which of the following describes the difference between the block and quarantine actions?
For Data Leak Prevention, which of the following describes the difference between the block
and quarantine actions?
How can DLP file filters be configured to detect Office 2010 files?
How can DLP file filters be configured to detect Office 2010 files? (Select all that apply.)
what action will the FortiGate unit take?
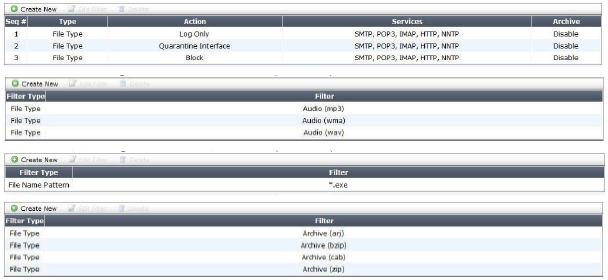
Examine the Exhibits shown below, then answer the question that follows. Review the
following DLP Sensor (Exhibit 1): Review the following File Filter list for rule #1 (Exhibit 2):
Review the following File Filter list for rule #2 (Exhibit 3): Review the following File Filter list
for rule #3 (Exhibit 4): An MP3 file is renamed to ‘workbook.exe’ and put into a ZIP archive.
It is then sent through the FortiGate device over HTTP. It is intercepted and processed by
the configuration shown in the above Exhibits 1-4. Assuming the file is not too large for the
File scanning threshold, what action will the FortiGate unit take?
Which of one the following profiles could be enabled in order to prevent the file from passing through the For
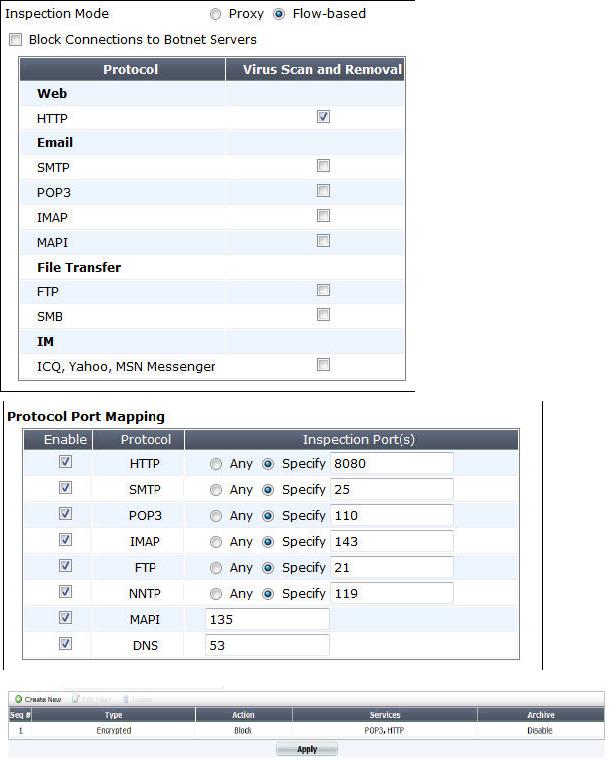
The eicar test virus is put into a zip archive, which is given the password of “Fortinet” in
order to open the archive. Review the configuration in the exhibits shown below; then
answer the question that follows. Exhibit A – Antivirus Profile: Exhibit B – Non-default UTM
Proxy Options Profile: Exhibit C – DLP Profile: Which of one the following profiles could be
enabled in order to prevent the file from passing through the FortiGate device over HTTP on
the standard port for that protocol?
which of the following statements are correct?
With FSSO, a domain user could authenticate either against the domain controller running
the Collector Agent and Domain Controller Agent, or a domain controller running only the
Domain Controller Agent. If you attempt to authenticate with the Secondary Domain
Controller running only the Domain Controller Agent, which of the following statements are
correct? (Select all that apply.)
Select the answer that describes what the CLI command diag debug authd fsso list is used for.
Select the answer that describes what the CLI command diag debug authd fsso list is used
for.
What are the requirements for a cluster to maintain TCP connections after device or link failover?
What are the requirements for a cluster to maintain TCP connections after device or link
failover? (Select all that apply.)
which of the following statements are correct?
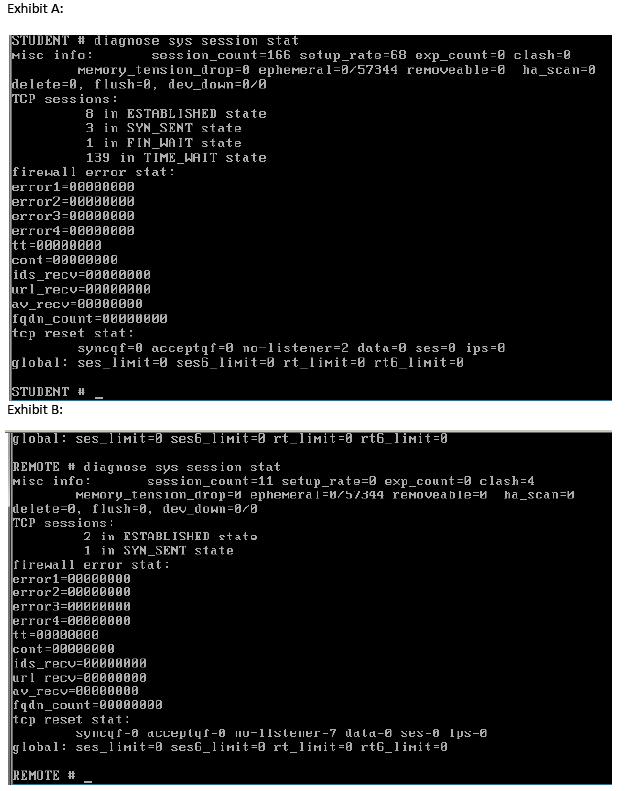
Two devices are in an HA cluster, the device hostnames are STUDENT and REMOTE.
Exhibit A shows the command output of ‘diag sys session stat’ for the STUDENT device.
Exhibit B shows the command output of ‘diag sys session stat’ for the REMOTE device.
Exhibit A: Exhibit B: Given the information provided in the exhibits, which of the following
statements are correct? (Select all that apply.)
Which of the following statements are correct about the HA diag command diagnose sys ha resetuptime?
Which of the following statements are correct about the HA diag command diagnose sys ha
resetuptime? (Select all that apply.)