Your network contains an Active Directory domain named contoso.com.
You are deploying Microsoft Advanced Threat Analytics (ATA) to the domain.
You install the ATA Gateway on a server named Server1.
To assist in detecting Pass-the-Hash attacks, you plan to configure ATA Gateway to collect events.
You need to configure the query filter for event subscriptions on Server1.
How should you configure the query filter?

A.
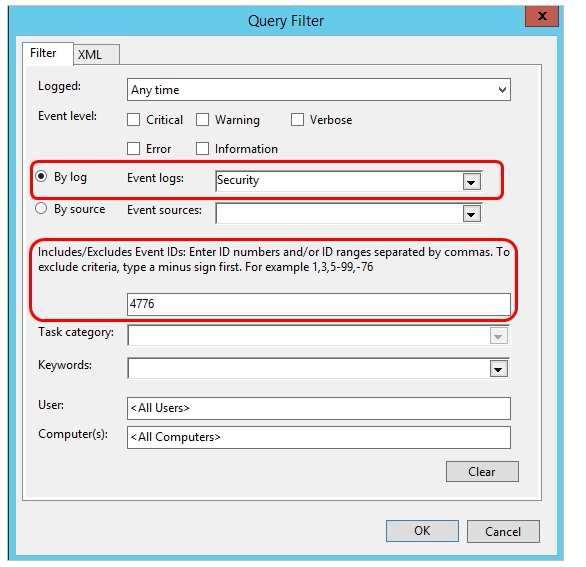
Event log to configure: Application
B.
Event log to configure: Directory Services
C.
Event log to configure: Security
D.
Event log to configure: System
E.
Event ID to include: 1000
F.
Event ID to include: 1009
G.
Event ID to include: 1025
H.
Event ID to include: 4776
I.
Event ID to include: 4997
Explanation:
https://docs.microsoft.com/en-us/advanced-threat-analytics/configure-event-collection
To enhance detection capabilities, ATA needs the following Windows events: 4776, 4732, 4733, 4728, 4729,
4756, 4757.These can either be read automatically by the ATA Lightweight Gateway or in case the ATA Lightweight
Gateway is not deployed,
it can be forwarded to the ATA Gateway in one of two ways, by configuring the ATA Gateway to listen for SIEM
events or by configuring Windows Event Forwarding.Event ID: 4776 NTLM authentication is being used against domain controller
Event ID: 4732 A User is Added to Security-Enabled DOMAIN LOCAL Group,
Event ID: 4733 A User is removed from Security-Enabled DOMAIN LOCAL Group
Event ID: 4728 A User is Added or Removed from Security-Enabled Global Group
Event ID: 4729 A User is Removed from Security-Enabled GLOBAL Group
Event ID: 4756 A User is Added or Removed From Security-Enabled Universal Group
Event ID: 4757 A User is Removed From Security-Enabled Universal Group


Is someone already take the exam ?
Do the questions correspond to the exam ?
0
0
New 70-744 Exam Questions Updated Today (4th/12/2017):
QUESTION
Note: This question b part of a series of questions that use the same or simitar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2016.
Server1 has a shared folder named Share1.
You need to ensure that all access to Share1 uses SMB Encryption.
Which tool should you use?
A. File Explorer
B. Shared Folders
C. Server Manager
D. Disk Management
E. Storage Explorer
F. Computer Management
G. System Configuration
H. File Server Resource Manager (FSRM)>
Answer: H
QUESTION
Your network contains an Active Directory forest named contoso.com.
The forest functional level is Windows Server 2012.
The forest contains a single domain.
The domain contains multiple Hyper-V hosts.
You plan to deploy guarded hosts.
You deploy a new server named Server22 to a workgroup.
You need to configure Server22 as a Host Guardian Service server.
What should you do before you initialize the Host Guardian Service on Server22?
A. Install the Active Directory Domain Services server role on Server22.
B. Obtain a certificate.
C. Raise the forest functional level.
D. Join Server22 to the domain.
Answer: D
QUESTION
Your network contains an Active Directory domain named contoso.com.
You create a Microsoft Operations Management Suite (OMS) workspace.
You need to connect several computers directly to the workspace.
Which two pieces of information do you require? Each correct answer presents part of the solution.
A. the ID of the workspace
B. the name of the workspace
C. the URL of the workspace
D. the key of the workspace
Answer: A
QUESTION
Note: This question b part of a series of questions that present the same scenario. Each question In the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear In the review screen.
Your network contains an Active Directory domain named contow.com. All servers run Windows Server 2016. All client computers run Windows 10.
The relevant objects in the domain are configured as shown in the following table.
You need to assign User1 the right to restore files and folders on Server1 and Server2.
Solution: You create a Group Policy object (GPO), link it to the Operations Users OU, and modify the Users Rights Assignment in the GPO.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION
Note: This question is part of a scries of questions that present the same scenario. Each question In the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question In this section, you will NOT be able to return to It. As a result, these questions will not appear In the review screen.
Your network contains an Active Directory domain named contoso.com. The domain contains mulbple Hyper-V hosts.
You need to deploy several critical line-of-business applications to the network; to meet the following requirements:
– The resources of the applications must be isolated from the physical host.
– Each application must be prevented from accessing the resources of the other applications.
– The configurations of the applications must be accessible only from the operating system that hosts the application.
Solution: You deploy a separate Windows container for each application.
Does this meet the goal?
A. Yes
B. No
Answer: A
QUESTION
Note: This question Is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2016.
Server1 has a volume named Volume1.
A central access policy named Policyl is deployed to the domain.
You need to apply Policyl to Volume1.
Which tool should you use?
A. File Explorer
B. Shared Folders
C. Server Manager
D. Disk Management
E. Storage Explorer
F. Computer Management
G. System Configuration
H. File Server Resource Manager (FSRM)
Answer: D
Explanation and more 70-744 Practice Questions can be checked here: https://drive.google.com/drive/folders/0B75b5xYLjSSNMDN6VjRLbFVKaWM?usp=sharing
0
1
has any one passed the the exam yet ? if so please email the dump u use mqbankai@gmail.com please
0
0
KK: New 70-744 Exam Questions Updated Today (4th/12/2017)
As I think, right answers are:
1. C
2. D
3. AD
4. B
5. A
6. A
0
0
Hi,
I need the 20744 trainerhandbook. Anyone share with me
Thanks
0
0
hello @ll,
can someone send me the dump? please? !!a.bandero@yahoo.com
Thank You,
0
0
I have latest questions and answer
mcsamcsa09568@gmail.com
1
0
hello, can someone send me latest dumps, please?
0
0
Could you please share your dumps me on below email address
sachi_puran22@gmail.com
0
0
Hi, I have latest dumps for 70-744, but it’s not free.
If you interesting buy 6 usd by paypal.
0
0
Could you please share your dumps me on below email address
0
0
Hello Kindom,
Did you recive new dump. Can you share it?
Thanks mate
0
0
Hi, I have latest dumps for 70-744, but it’s not free.
If you interesting buy 6 usd by paypal.
0
0
Hi, I have latest dumps for 70-744, but it’s not free.
If you interesting buy 6 usd by paypal.
0
0
Hi
Im intresting that
Can you mail me a.bandero@yahoo.com?
1
1
Anyone take this recently?
0
0