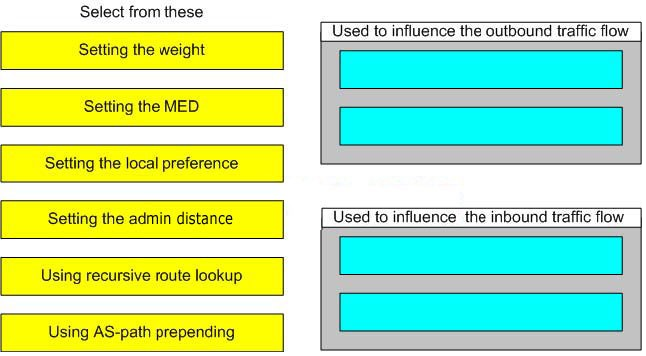
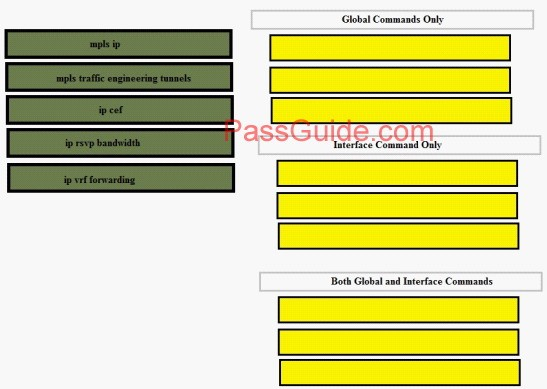
Drag the method used to influence BGP path selection on the left to the traffic flow it influences on the righ
List the BGP route selection steps in the correct order?
Select the best response.
If you know someone is trying to physically access your mesh access points deployed on a pole top in an area, which is the most appropriate alarm to check on the Cisco WCS? Select the best response.
Select the best response.
When using third-party antennas that provide a gain greater than +6 dBi for Context-Aware software, the difference in gain between the third-party antenna and the Cisco equivalent should not exceed which gain level, assuming a fixed power level? Select the best response.
which configuration command should be used if the internal routers
When the border routers in a transit autonomous system are to be configured, which configuration command should be used if the internal routers within the transit autonomous system have no IGP route to reach the router interface of the EBGP neighbor?
A well-designed IP addressing scheme supporting role-based functions within the subnet will result in the most
A well-designed IP addressing scheme supporting role-based functions within the subnet will result in the most efficient use of which technology?
How many IDSMs can be aggregated using a single EtherChannel in a highly available configuration?
How many IDSMs can be aggregated using a single EtherChannel in a highly available configuration?
How is the Cisco Compatible Extensions S36 message used in Cisco WLC v7.0?
How is the Cisco Compatible Extensions S36 message used in Cisco WLC v7.0?