Once inside the policy, the following logic is followed:
In order to match an identity-based policy, the FortiGate unit checks the IP information. Once inside
the policy, the following logic is followed:
What is the correct behavior when the email attachment …
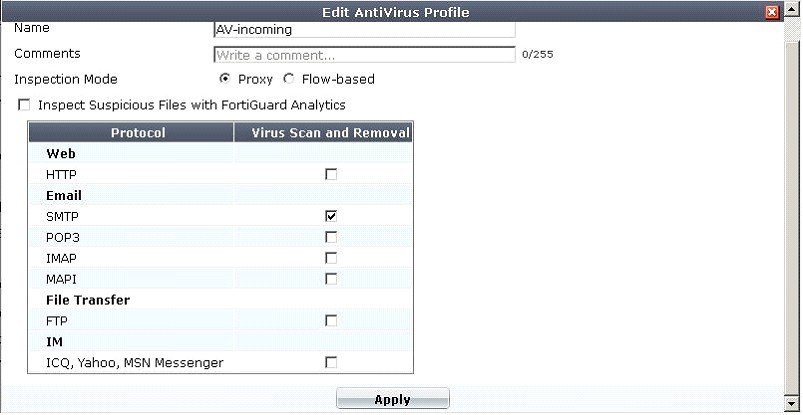
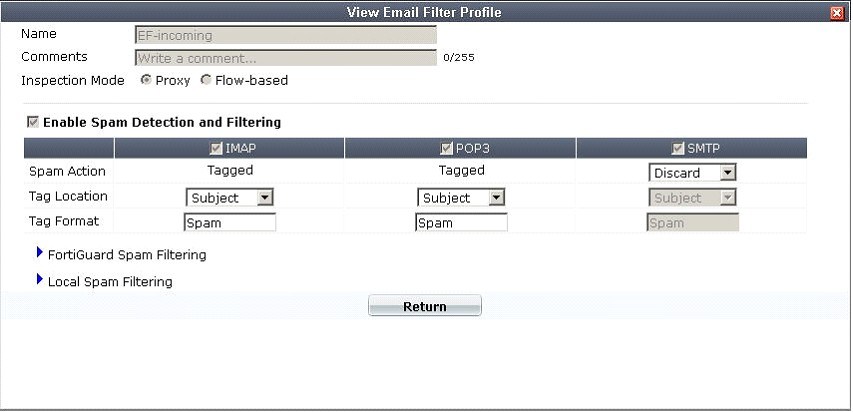
A firewall policy has been configured for the internal email server to receive email from external
parties through SMTP. Exhibits A and B show the antivirus and email filter profiles applied to this
policy.
Exhibit A:
Exhibit B:
What is the correct behavior when the email attachment is detected as a virus by the FortiGate
antivirus engine?
which of the following statements describes the action …
If no firewall policy is specified between two FortiGate interfaces and zones are not used, which of
the following statements describes the action taken on traffic flowing between these interfaces?
What are the valid sub-types for a Firewall type policy?
What are the valid sub-types for a Firewall type policy? (Select all that apply)
what is a valid dmz DHCP addressing range?
If a FortiGate unit has a dmz interface IP address of 210.192.168.2 with a subnet mask of
255.255.255.0, what is a valid dmz DHCP addressing range?
Which of the following statements regarding overrides a…
Users may require access to a web site that is blocked by a policy. Administrators can give users
the ability to override the block. Which of the following statements regarding overrides are correct?
(Select all that apply.)
Which of the following statements best describes how to…
An issue could potentially occur when clicking Connect to start tunnel mode SSL VPN.
The tunnel will start up for a few seconds, then shut down.
Which of the following statements best describes how to resolve this issue?
Which statement is correct regarding virus scanning on …
Which statement is correct regarding virus scanning on a FortiGate unit?
Two-factor authentication is supported using the follow…
Two-factor authentication is supported using the following methods? (Select all that apply.)
Which of the following steps is required to prevent a u…
SSL content inspection is enabled on the FortiGate unit. Which of the following steps is required to
prevent a user from being presented with a web browser warning when accessing an SSLencrypted website?