Which two options are characteristics of Cisco collaboration cloud-based solutions?
Which two options are characteristics of Cisco collaboration cloud-based solutions?
(Choose two.)
What are the three main drivers for changing operations?
What are the three main drivers for changing operations? (Choose three.)
which way can Cisco partners benefit from offering a wide range of collaboration-related services?
Services are creating additional revenue. In which way can Cisco partners benefit from
offering a wide range of collaboration-related services?
Which building block of the business model references that KPI?
The customer satisfaction index is an important business Key Performance Indicator Which
building block of the business model references that KPI?
Which two entries define a valid storage option for the Cisco UCS C210 M2 TRC 1 server?
Which two entries define a valid storage option for the Cisco UCS C210 M2 TRC 1 server? (Choose
two.)
What are two common requirements of most tasks in business processes?
What are two common requirements of most tasks in business processes? (Choose two.)
Which two questions represent market trend complexities for considering a new collaboration experience?
Which two questions represent market trend complexities for considering a new
collaboration experience? (Choose two.)
What is the cause?
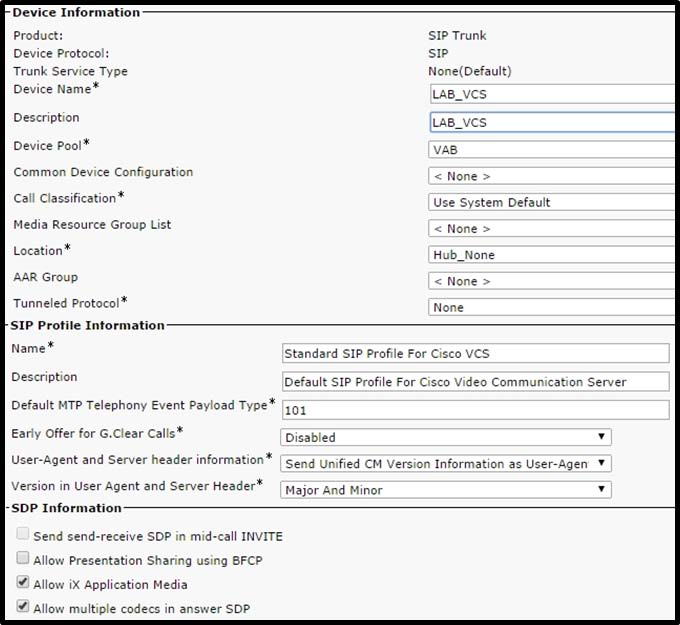
Refer to the exhibit. A network engineer configures a Cisco Unified Communications
Manager and VCS integration via a SIP trunk. Endpoint A is able to conduct video calls to
Endpoint B. When Endpoint A attempts to share presentation content with Endpoint B,
Endpoint B sees the presentation video on the main screen rather than on the presentation
display. What is the cause?
Which of the following is a reason why it is important to identify and collect business KPIs when designing th
Which of the following is a reason why it is important to identify and collect business KPIs
when designing the Cisco Collaboration Architecture?
Which statement correctly describes the relevance of security within a business process?
Which statement correctly describes the relevance of security within a business process?