Drag the five main security design components that should be addressed when implementing secure WAN solutions&
Please point out two requirements call for the deployment of 802.1X.
You are the network consultant from Your company. Please point out two requirements call for the
deployment of 802.1X.
Which OSPF configuration should the administrator enable to preent this kind of attack on the Router?
Open Shortest Path First (OSPF) is a dynamic routing protocol for use in Internet Protocol (IP)
networks. An OSPF router on the network is running at an abnormally high CPU rate. By use of
different OSPF debug commands on Router, the network administrator determines that router is
receiving many OSPF link state packets from an unknown OSPF neighbor, thus forcing many
OSPF path recalculations and affecting router’s CPU usage. Which OSPF configuration should the
administrator enable to preent this kind of attack on the Router?
Which one of the following Cisco Security Management products is able to perform (syslog) events normalization
Which one of the following Cisco Security Management products is able to perform (syslog) events
normalization?
which one of the following platforms has the highest IPSec throughput and can support the highest number of tu
Can you tell me which one of the following platforms has the highest IPSec throughput and can
support the highest number of tunnels?
Which method will always compute the password if it is made up of the character set you selected to test?
Which method will always compute the password if it is made up of the character set you selected
to test?
Which two methods can be used to perform IPSec peer authentication?
Which two methods can be used to perform IPSec peer authentication? (Choose two.)
What is the best way to mitigate the risk that executable-code exploits will perform malicious acts such as er
What is the best way to mitigate the risk that executable-code exploits will perform malicious acts
such as erasing your hard drive?
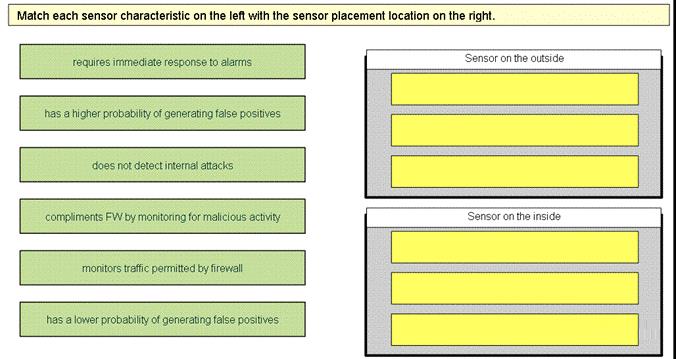
Match each sensor characteristic on the left with the sensor placement location on the right.
What are three functions of CSA in helping to secure customer environments?
Cisco Security Agent is the first endpoint security solution that combines zero-update attack
protection, data loss prevention and signature-based antivirus in a single agent. This unique blend
of capabilities defends servers and desktops against sophisticated day-zero attacks and enforces
acceptable-use and compliance policies within a simple management infrastructure. What are
three functions of CSA in helping to secure customer environments?