Which attack exploits incorrect boundary checking in network software?
Which attack exploits incorrect boundary checking in network software?
how do you add an additional participant to a call on your MultiSite-enabled endpoint?
While on a call, using the remote control, how do you add an additional participant to a call on your
MultiSite-enabled endpoint?
Where should you report suspected security vulnerability in Cisco router software?
Where should you report suspected security vulnerability in Cisco router software?
Which three are true statements regarding the Cisco TelePresence endpoint product set?
Which three are true statements regarding the Cisco TelePresence endpoint product set?
(Choose three.)
which two pieces of useful information would be found in a syslog message?
When investigating potential network security issues, which two pieces of useful information would
be found in a syslog message? (Choose two.)
What are the two methods for pairing an 8-inch Cisco TelePresence Touch panel to a Codec C90?
What are the two methods for pairing an 8-inch Cisco TelePresence Touch panel to a Codec C90?
(Choose two.)
Which command would provide you with interface status information on a Cisco IOS router?
Which command would provide you with interface status information on a Cisco IOS router?
Which statement is true regarding passwords on a Cisco TelePresence MX, EX, C Series, or SX20 device?
Which statement is true regarding passwords on a Cisco TelePresence MX, EX, C Series, or
SX20 device?
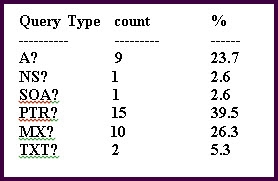
Which DNS Query Types pertains to email?
which two statements are true?
When configuring a Cisco TelePresence EX, MX, or C Series device, which two statements are
true? (Choose two.)