###BeginCaseStudy###
Case Study: 4
Scenario 4
Application Information
You are a database administrator for a manufacturing company.
You have an application that stores product data. The data will be converted to technical
diagrams for the manufacturing process.
The product details are stored in XML format. Each XML must contain only one product that
has a root element named Product. A schema named Production.ProductSchema has been
created for the products xml.
You develop a Microsoft .NET Framework assembly named ProcessProducts.dll that will be
used to convert the XML files to diagrams. The diagrams will be stored in the database as
images. ProcessProducts.dll contains one class named ProcessProduct that has a method
name of Convert(). ProcessProducts.dll was created by using a source code file named
ProcessProduct.es.
All of the files are located in C:\Products\.
The application has several performance and security issues.
You will create a new database named ProductsDB on a new server that has SQL Server
2012 installed. ProductsDB will support the application.
The following graphic shows the planned tables for ProductsDB:
You will also add a sequence named Production.ProductID_Seq.
You plan to create two certificates named DBCert and ProductsCert. You will create
ProductsCert in master. You will create DBCert in ProductsDB.
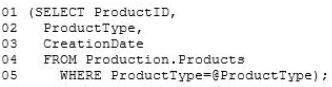
You have an application that executes dynamic T-SQL statements against ProductsDB. A
sample of the queries generated by the application appears in Dynamic.sql.
Application Requirements
The planned database has the following requirements:
• All stored procedures must be signed.
• The amount of disk space must be minimized.
• Administrative effort must be minimized at all times.
• The original product details must be stored in the database.
• An XML schema must be used to validate the product details.
• The assembly must be accessible by using T-SQL commands.
• A table-valued function will be created to search products by type.
• Backups must be protected by using the highest level of encryption.
• Dynamic T-SQL statements must be converted to stored procedures.
• Indexes must be optimized periodically based on their fragmentation.
• Manufacturing steps stored in the ManufacturingSteps table must refer to a product by
the sameidentifier used by the Products table.
ProductDetails_Insert.sql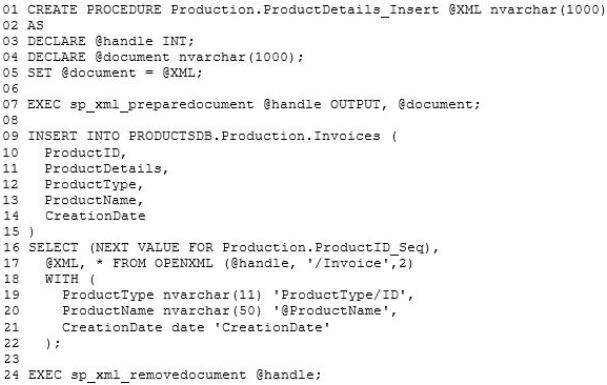
Product, xml
All product types are 11 digits. The first five digits of the product id reference the category of
the product and the remaining six digits are the subcategory of the product.
The following is a sample customer invoice in XML format: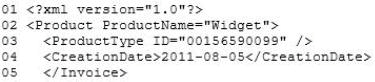
IndexManagement.sql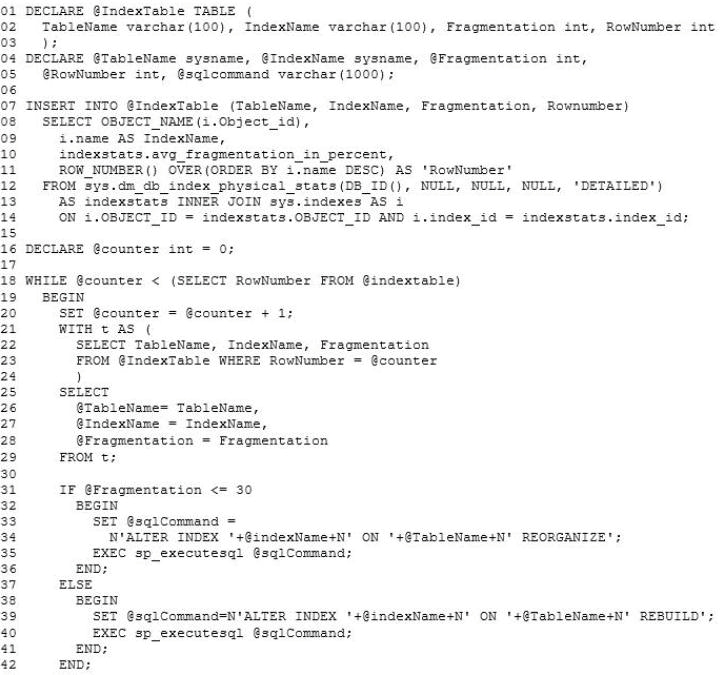
###EndCaseStudy###
An administrator provides a digital certificate named ServerCert.
You need to implement Transparent Data Encryption (TDE) on ProductsDB.
Which code segment should you use?

A.
USE PRODUCTSDB;
GO
CREATE DATABASE ENCRYPTION KEY WITH ALGORITHM = TRIPLE_DES_3KEY
ENCRYPTION BY SERVER CERTIFICATE DBCERT;
GO
ALTER DATABASE PRODUCTSDB SET ENCRYPTION ON;
GO
B.
USE PRODUCTSDB;
GO
CREATE DATABASE ENCRYPTION KEY WITH ALGORITHM = TRIPLE_DES_3KEY
ENCRYPTION BY SERVER CERTIFICATE PRODUCTSCERT;
GO
ALTER DATABASE PRODUCTSDB SET ENCRYPTION ON;
GO
C.
USE PRODUCTSDB;
GO
CREATE DATABASE ENCRYPTION KEY WITH ALGORITHM = AES_256
ENCRYPTION BY SERVER CERTIFICATE PRODUCTSCERT;
GO
ALTER DATABASE PRODUCTSDB SET ENCRYPTION ON;
GO
D.
USE PRODUCTSDB;
GO
CREATE DATABASE ENCRYPTION KEY WITH ALGORITHM = AES_256
ENCRYPTION BY SERVER CERTIFICATE DBCERT;
GO
ALTER DATABASE PRODUCTSDB SET ENCRYPTION ON;
GO
Explanation:
http://msdn.microsoft.com/en-us/library/bb934049.aspx




TDE performs real-time I/O encryption and decryption of the data and log files. The encryption uses a database encryption key (DEK), which is stored in the database boot record for availability during recovery. The DEK is a symmetric key secured by using a certificate stored in the master database of the server or an asymmetric key protected by an EKM module.
0
0
メーカーARENA アリーナ(株式会社デサント) 型番SAR 4106WJ 商品名タフスーツ ジュニア女子 スーパーストリーナ 素材タフスキンD(ポリエステル100) 素材説明タフスキンポリウレタンを含まないため、耐塩素性に優れます。 お洒落パーカー
http://www.L2n65q0tTX.com/L2n65q0tTX
0
0
Many thanks, this site is extremely practical.|
http://www.RNXjAvnzt9.com/RNXjAvnzt9
0
0