Start the simulator by clicking on the host computer?
SIMULATION
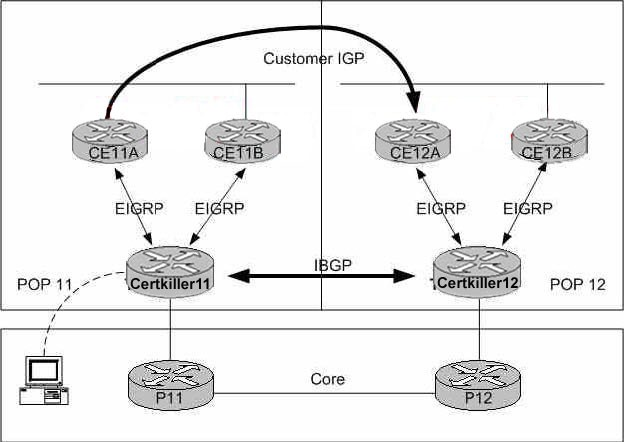
Network Topology Exhibit
You are a CCNA, CCNP and CCSP certified network technician at Certkiller .com. Indigo IT company is a client of Certkiller .com. Indigo IT company is a stock broker service that is using EIGRP AS 1 as the IGP in its network. Furthermore Indigo IT company has decided to establish connectivity between the two sites. For this Implementation Certkiller .com is using a MPLS VPN solution. Certkiller .com has already established MPLS connectivity between all of its PE routers. MPBGP connectivity has also been established on all Certkiller routers. Indigot IT company has successfully completed all necessary tasks on the CE routers, and Certkiller .com has successfully completed all necessary MPLS VPN configuration tasks on Certkiller 12. Your task is to successfully complete the implementation of the VPN connection by configuring the MPLS VPN on Certkiller 11 using the following information:
Privileged mode password: Certkiller
EIGRP is to be used the Certkiller -CE protocol for the VPN. MPBGP is being used to propagate VPN routing information between the Certkiller routers.
The interface supporting the Indigo Company is Serial0/0 and will have an IP address of 150.1.244.18 255.255.255.240.
The following has been assigned to Indigo’s VPN:
The VRP name is Customer_6
The RD is 6:10
The route target for import is 14:10.
The route target for export is 14:10.
Configure EIGRP between CE11A and Certkiller 11 using AS number 10. Redistribute from BGP to EIGRP AS 10 using metric string of 10000 100 255 1 1500.
Redistribute from EIGRP AS 10 to BGP using a metric of 1. VPN is operational when you can see routes for both the local (10.1.11.10) and the remote (10.1.12.0) sites in the VRF routing table.
Start the simulator by clicking on the host computer?
Which two settings must be configured in order to use the GUI to configure Call Admission Control with voice a
Which two settings must be configured in order to use the GUI to configure Call Admission Control with voice applications? (Choose two.)
Which distance setting should you use for the bridge configured as the root?
You are using standalone Cisco Aironet 1400 Series Wireless Bridges for a nine-mile point-to-point
wireless link between two buildings. Which distance setting should you use for the bridge configured as the
root?
DRAG DROP
DRAG DROP
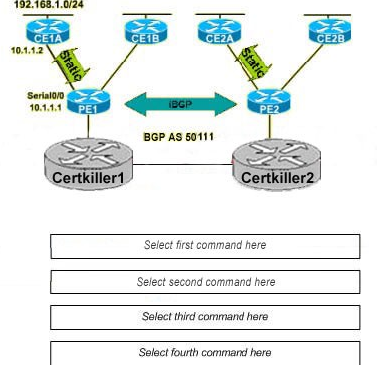
Exhibit:
CE1A and CE2A belong to the Certkiller _A VPN. Select the correct commands for the PE1 router to establish static routing from PE1 to the CE1A 192.168.1.0/24 network by selecting them below. Some of the commands must be entered in the correct order. Also enable propagation of the static route intp MP-iBGP. Assume the MP-iBGP session between PE1 and PE2 have been configured already.
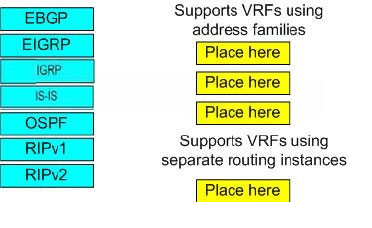
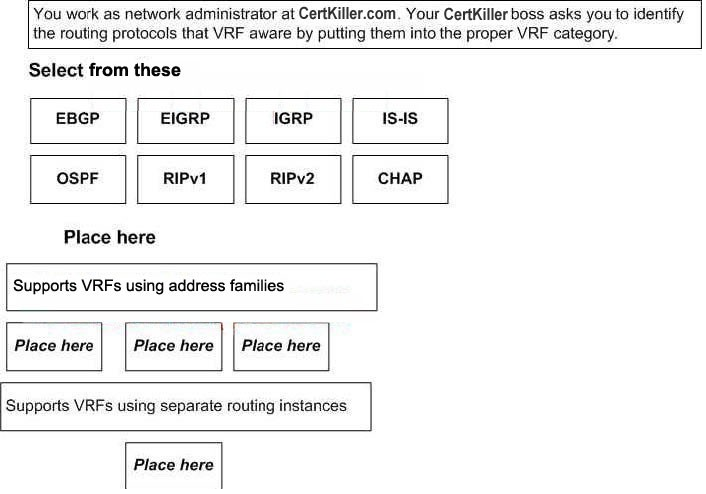
Identify the routing protocols on the left
DRAG DROP
Dragging and dropping them into the proper VRF category on the right?
Choose the service component in the optimize phase which assesses the WLAN
Choose the service component in the optimize phase which assesses the WLAN system and drives
continuous improvements by recommending remediation measures including device configuration
optimization, capacity planning, traffic analysis, security assessment, and quality issue resolution.
Which feature should you implement to detect a hacker
Which feature should you implement to detect a hacker invoking denial-of-service attacks, flooding the network with associations and probes, inserting rogue access points, and affecting network performance by attacking the quality of service?
SIMULATION
SIMULATION
Network topology exhibit:
Cisco Clean Access Manager Exhibit:
You work as a network engineer at Domain .com. Please study the topology exhibit carefully. Also examine the Cisco Clean Access Manager Exhibit. Domain .com has implemented a Cisco NAC Appliance solution. The internal server Certkiller C has been set up to provide HTTP and HTTPS services only. These services are only available for Domain .com internal users.
Your boss, Mrs. Certkiller, has asked you to provide the following configuration tasks:
* define a NAC Appliance IP-based traffic policy for the “Temporary Role”
* configure the policy so that it is able to access this remediation server over HTTP and HTTPS for clients on the 10.158.10.0, 255.255.255.0 subhet.
* after the configuration has been completed you must be able to launch the link to access the remediation server from the Certkiller B client computer.