What are three steps of the Security Wheel?
What are three steps of the Security Wheel? Choose three.
What does the csd enable command enable on the Cisco ASA?
What does the csd enable command enable on the Cisco ASA?”
Which of these commands, when issued on the primary adaptive security appliance…?
The primary adaptive security appliance failed, so the secondary adaptive security appliance was
automatically activated. The network administrator then fixed the problem. Now the administrator
wants to return the primary to “active” status.
Which of these commands, when issued on the primary adaptive security appliance, will reactivate
the primary adaptive security appliance and restore it to “active” status?
What are three differences between inline and promiscuous sensor functionality?
What are three differences between inline and promiscuous sensor functionality?
(Choose three.)
Which method can be used by Cisco SSL VPN solution to provide connections between a Winsock2, TCP-based applic
Which method can be used by Cisco SSL VPN solution to provide connections between a
Winsock2, TCP-based application and a private site without requiring administrative privileges?
Which command will set the default route for an adaptive security appliance to the IP address 10.10.10.1?
Which command will set the default route for an adaptive security appliance to the IP address
10.10.10.1?
Which command provides a snapshot of the current internal state of a sensor service, enabling you to check the
Which command provides a snapshot of the current internal state of a sensor service, enabling
you to check the status of automatic upgrades and NTP?
which is used to protect the multi-tiered web application?
Which three tunneling protocols and methods are supported by the Cisco VPN Client?
Which three tunneling protocols and methods are supported by the Cisco VPN Client? (Choose
three.)
What does the security appliance do with the traffic from the host on the outside network?
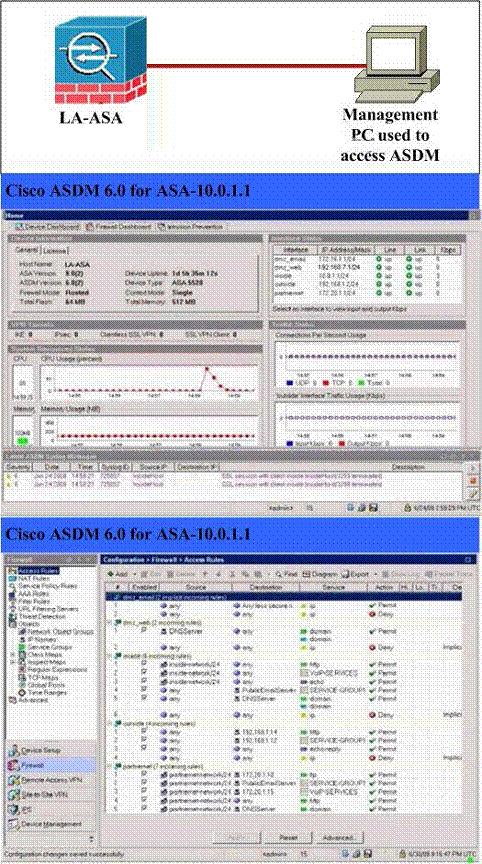
You work as a network engineer, you are asked to examine the current Modular Policy Framework
configurations on the LA-ASA Adaptive Security Appliances using the Cisco Adaptive Security
Device Manager (ASDM) utility. You need to answer the multiple-choice questions in this
simulation by use of the appropriate Cisco ASDM configuration screens.
A host on the outside network makes a VoIP call to a host on the inside network. What does the
security appliance do with the traffic from the host on the outside network?