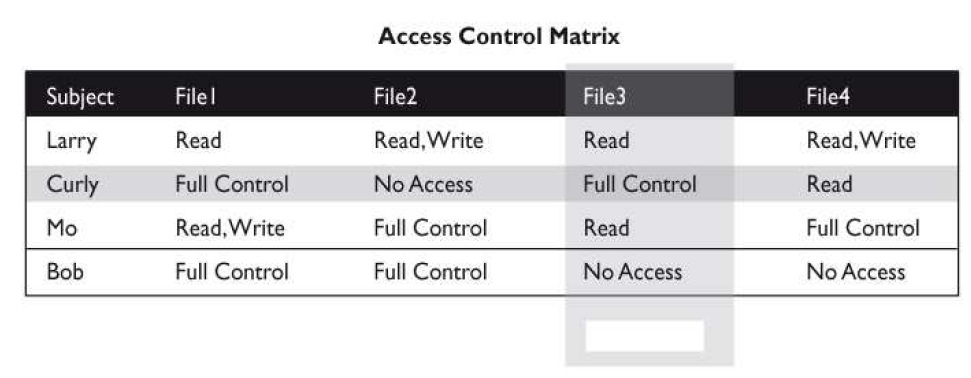
What is the column in this type of matrix referred to as?
Which of the following is illustrated in the graphic that follows?
What type of markup language allows company interfaces to pass service requests and the receiving company prov
What type of markup language allows company interfaces to pass service requests and the receiving company provision access to these services?
Which of the following best describes the differences between these countermeasures?
Alex works for a chemical distributor that assigns employees tasks that separate their duties and routinely rotates job assignments. Which of the following best describes the differences between these countermeasures?
Of the following, what is the primary item that a capability listing is based upon?
Of the following, what is the primary item that a capability listing is based upon?
What type of identity theft is this?
Sam plans to establish mobile phone service using the personal information he has stolen from his former boss. What type of identity theft is this?
Which of the following is characteristic of a rule-based IDS?
A rule-based IDS takes a different approach than a signature-based or anomaly-based system. Which of the following is characteristic of a rule-based IDS?
What type of IDS builds a profile of an environment’s normal activities and assigns an anomaly score to
There are several types of intrusion detection systems (IDSs). What type of IDS builds a profile of an environment’s normal activities and assigns an anomaly score to packets based on the profile?
Which of the following is not a factor he needs to consider when choosing the products?
Harrison is evaluating access control products for his company. Which of the following is not a factor he needs to consider when choosing the products?