A company just completed the rollout of IP/TV. The first inside network MC client to use the new feature claims they can not access the service. After re-viewing the above ASA Security appliance configuration and network diagram, the administrator was able to determine the following

A.
The igmp access-group command was not correct and should be changed.
B.
The access-list command was not correct and should be changed
C.
The igmp forward command should be changed to igmp forward interface inside and applied to interface Ethernet 2
D.
The ASA multicast configuration is correct, the configuration problem exists in the MC clients PC
Explanation:
ExplanationTCP/IP Access Lists
You can have up to 99 Standard IP Access Lists ranging in number from 1 to 99, the Extended IP Access Lists number range is assigned from 100 to 199. The most common use of the Extended IP access list to is create a packet filtering firewall. This is where you specify the allowed destinations of each packet from an allowed source.
UDP
access-list access-list-number [dynamic dynamic-name [timeout minutes]] {deny | permit} udp source source-wildcard [operator [port]] destination destination-wildcard [operator [port]]
[precedence precedence] [tos tos] [log | log-input]
[time-range time-range-name]
In all software releases, the access-list-number can be 101 to 199. In Cisco IOS Software Release 12.0.1, extended ACLs begin to use additional numbers (2000 to 2699). These additional numbers are referred to as expanded IP ACLs. Cisco IOS Software Release 11.2 added the ability to use list name in extended ACLs.
The value of 0.0.0.0/255.255.255.255 can be specified as any. After the ACL is defined, it must be applied to the interface (inbound or outbound). In early software releases, out was the default when a keyword out or in was not specified. The direction must be specified in later software releases.
interface
ip access-group {number|name} {in|out}
This extended ACL is used to permit traffic on the 10.1.1.x network (inside) and to receive ping responses from the outside while it prevents unsolicited pings from people outside, permitting all other traffic.
interface Ethernet0/1
ip address 172.16.1.2 255.255.255.0
ip access-group 101 in
access-list 101 deny icmp any 10.1.1.0 0.0.0.255 echo
access-list 101 permit ip any 10.1.1.0 0.0.0.255igmp access-group
To control the multicast groups that hosts on the subnet serviced by an interface can join, use the igmp access-group command in interface configuration mode. To disable groups on the interface, use the no form of this command.
igmp access-group acl
no igmp access-group acl


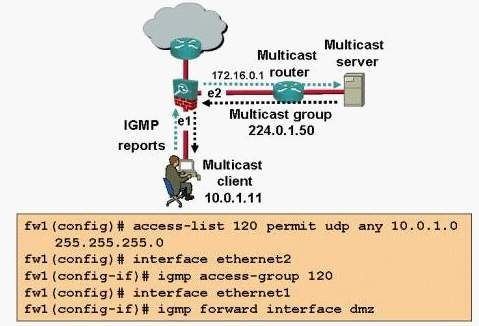
answer is supposed to be b (acl badly configured)
0
0
Simple answer is that the ACL is missing the extended keyword.
0
0