Your network contains an Active Directory domain named contoso.com. The domain contains multiple servers
that run multiple applications.
Domain user accounts are used to authenticate access requests to the servers.
You plan to prevent NTLM from being used to authenticate to the servers.
You start to audit NTLM authentication events for the domain.
You need to view all of the NTLM authentication events and to identify which applications authenticate by using
NTLM.
On which computers should you review the event logs and which logs should you review?

A.
Computers on which to review the event logs: Only client computers
B.
Computers on which to review the event logs: Only domain controllers
C.
Computers on which to review the event logs: Only member servers
D.
Event logs to review: Applications and Services Logs\\Microsoft\\Windows\\Diagnostics-Networking
\\Operational
E.
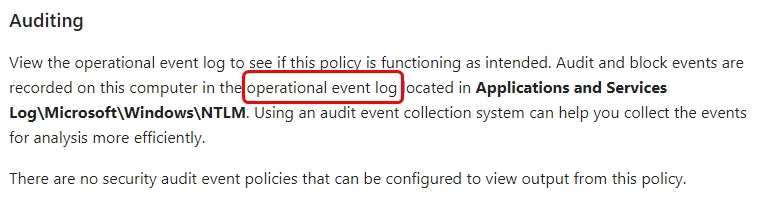
Event logs to review: Applications and Services Logs\\Microsoft\\Windows\\NTLM\\Operational
F.
Event logs to review: Applications and Services Logs\\Microsoft\\Windows\\SMBClient\\Security
G.
Event logs to review: Windows Logs\\Security
H.
Event logs to review: Windows Logs\\System
Explanation:
Do not confuse this with event ID 4776 recorded on domain controller’s security event log!!!
This question asks for implementing NTLM auditing when domain clients is connecting to member
servers! See below for further information.
https://docs.microsoft.com/en-us/windows/device-security/security-policy-settings/network-security-restrict-ntlmaudit-ntlm-authentication-in-this-domain
Via lab testing, most of the NTLM audit logs are created on Windows 10 clients, except that you use Windows
Server 2016 OS as clients (but this is unusual)


More 70-744 Exam Dumps PDF can be viewed at: https://drive.google.com/drive/folders/0B75b5xYLjSSNMDN6VjRLbFVKaWM?usp=sharing
0
0