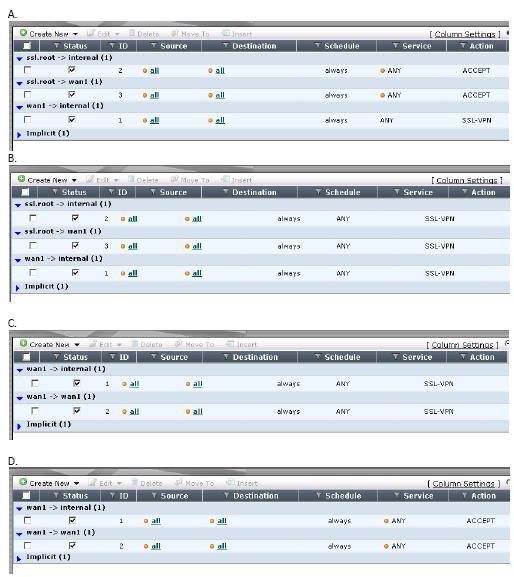
Which firewall policies are needed to allow the end user to not only access the internal network but also reac
An end user logs into the SSL VPN portal and selects the Tunnel Mode option by clicking on
the “Connect” button. The administrator has not enabled split tunneling and so the end user
must access the Internet through the SSL VPN Tunnel. Which firewall policies are needed
to allow the end user to not only access the internal network but also reach the Internet?
Which of the following antivirus and attack definition update features are supported by FortiGate units?
Which of the following antivirus and attack definition update features are supported by
FortiGate units? (Select all that apply.)
which action?
By default the Intrusion Protection System (IPS) on a FortiGate unit is set to perform which
action?
which types of network traffic?
A FortiGate unit can scan for viruses on which types of network traffic? (Select all that
apply.)
Which statement is correct regarding virus scanning on a FortiGate unit?
Which statement is correct regarding virus scanning on a FortiGate unit?
Which of the following statements are correct regarding URL Filtering on the FortiGate unit?
Which of the following statements are correct regarding URL Filtering on the FortiGate unit?
(Select all that apply.)
Which of the following statements is correct regarding URL Filtering on the FortiGate unit?
Which of the following statements is correct regarding URL Filtering on the FortiGate unit?
Which of the following Regular Expression patterns will make the term "bad language" case insensitiv
Which of the following Regular Expression patterns will make the term “bad language” case
insensitive?
Which of the following steps is required to prevent a user from being presented with a web browser warning whe
SSL content inspection is enabled on the FortiGate unit. Which of the following steps is
required to prevent a user from being presented with a web browser warning when
accessing an SSL-encrypted website?
Which of the following statements describes the method of creating a policy to block access to an FTP site?
Which of the following statements describes the method of creating a policy to block access
to an FTP site?