Which statement is true regarding the packet flow on Cisco ASA firewall running version
8.2?

A.
For the packet that has been received on the ingress interface, ACL is only checked if
the connection entry exists for the packet flow.
B.
For the packet that has been received on the ingress interface, transaction rule is
checked before the ACL if the connection entry for the packet flow does not exist.
C.
For the packet that has been received on the egress interface, transaction rule is
checked before the ACL if the connection entry does not exist for the packet flow.
D.
For the packet that has been received on the ingress interface, ACL is only checked if
the connection entry does not exist for the packet flow.
Explanation:
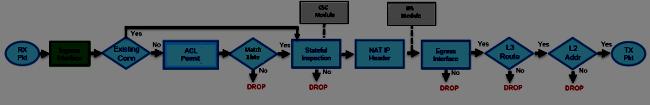
Here is a diagram of how the Cisco ASA processes the packet that it receives:Here are the individual steps in detail:
1. The packet is reached at the ingress interface.
2. Once the packet reaches the internal buffer of the interface, the input counter
of the interface is incremented by one.
3. Cisco ASA first looks at its internal connection table details in order to verify if
this is a current connection. If the packet flow matches a current connection,
then the Access Control List (ACL) check is bypassed and the packet is moved
forward.
If packet flow does not match a current connection, then the TCP state is verified. If it is
a SYN packet or UDP (User Datagram Protocol) packet, then the connection counter is
incremented by one and the packet is sent for an ACL check. If it is not a SYN packet, the
packet is dropped and the event is logged.
4. The packet is processed as per the interface ACLs. It is verified in sequential
order of the ACL entries and if it matches any of the ACL entries, it moves
forward. Otherwise, the packet is dropped and the information is logged. The
ACL hit count is incremented by one when the packet matches the ACL entry.
5. The packet is verified for the translation rules. If a packet passes through this
check, then a connection entry is created for this flow and the packet moves
forward. Otherwise, the packet is dropped and the information is logged.
6. The packet is subjected to an Inspection Check. This inspection verifies whether
or not this specific packet flow is in compliance with the protocol. Cisco ASA has
a built-in inspection engine that inspects each connection as per its pre-defined
set of application-level functionality. If it passed the inspection, it is moved
forward. Otherwise, the packet is dropped and the information is logged.
Additional security checks will be implemented if a Content Security (CSC) module is
involved.
7. The IP header information is translated as per the Network Address Translation/
Port Address Translation (NAT/PAT) rule and checksums are updated
accordingly. The packet is forwarded to Advanced Inspection and Prevention
Security Services Module (AIP-SSM) for IPS related security checks when the AIP
module is involved.8. The packet is forwarded to the egress interface based on the translation rules. If
no egress interface is specified in the translation rule, then the destination
interface is decided based on the global route lookup.
9. On the egress interface, the interface route lookup is performed. Remember,
the egress interface is determined by the translation rule that takes the priority.
10. Once a Layer 3 route has been found and the next hop identified, Layer 2
resolution is performed. The Layer 2 rewrite of the MAC header happens at this
stage.
11. The packet is transmitted on the wire, and interface counters increment on the
egress interface
“ASA 8.2: Packet Flow through an ASA Firewall”
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-nextgeneration-firewalls/113396-asa-packet-flow-00.html