Which of these is a reason for using groups to administer Agents?
Which of these is a reason for using groups to administer Agents?
which one allows the firewall to function as a Layer 2 bridge on the network?
For the following Cisco IOS Firewall features, which one allows the firewall to function as a Layer 2
bridge on the network?
What are the three steps in the auto-update configuration process?
What are the three steps in the auto-update configuration process? Choose three.
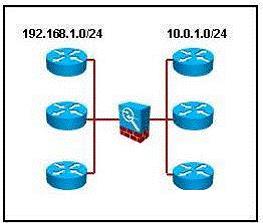
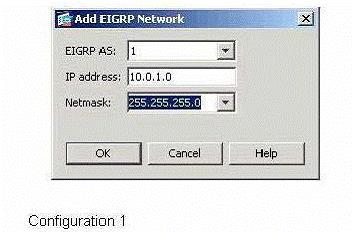
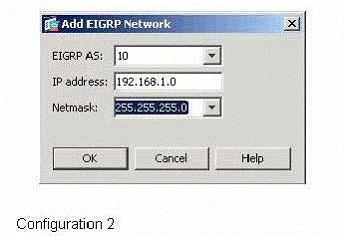
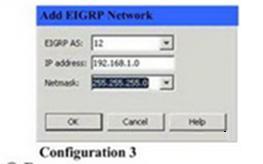
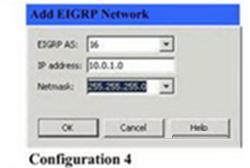
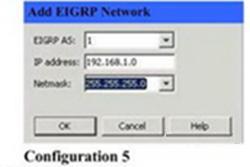
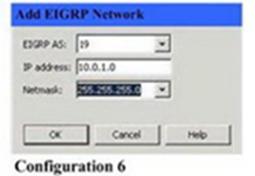
Which two Cisco ASDM configurations will add these networks to the configuration of EIGRP according to the inf
which of the following commands specifies that the IOS Firewall IDS engine drops packets and resets TCP connec
While logged into a Company router, which of the following commands specifies that the IOS
Firewall IDS engine drops packets and resets TCP connections for information signatures?
which operating system is the system API control rule available?
For which operating system is the system API control rule available?
Which statement best describes Cisco IOS Firewall URL-filtering services on Cisco IOS Release 12,4(15)T and la
Which statement best describes Cisco IOS Firewall URL-filtering services on Cisco IOS Release
12,4(15)T and later?
what does the Cisco VPN 3002 do with any existing backup server addresses in its configuration?
If the Cisco VPN Concentrator sends the Cisco VPN 3002 a backup server list, what does the
Cisco VPN 3002 do with any existing backup server addresses in its configuration?
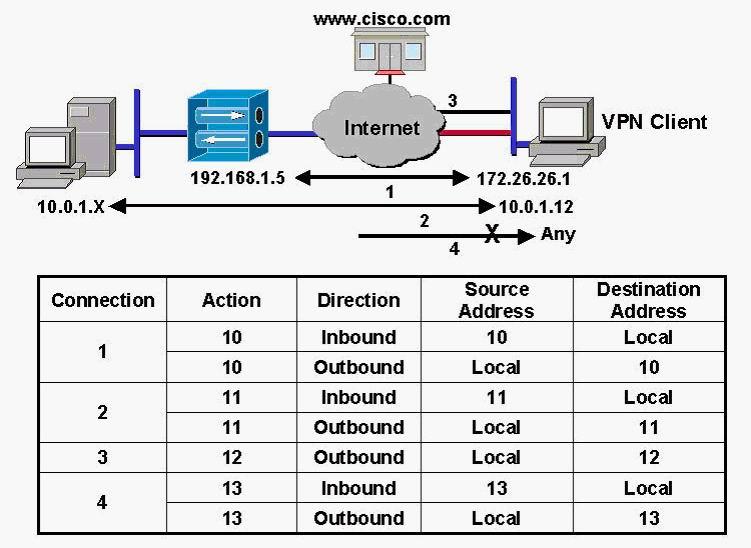
Select the correct action and destination address for this policy.
In the diagram, the firewall feature was enabled on the VPN Client. By clicking on the Firewall tab
of the VPN Client connection status window, you can view the VPN Client’s firewall policy for the
four connections, labeled 1 through 4 in the diagram. In the bottom half of the diagram,
Connection 3 displays the policy applied to traffic between the VPN Client and WWW. According
to the policy for connection 3, any local outbound traffic destined for destination address X will
have action Y applied to this traffic. Select the correct action and destination address for this
policy.
Which step is optional when configuring the crypto maps on the Firewalls?
You are creating a site-to-site VPN using IPSec between two PIX Firewalls. Which step is optional
when configuring the crypto maps on the Firewalls?