What is this technique called?
This IDS defeating technique works by splitting a datagram (or packet) into multiple fragments and the IDS will not spot the true nature of the fully assembled datagram. The datagram is not reassembled until it reaches its final destination. It would be a processor-intensive task for an IDS to reassemble all fragments itself, and on a busy system the packet will slip through the IDS onto the network.
What is this technique called?
How would you protect from these attacks?
Take a look at the following attack on a Web Server using obstructed URL:
http://www.example.com/script.ext?template=%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63 %2f%70%61%73%73%77%64
This request is made up of:
.%2e%2e%2f%2e%2e%2f%2e%2e%2f = ../../../
.%65%74%63 = etc
.%2f = /
.%70%61%73%73%77%64 = passwd
How would you protect from these attacks?
What tool has Gerald's attacker used to cover their tracks?
Gerald, the Systems Administrator for Hyped Enterprises, has just discovered that his network has been breached by an outside attacker.After performing routine maintenance on his servers, he discovers numerous remote tools were installed that no one claims to have knowledge of in his department.
Gerald logs onto the management console for his IDS and discovers an unknown IP address that scanned his network constantly for a week and was able to access his network through a high- level port that was not closed.Gerald traces the IP address he found in the IDS log to a proxy server in Brazil.
Gerald calls the company that owns the proxy server and after searching through their logs, they trace the source to another proxy server in Switzerland.Gerald calls the company in Switzerland that owns the proxy server and after scanning through the logs again, they trace the source back to a proxy server in China.
What tool has Gerald’s attacker used to cover their tracks?
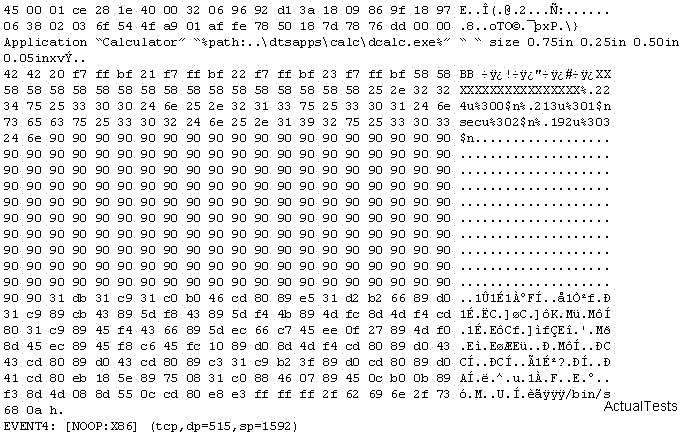
an analyst what would you conclude about the attack?
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack. You also notice “/bin/sh” in the ASCII part of the output. As an analyst what would you conclude about the attack?