Which Cisco product can provide endpoint-based trusted-traffic marking while implementing QoS?
Which Cisco product can provide endpoint-based trusted-traffic marking while implementing
QoS?
which tab in the Cisco IDM can you find the Custom Signature Wizard?
Under which tab in the Cisco IDM can you find the Custom Signature Wizard?
which additional security control can be used to force an attacker to compromise the exposed server before the
In multi-tier applications and multi-tier firewall designs, which additional security control can be
used to force an attacker to compromise the exposed server before the attacker attempts to
penetrate the more protected domains?
Please point out three technologies address ISO 17799 requirements for unauthorized access prevention.
You are the network consultant from Company.com. Please point out three technologies address
ISO 17799 requirements for unauthorized access prevention.
which IPsecprotected traffic could be forwarded?
While configuring a crypto map, which command will be used to specify the peer to which IPsecprotected traffic could be forwarded?
Which Cisco Catalyst Series switch feature can be used to integrate a tap-mode (promiscuous mode) IDS/IPS sens
Which Cisco Catalyst Series switch feature can be used to integrate a tap-mode (promiscuous
mode) IDS/IPS sensor into the network?
which two functions?
Cisco Security MARS and Cisco Security Manager could work together to implement which two
functions? (Choose two.)
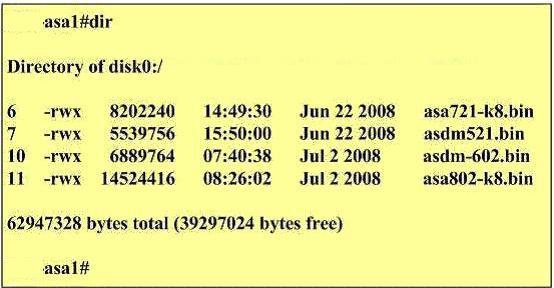
Which three commands can verify that the boot image is asa802-k8.bin according to the exhibit?
Which item is correct about the relationship between the VPN types and their descriptions?
Which item is correct about the relationship between the VPN types and their descriptions?
1. DMVPN
2. GET VPN
3. DGVPN
4. Dynamic VTI
5. Crypto maps
a. supported on Cisco IOS routers and ASAs
b. provides on-demand virtual access interface cloned from a virtual template configuration
c. combines two VPN technologies
d. provides tunnel-less any-to-any connectivity
e. supports routing protocol over VPN tunnels
What is the most appropriate sensor tuning for this scenario?
Your sensor is detecting a large volume of web traffic because it is monitoring traffic outside the
firewall. What is the most appropriate sensor tuning for this scenario?