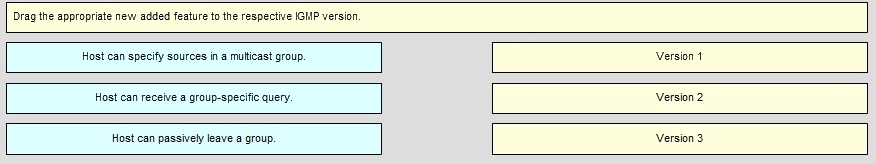
Drag the appropriate new added feature to the respective IGMP version.
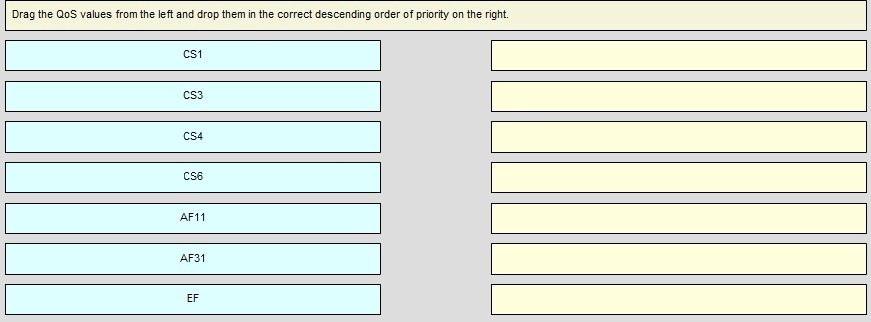
Drag the QoS value from the left and drop them in the correct descending order or priority on the right.
Which device performs the enforcement of posture assessment for a wireless client when implementing a NAC appl
Which device performs the enforcement of posture assessment for a wireless client when
implementing a NAC appliance solution?
Which of these statements best describes the Cisco Compatible Extensions "AP Specified Max Power" fe
Which of these statements best describes the Cisco Compatible Extensions “AP Specified Max
Power” feature?
Which type of attack is characterized by an evil twin?
Which type of attack is characterized by an evil twin?
Which type of attack is a result of a WLAN being overwhelmed by 802.1X authentication requests?
Which type of attack is a result of a WLAN being overwhelmed by 802.1X authentication requests?
which of these characteristics in common?
Controllers in a mobility group must all have which of these characteristics in common?
Which two attacks represent a social engineering attack?
Which two attacks represent a social engineering attack? (Choose two.)
Which of these statements best describes Cisco Centralized Key Management?
Which of these statements best describes Cisco Centralized Key Management?
Which two situations permit the Cisco WCS v7.0 to successfully trace a rogue to a switch port?
Which two situations permit the Cisco WCS v7.0 to successfully trace a rogue to a switch port?
(Choose two.)