Which command could cause the CSC SSM to load a new software image from a remote TFTP server via the CLI?
Which command could cause the CSC SSM to load a new software image from a remote TFTP
server via the CLI?
Which is a design alternative in the SAFE SMR midsize network design campus module?
Which is a design alternative in the SAFE SMR midsize network design campus module?
Which two are necessary to take into consideration when preparing to tune your sensor?
Which two are necessary to take into consideration when preparing to tune your sensor? (Choose
two.)
Which two statements correctly describe configuring active/active failover?
Which two statements correctly describe configuring active/active failover? (Choose two.)
which security appliance attribute does not change?
During failover, which security appliance attribute does not change?
Which statement is true?
You are using multiple monitoring interfaces on a sensor appliance running software version 5.0.
Which statement is true?
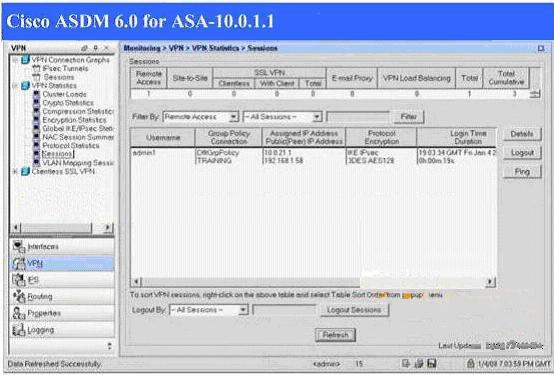
Which three pieces of information can be learned from the panel displayed in the exhibit?
Which sensor process is used to initiate the blocking response action?
Which sensor process is used to initiate the blocking response action?
which three commands need to be used?
Now, only the default modular policy framework is configured on your Cisco ASA. You wish to
prevent the dele and put FTP commands, but only on the outside interface. In order to achieve this
goal, which three commands need to be used? (Choose three.)
what series of VPN optimized routers?
The VPN acceleration module (VAM) is available on what series of VPN optimized routers?
Choose two.