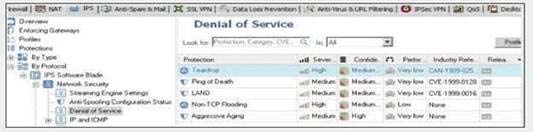
You are responsible for the IPS configuration of your Check Point firewall. Inside the Denial of service
section you need to set the protection parameters against the Teardrop attack tool with high
severity. How would you characterize this attack tool? Give the BEST answer.

A.
Hackers can send high volumes of non-TCP traffic in an effort to fill up a firewall State Table. This
results in a Denial of Service by preventing the firewall from accepting new connections. Teardrop is
a widely available attack tool that exploits this vulnerability.
B.
A remote attacker may attack a system by sending a specially crafted RPC request to execute
arbitrary code on a vulnerable system. Teardrop is a widely available attack tool that exploits this
vulnerability.
C.
Some implementations of TCP/IP are vulnerable to packets that are crafted in a particular way (a
SYN packet in which the source address and port are the same as the destination, i.e., spoofed).
Teardrop is a widely available attack tool that exploits this vulnerability
D.
Some implementations of the TCP/IP IP fragmentation re-assembly code do not properly handle
overlapping IP fragments. Sending two IP fragments, the latter entirely contained insidethe former,
causes the server to allocate too much memory and crash. Teardrop is a widely available attack tool
that exploits this vulnerability.