What is contained within a scope in XenDesktop?
What is contained within a scope in XenDesktop?
Which PowerShell cmdlet will a Citrix Administrator use…
Which PowerShell cmdlet will a Citrix Administrator use to show a list of all configured published
applications along with associated user names in a XenApp 7.6 environment?
Which command could the engineer run to check the logs that will contain such details?
A network engineer is investigating issues and suspects that a new server that has been recently added to the
environment has the same IP address as a virtual server that is configured on the NetScaler.
Which command could the engineer run to check the logs that will contain such details?
Which log file should a Citrix Administrator use to troubleshoot a cluster node in the INACTIVE state?
Which log file should a Citrix Administrator use to troubleshoot a cluster node in the INACTIVE state?
Which feature should the administrator use?
A network engineer wants to hide the IP address of the outgoing packets by changing it to
the IP of the VIP. Which feature should the administrator use?
What would the administrator choose to begin collecting data to evaluate under Technical Support Tools using t
In an effort to troubleshoot NetScaler Gateway, a Citrix Administrator needs to capture packets to
validate basic traffic flow (IP and port information).
What would the administrator choose to begin collecting data to evaluate under Technical Support
Tools using the NetScaler Configuration Utility?
Which two methods could the network engineer use to restrict these services?
During a recent security penetration test, several ports on the management address were
identified as providing unsecured services. Which two methods could the network engineer
use to restrict these services? (Choose two.)
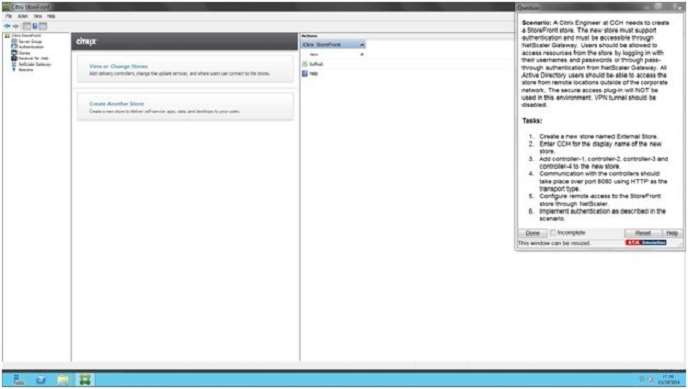
Create a new store named External Store.
SIMULATION
Scenario:
A Citrix Engineer at CCH needs to create a StoreFront store. The new store must support authentication and
must be accessible through NetScaler Gateway. Users should be allowed to access resources from the store
by logging in with their usernames and passwords or through pass-through authentication from NetScaler
Gateway. All Active Directory users should be able to access the store from remote locations outside of the
corporate network. The secure access plug-in will NOT be used in this environment. VPN tunnel should be
disabled.
Tasks:
1. Create a new store named External Store.
2. Enter CCH for the display name of the new store.
3. Add controller-1, controller-2, controller-3 and controller-4 to the new store.
4. Communication with the controllers should take place over port 8080 using HTTP as the transport type.
5. Configure remote access to the StoreFront store through NetScaler.
6. Implement authentication as described in the scenario.
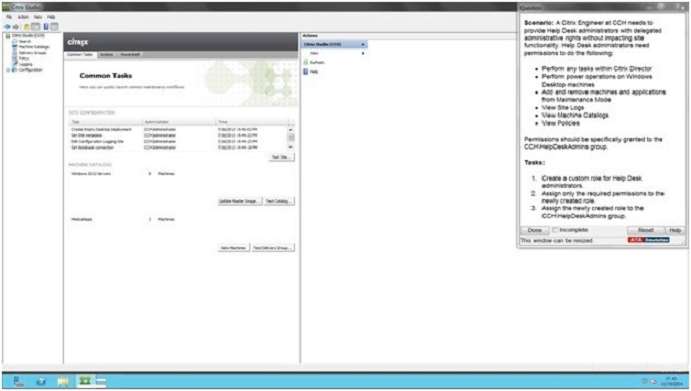
Help Desk administrators need permissions to do the following:
SIMULATION
Scenario:
A Citrix Engineer at CCH needs to provide Help Desk administrators with delegated administrative rights
without impacting site functionality.
Help Desk administrators need permissions to do the following:
– Perform any tasks within Citrix Director
– Perform power operations on Windows Desktop machines
– Add and remove machines and applications from Maintenance Mode
– View Site Logs
– View Machine Catalogs
– View Policies
Permissions should be specifically granted to the CCH\\HelpDeskAdmins group.
Tasks:
1. Create a custom role for Help Desk administrators.
2. Assign only the required permissions to the newly created role.
3. Assign the newly created role to the CCH\\HelpDeskAdmins group.
use the existing site, store, and device collection to implement…
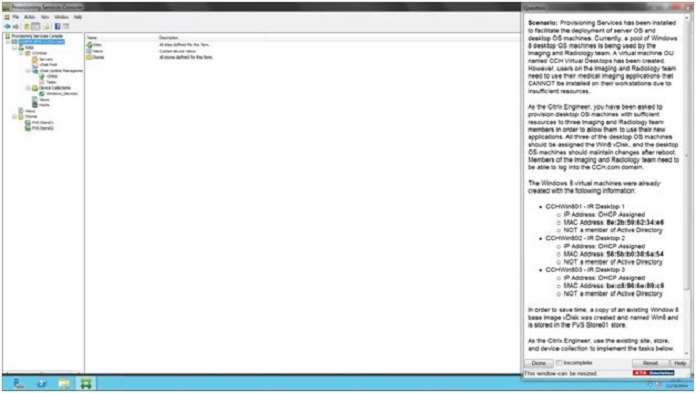
SIMULATION
Scenario:
Provisioning Services has been installed to facilitate the deployment of server OS and desktop OS machines.
Currently, a pool of Windows 8 desktop OS machines is being used by the Imaging and Radiology team. A
virtual machine OU named CCH Virtual Desktops has been created. However, users on the Imaging and
Radiology team need to use their medical imaging applications that CANNOT be installed on their workstations
due to insufficient resources.
As the Citrix Engineer, you have been asked to provision desktop OS machines with sufficient resources to
three Imaging and Radiology team members in order to allow them to use their new applications. All three of
the desktop OS machines should be assigned the Win8 vDisk, and the desktop OS machines should maintain
changes after reboot. Members of the Imaging and Radiology team need to be able to log into the CCH.com
domain.
The Windows 8 virtual machines were already created with the following information:
CCHWin801 – IR Desktop 1
IP Address: DHCP Assigned
MAC Address: 56:5b:b0:38:6a:54
NOT a member of Active DirectoryCCHWin803 – IR Desktop 3
CCHWin802 – IR Desktop 2
IP Address: DHCP Assigned
MAC Address: be:c8:96:6e:89:c9
NOT a member of Active Directory
In order to save time, a copy of an existing Window 8 base image vDisk was created and named Win8 and is
stored in the PVS StoreOI store.
As the Citrix Engineer, use the existing site, store, and device collection to implement the tasks below.
Tasks:
1. Create and configure all 3 of the Windows 8 desktop OS machines as target devices to boot using the Win8
vDisk.
2. Name the target devices CCHWin801, CCHWin802, and CCHWin803.
3. Modify the vDisk as necessary to meet the requirements outlined in the scenario.