Which user account should you use?
Your network contains an Active Directory forest named adatum.com. The forest contains a
child domain named asia.adatum.com. The asia.adatum.com child domain contains a server
named DHCP1 that runs Windows Server 2012 R2.
You install the DHCP Server server role on DHCP1.
You have access to the administrative accounts shown in the following table.
You need to authorize DHCP1.
Which user account should you use?
You need to upgrade Server1 to Windows Server 2012 R2 with the graphical user interface (GUI)
You have a server named Server1 that has a Server Core installation of Windows Server
2008 R2.
Server1 has the DHCP Server server role and the File Server server role installed.
You need to upgrade Server1 to Windows Server 2012 R2 with the graphical user interface
(GUI).
The solution must meet the following requirements:
Preserve the server roles and their configurations.
Minimize administrative effort.
What should you do?
You need to ensure that when the users connect to Documents, they only see the files to which they have access
Your network contains an Active Directory domain named contoso.com. All servers run
Windows Server 2012 R2. The domain contains a member server named Server1. Server1
has the File and Storage Services server role installed.
On Server1, you create a share named Documents. The Documents share will contain the
files and folders of all users.
You need to ensure that when the users connect to Documents, they only see the files to
which they have access.
What should you do?
What should you identify?
You have a server named Server1 that runs a Server Core installation of Windows Server
2012 R2 Standard. You establish a Remote Desktop session to Server1.
You need to identify which task can be performed on Server1 from within the Remote
Desktop session.
What should you identify?
Which authentication method should you configure in the connection security rule?
You have a server named Server1. Server1 runs Windows Server 2012 R2 and is located in
a perimeter network.
You need to configure a custom connection security rule on Server1. The rule must encrypt
network communications across the Internet to a computer at another company.
Which authentication method should you configure in the connection security rule?
Which settings should you configure on VM1?
HOTSPOT
Your network contains two servers named Server1 and Server2 that run Windows Server
2012 R2. Server1 has the Hyper-V server role installed. Server2 has the Windows
Deployment Services server role installed.
On Server1, you have a virtual machine named VM1.
You plan to deploy an image to VM1 by using Windows Deployment Services (WDS).
You need to ensure that VM1 can connect to Server1 by using PXE.
Which settings should you configure on VM1?To answer, select the appropriate settings in
the answer area.
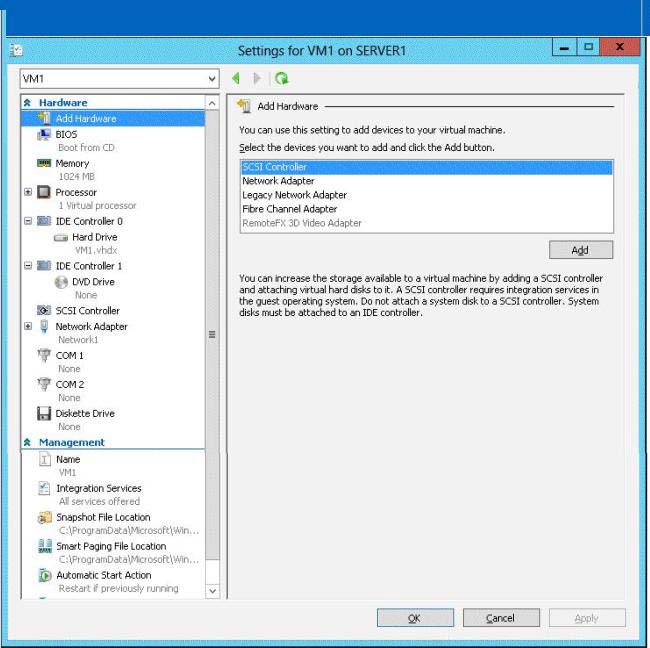
You need to add the RemoteFX 3D Video Adapter to VM1
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1. Server1 runs Windows Server 2012 R2 and has the
Hyper-V server role installed.
On Server1, you create a virtual machine named VM1.
When you try to add a RemoteFX 3D Video Adapter to VM1, you discover that the option is
unavailable as shown in the following exhibit. (Click the Exhibit button.)
You need to add the RemoteFX 3D Video Adapter to VM1.
What should you do first?
Which two actions should you perform?
Your network contains an Active Directory domain named contoso.com.
The domain contains 20 computer accounts in an organizational unit (OU) named OU1. A
user account named User1 is in an OU named OU2.
You are configuring a Group Policy object (GPO) named GPO1.
You need to assign User1 the Backup files and directories user right to all of the computer
accounts in OU1.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
Which three actions should you perform?
Your network contains an Active Directory domain named contoso.com. The domain
contains 500 servers that run Windows Server 2012 R2.
You have a written security policy that states the following:
Only required ports must be open on the servers.
All of the servers must have Windows Firewall enabled.
Client computers used by administrators must be allowed to access all of the ports on all of
the servers.
Client computers used by the administrators must be authenticated before the client
computers can access the servers.
You have a client computer named Computer1 that runs Windows 8.
You need to ensure that you can use Computer1 to access all of the ports on all of the
servers successfully. The solution must adhere to the security policy.
Which three actions should you perform? (Each correct answer presents part of the solution.
Choose three.)
You need to create a new starter GPO based on the settings in GPO1
Your network contains an Active Directory domain named contoso.com.
You have a starter Group Policy object (GPO) named GPO1 that contains more than 100
settings.
You need to create a new starter GPO based on the settings in GPO1.
You must achieve this goal by using the minimum amount of administrative effort.
What should you do?