What does the security appliance do with traffic from the partnernet?
You work as a network engineer, you are asked to examine the current Modular Policy Framework
configurations on the LA-ASA Adaptive Security Appliances using the Cisco Adaptive Security
Device Manager (ASDM) utility. You need to answer the multiple-choice questions in this
simulation by use of the appropriate Cisco ASDM configuration screens.
A host on the partnernet network attempts to access the public web server via HTTP. What does
the security appliance do with traffic from the partnernet?
What does the security appliance do with the traffic from the outside host?
You work as a network engineer, you are asked to examine the current Modular Policy Framework
configurations on the LA-ASA Adaptive Security Appliances using the Cisco Adaptive Security
Device Manager (ASDM) utility. You need to answer the multiple-choice questions in this
simulation by use of the appropriate Cisco ASDM configuration screens.
A host on the outside network sends e-mail to the public e-mail server. What does the security
appliance do with the traffic from the outside host?
What does the security appliance do with the VoIP traffic between host 172.20.1.15 and the host…?
You work as a network engineer, you are asked to examine the current Modular Policy Framework
configurations on the LA-ASA Adaptive Security Appliances using the Cisco Adaptive Security
Device Manager (ASDM) utility. You need to answer the multiple-choice questions in this
simulation by use of the appropriate Cisco ASDM configuration screens.
A host on the partnernet network makes a VoIP call to 172.20.1.15,which is statically mapped to
an IP phone on the inside network. What does the security appliance do with the VoIP traffic
between host 172.20.1.15 and the host on the partnernet network?
Which traffic does the security appliance inspect globally(regardless of the interface on…
You work as a network engineer, you are asked to examine the current Modular Policy Framework
configurations on the LA-ASA Adaptive Security Appliances using the Cisco Adaptive Security
Device Manager (ASDM) utility. You need to answer the multiple-choice questions in this
simulation by use of the appropriate Cisco ASDM configuration screens.
Which traffic does the security appliance inspect globally(regardless of the interface on which the
traffic enters the security appliance)?(Choose 3)
What does the security appliance do with the traffic from the partnernet host?
You work as a network engineer, you are asked to examine the current Modular Policy Framework
configurations on the LA-ASA Adaptive Security Appliances using the Cisco Adaptive Security
Device Manager (ASDM) utility. You need to answer the multiple-choice questions in this
simulation by use of the appropriate Cisco ASDM configuration screens.
A host on the partnernet network attempts to use FTP to download a file from InsideHost, which
resides on the inside interface of the security appliance. What does the security appliance do with
the traffic from the partnernet host?
Which three of these are encryption algorithms used by Cisco ASA security appliances?
Which three of these are encryption algorithms used by Cisco ASA security appliances? (Choose
three.)
Which of the following is not tuning parameters that affect the Cisco IPS Sensor globally?
Which of the following is not tuning parameters that affect the Cisco IPS Sensor globally?
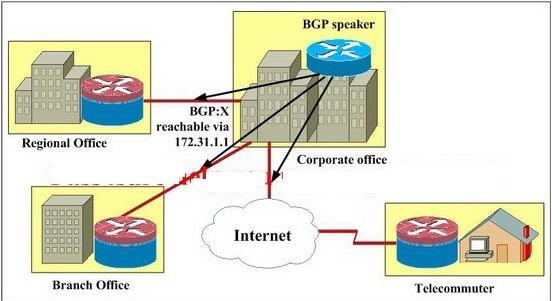
Which two methods will be adopted by the routers at the regional office, branch office, and telecommuter locat
You work as a network operator for an IT company. You have just detected a distributed DoS
attack which appears to have sources from many hosts in network X/24. You must take preventive
action to block all offending traffic, so you announce a BGP route, with the next-hop attribute of
172.31.1.1, for the X/24 network of the attacker. Which two methods will be adopted by the routers
at the regional office, branch office, and telecommuter location to prevent traffic going to and from
the attacker? (Choose two.)
Which three of these commands, used individually, would allow the administrator to place limits on the number
An administrator wants to protect a DMZ web server from SYN flood attacks. Which three of these
commands, used individually, would allow the administrator to place limits on the number of
embryonic connections? (Choose three.)
Which two protocols can be used for automatic signature anc service pack updates?
Which two protocols can be used for automatic signature anc service pack updates? (Choose two.