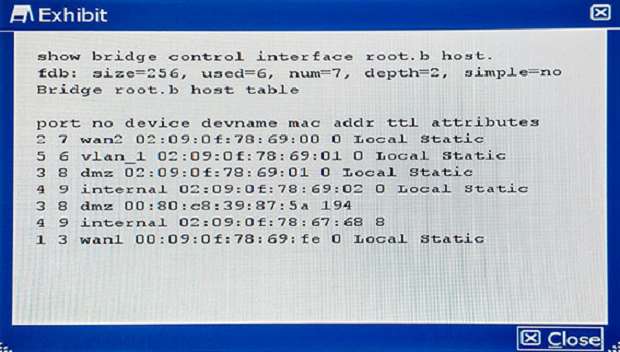
Which two groups of CLI commands allow you to see infor…
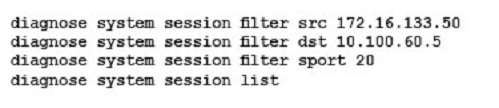
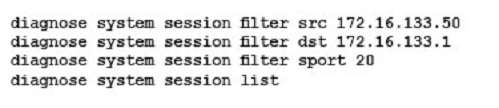
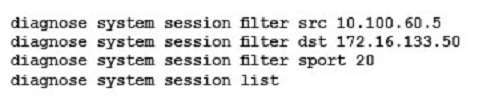
You are investigating a problem related to FTP active mode. You use a test PC with IP address 10.100.60.5 to connect to the FTP server at 172.16.133.50 and transfer a large file. The FortiGate translates source address
(SNAT) in network 10.100.60.0/24 to the IP address 172.16.133.1.
Which two groups of CLI commands allow you to see information related to this FTP connection (Choose two.)
A)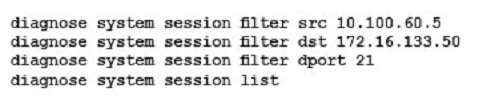
Which statement is correct?
how many hosts are connected to the FortiGate?
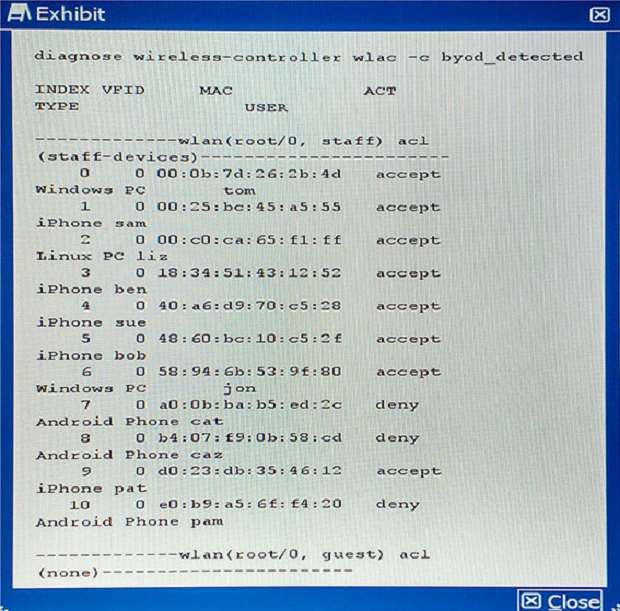
Which three statements are true?
Which two configurations will resolve the problem? (Cho…
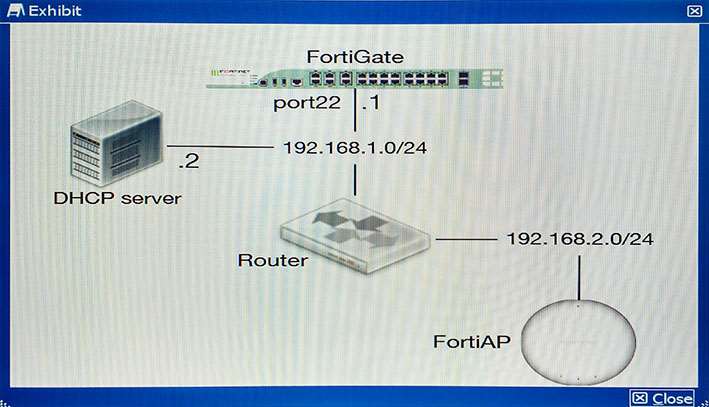
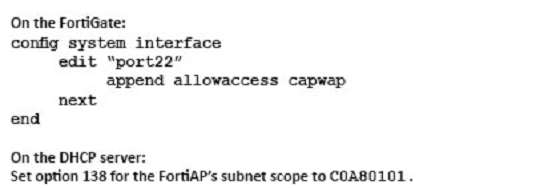
Which statement describes a valid solution for this req…
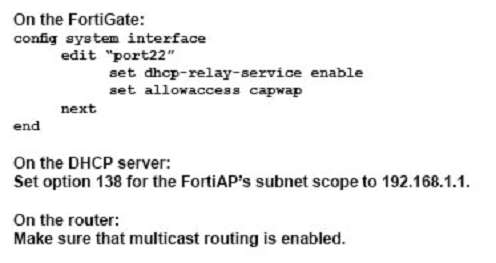
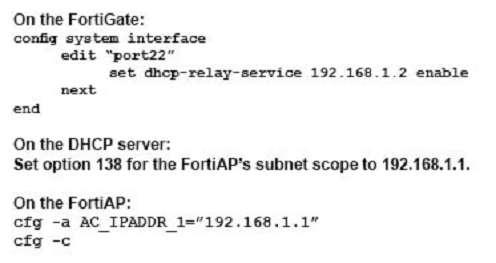
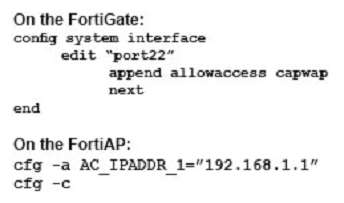
You are asked to implement a wireless network for a conference center and need to provision a high number of access points to support a large number of wireless client connections.
Which statement describes a valid solution for this requirement?
Which static routing configuration meets the requirements?
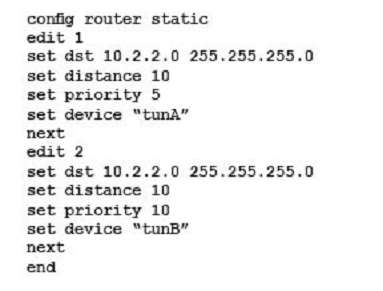
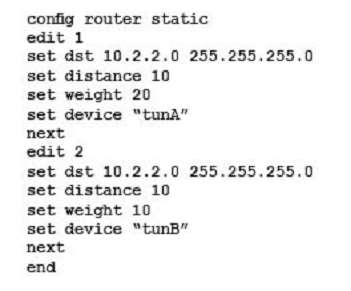
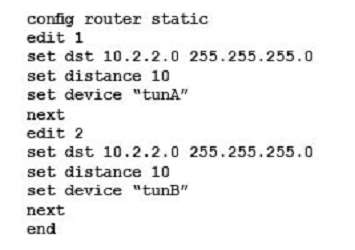
The FortiGate is used as an IPsec gateway at a branch office. Two tunnels, tunA and tunB, are established between this FortiGate and the headquarters’ IPsec gateway. The branch office’s subnet is 10.1.1.0/24. The headquarters’ subnet is 10.2.2.0/24. The desired usage for tunA and tunB has been defined as follows:
– sessions initiated from 10.1.1.0/24 to 10.2.2.0/24 must be routed out over tunA when tunA is up
– sessions initiated from 10.1.1.0/24 to 10.2.2.0/24 have to be routed out over tunB when tunA is down
– sessions initiated from 10.2.2.0/24 can ingress either on tunA or on tunB
Which static routing configuration meets the requirements?
A)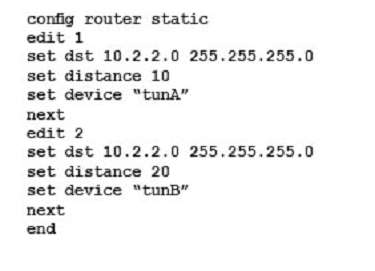
Which three missing configuration statements are needed…
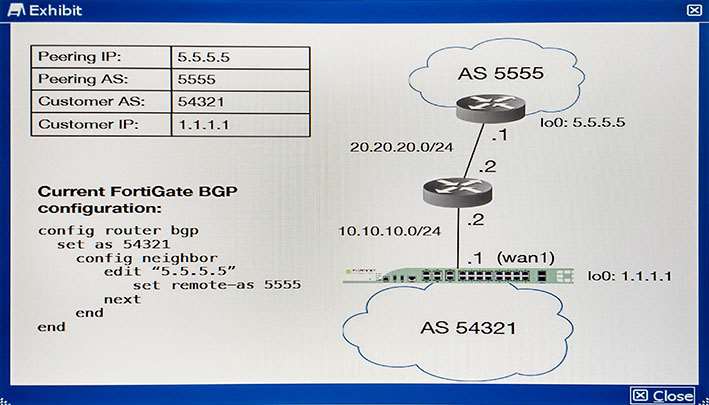
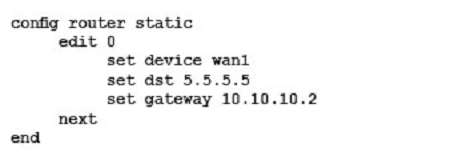
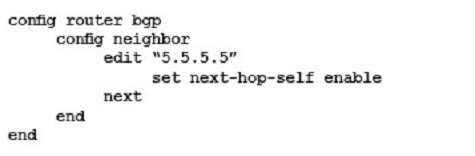
You must establish a BGP peering with a service provider. The provider has supplied you with BGP peering parameters and you performed the basic configuration shown in the exhibit on your FortiGate unit. You notice that your peering session is not coming up.
Which three missing configuration statements are needed to make this configuration functional? (Choose three.)
A)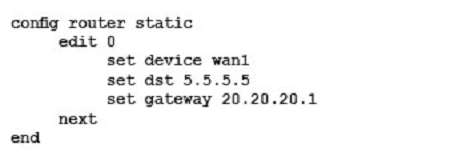
Which three solutions satisfy these requirements?
You are asked to design a secure solution using Fortinet products for a company. The company recently has
Web servers that were exploited and defaced. The customer has also experienced Denial or Service due to
SYN Flood attacks. Taking this into consideration, the customer’s solution should have the following requirements:
– management requires network-based content filtering with man-in-the-middle inspection
– the customer has no existing public key infrastructure but requires centralized certificate management
– users are tracked by their active directory username without installing any software on their hosts
– Web servers that have been exploited need to be protected from the OWASP Top 10
– notification of high volume SYN Flood attacks when a threshold has been triggered
Which three solutions satisfy these requirements? (Choose three.)
Which high availability solution would you implement?
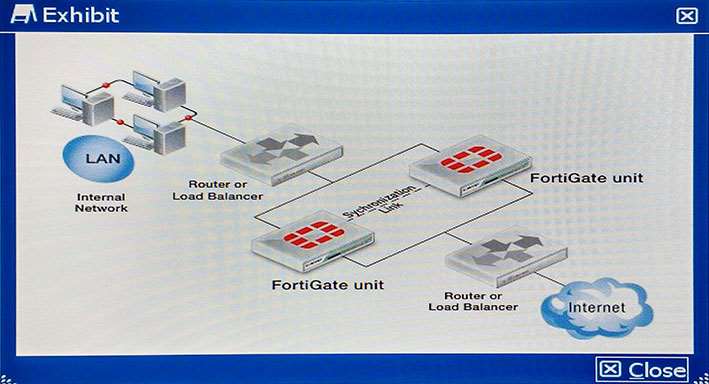
A customer just bought an additional FortiGate device and plans to use their existing load balancer to distribute traffic across two FortiGate units participating on a BGP network serving different neighbors. The customer has mixed traffic of IPv4 and IPv6 TCP, UDP, and ICMP. The two FortiGate devices shown in the exhibit should be redundant to each other so that the NAT session and active session tables will synchronize and fail over to the unit that is still operating without any loss of data if one of the units fail.
Which high availability solution would you implement? http://docs.fortinet.com/uploaded/files/1074/fortigate-ha-40-mr2.pdf