Which of the following logging options are supported on a FortiGate unit?
Which of the following logging options are supported on a FortiGate unit? (Select all that
apply.)
Once inside the policy, the following logic is followed:
In order to match an identity-based policy, the FortiGate unit checks the IP information.
Once inside the policy, the following logic is followed:
Which of the following statements regarding the firewall policy authentication timeout is true?
Which of the following statements regarding the firewall policy authentication timeout is
true?
Two-factor authentication is supported using the following methods?
Two-factor authentication is supported using the following methods? (Select all that apply.)
Which of the following statements are true regarding Local User Authentication?
Which of the following statements are true regarding Local User Authentication? (Select all
that apply.)
Which of the statements below are true regarding firewall policy disclaimers?
Which of the statements below are true regarding firewall policy disclaimers? (Select all that
apply.)
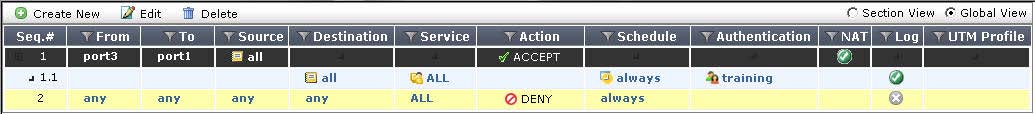
Which of the following statements are correct based on the firewall configuration illustrated in the exhibit?
which of the following source IP addresses would the web server consider the HTTP request to be initiated?
When browsing to an internal web server using a web-mode SSL VPN bookmark, from
which of the following source IP addresses would the web server consider the HTTP
request to be initiated?
Which of the following configuration steps are required to achieve these objectives?
You are the administrator in charge of a FortiGate unit which acts as a VPN gateway. You
have chosen to use Interface Mode when configuring the VPN tunnel and you want users
from either side to be able to initiate new sessions. There is only 1 subnet at either end and
the FortiGate unit already has a default route. Which of the following configuration steps are
required to achieve these objectives? (Select all that apply.)
which log will a UTM event message be stored?
A firewall policy has been configured such that traffic logging is disabled and a UTM
function is enabled. In addition, the system setting ‘utm-incident-traffic-log’ has been
enabled. In which log will a UTM event message be stored?