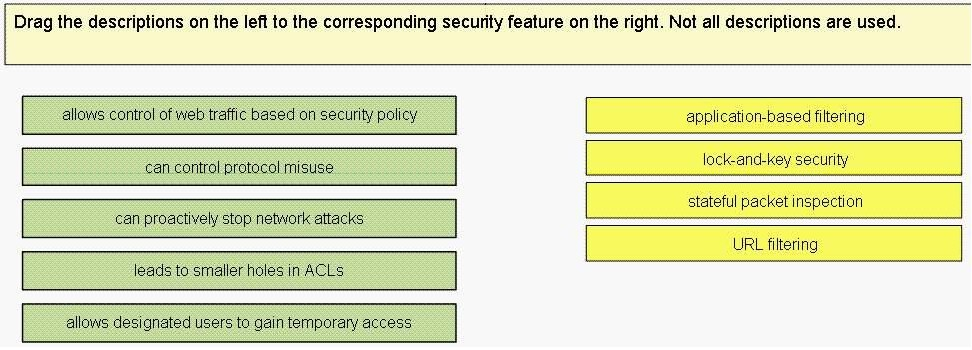
Match each IKE component to its supported option.
Match each IKE component to its supported option.
1. IKE authentication
2. IKE encryption
3. IKE data authentication/integrity
4. IKE key negotiation
(a) 3DES or AES
(b) MD5 or SHA-1
(c) pre-shared key or digital certificates
(d) DH Group 1,2,or5
Which three of these security products complement
Which three of these security products complement each other to achieve a secure e-banking
solution? (Choose three.)
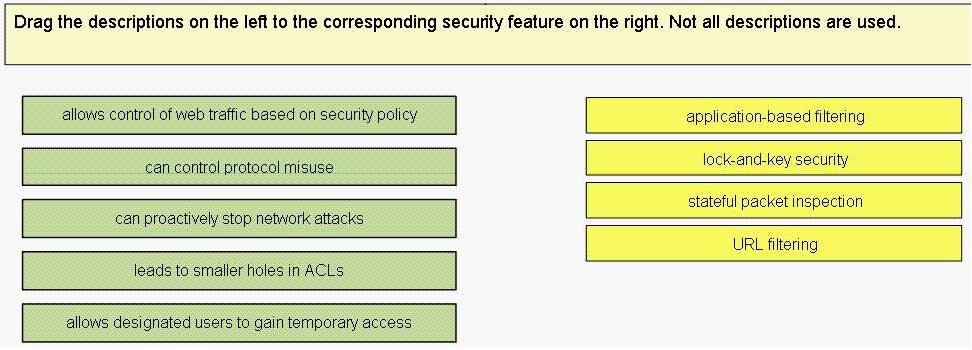
Match each IKE component to its supported option.
Match each IKE component to its supported option.
1. IKE authentication
2. IKE encryption
3. IKE data authentication/integrity
4. IKE key negotiation
(a) 3DES or AES
(b) MD5 or SHA-1
(c) pre-shared key or digital certificates
(d) DH Group 1,2,or5
Please point out three technologies address ISO 17799
You are the network consultant from Company.com. Please point out three technologies address
ISO 17799 requirements for unauthorized access prevention.
Which Cisco product can provide endpoint-based trusted-traffic marking while implementing QoS?
Which Cisco product can provide endpoint-based trusted-traffic marking while implementing
QoS?
can you tell me which one uses content scanning to identify sensitive content
Observe the following Cisco software agents carefully, can you tell me which one uses content scanning to identify sensitive content and controls the transfer of sensitive content off the local endpoint over removable storage, locally or network-attached hardware, or network applications?
Identify three components of the anti-X defense paillar. (Choose three.)
Your company wishes to adopt the Adaptive Threat Defense Architecture in their security policy.
Identify three components of the anti-X defense paillar. (Choose three.)
Which two of these statements describe features of the NAC Appliance architecture. (Choose two.)
Which two of these statements describe features of the NAC Appliance architecture. (Choose two.)