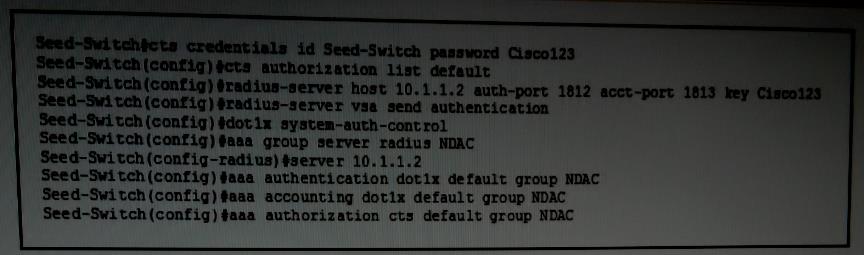
You have configured an NDAC seed switch as shown, but the switch is failing to allow
other switches to securely join the domain What command must you add to the seed
switch’s configuration to enable secure RADIUS communication?
Refer to the exhibit.

A.
Seed-Switch(config)#radius.server host 10.1.1.2 auth-port 1812 acct-port 1813
test username ndac-test pac key Cisco123
B.
Seed-Switch(config)#radius-server vsa send accounting
C.
Seed-Switch(config)#aaa preauth
D.
Seed-Switch(config)#no dot1x system-auth-control
E.
Seed-Switch(config)#radius-server host non-standard
F.
Seed-Switch(config)#aaa authentication dot1x default group local
Explanation:
http://www.cisco.com/c/en/us/td/docs/switches/lan/trustsec/configuration/guide/trustsec/ident-conn_config.html
Configuration Examples for Seed Device
Catalyst 6500 configured as a Cisco TrustSec seed device:
Router# cts credentials id Switch1 password Cisco123
Router# configure terminal
Router(config)# aaa new-model
Router(config)# aaa authentication dot1x default group radius
Router(config)# aaa authorization network MLIST group radius
Router(config)# cts authorization list MLIST
Router(config)# aaa accounting dot1x default start-stop group radiusRouter(config)# radius-server host 10.20.3.1 auth-port 1812 acct-port 1813 pac key
AbCe1234
Router(config)# radius-server vsa send authentication
Router(config)# dot1x system-auth-control
Router(config)# exit
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_cts/configuration/xe-
3e/sec-usr-cts-xe-3e-book/sec-cts-ndac.pdf
Example: Configuring AAA on Cisco TrustSec Seed Devices
Device> enable
Device# cts credentials id CTS-One password cisco123
Device# configure terminal
Device(config)# aaa new-model
Device(config)# aaa session-id common
Device(config)# radius server cts-aaa-server
Device(config-radius-server)# address ipv4 192.0.2.1 auth-port 1812 acct-port 1813
Device(config-radius-server)# pac key cisco123
Device(config-radius-server)# exit
Device(config)# radius-server vsa send authentication
Device(config)# aaa group server radius cts_sg
Device(config-sg-radius)# server name cts-aaa-server
Device(config-sg-radius)# exit
Device(config)# aaa authentication dot1x default group cts_sg
Device(config)# aaa authorization network default group cts_sg
Device(config)# aaa authorization network cts-mlist group cts_sg
Device(config)# cts authorization list cts-mlist
Device(config)# exit