why is it important to properly define the topology?
For a dedicated DLP Gateway that runs in inline bridge mode, why is it important to properly
define the topology?
Which protocol is not supported for DLP?
Which protocol is not supported for DLP?
What happens when an Administrator activates the DLP Portal for Self Incident Handling and enters its fully qu
What happens when an Administrator activates the DLP Portal for Self Incident Handling and
enters its fully qualified domain name (DNS name)?
How can you achieve this?
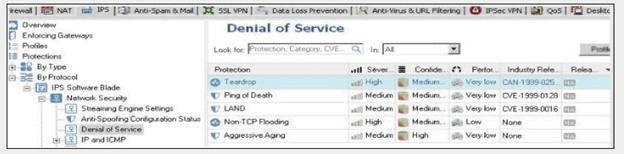
You just upgraded to R71 and are using the IPS Software Blade. You want to enable all critical
protections while keeping the rate of false positive very low. How can you achieve this?
Will you get all the information you need from these actions?
You enable Sweep Scan Protection and Host port scan in IPS to determine if a large amount of
traffic from a specific internal IP address is a network attack, or a user’s system is infected with a
worm. Will you get all the information you need from these actions?
which would be the best configuration to protect from a traffic hijack attempt?
You need to verify the effectiveness of your IPS configuration for your Web server farm. You have
a colleague run penetration tests to confirm that the Web servers are secure against traffic hijacks.
Of the following, which would be the best configuration to protect from a traffic hijack attempt?
How would you configure this in the IPS tab?
You need to determine if your company’s Web servers are accessed an excessive number of
times from the same host. How would you configure this in the IPS tab?
How would you characterize this attack tool?
Which application is used to create a File-Share Application?
Which application is used to create a File-Share Application?
Which procedure will create an Internal User?
Which procedure will create an Internal User?