What should you recommend?
###BeginCaseStudy###
Case Study: 10
Humongous Insurance
Scenario:
You are an enterprise desktop support technician for Humongous Insurance.
Active Directory Configuration
The company has two offices named Office1 and Office2.
The network contains an Active Directory forest named humongousinsurance.com. An
Active Directory site exists for each office. The sites are named Site1 and Site2.
Server Configuration
All servers run Windows Server 2008 R2 and are joined to the domain. The relevant servers
are configured as shown in the following table.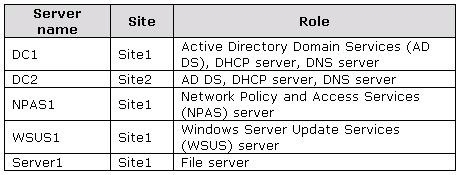
The corporate security policy states that all domain controllers must have only the following roles:
• AD DS
• DNS server
• DHCP server
Network Configuration
Site1 and Site2 connect to each other by using a WAN link.
Client Computer Configuration
All client computers run Windows 7 Enterprise and are members of the domain. Some client
computers are portable computers and some are desktop computers. The computers do not
support hardware virtualization.
All computers are configured to receive Windows Updates from WSUS1.
Remote Access Configuration
Users can connect to NPAS1 from the Internet by using all of the VPN protocols that are
supported by Windows Server 2008 R2.
Fabrikam, Inc. is a customer of Humongous Insurance. Several Humongous Insurance users
work at the Fabrikam office and access resources on the Humongous Insurance network by
using direct VPN connections to NPAS1. Fabrikam contains several wireless access points.
Application Configuration
All computers in the finance department run a custom application suite named App1.
Several users in the sales department install an application named App2. App2 runs as a
service and logs on by using the credentials of the user who installed the application.
###EndCaseStudy###
Each day, 100 users in Office2 download a 5-MB product catalog file from a share on Server1. The
network administrator reports that the downloads cause an excessive load on the WAN link between
Office1 and Office2. You need to recommend a solution to minimize WAN utilization. The solution
must not require that additional servers be deployed. What should you recommend?
What should you request?
###BeginCaseStudy###
Case Study: 10
Humongous Insurance
Scenario:
You are an enterprise desktop support technician for Humongous Insurance.
Active Directory Configuration
The company has two offices named Office1 and Office2.
The network contains an Active Directory forest named humongousinsurance.com. An
Active Directory site exists for each office. The sites are named Site1 and Site2.
Server Configuration
All servers run Windows Server 2008 R2 and are joined to the domain. The relevant servers
are configured as shown in the following table.
The corporate security policy states that all domain controllers must have only the following roles:
• AD DS
• DNS server
• DHCP server
Network Configuration
Site1 and Site2 connect to each other by using a WAN link.
Client Computer Configuration
All client computers run Windows 7 Enterprise and are members of the domain. Some client
computers are portable computers and some are desktop computers. The computers do not
support hardware virtualization.
All computers are configured to receive Windows Updates from WSUS1.
Remote Access Configuration
Users can connect to NPAS1 from the Internet by using all of the VPN protocols that are
supported by Windows Server 2008 R2.
Fabrikam, Inc. is a customer of Humongous Insurance. Several Humongous Insurance users
work at the Fabrikam office and access resources on the Humongous Insurance network by
using direct VPN connections to NPAS1. Fabrikam contains several wireless access points.
Application Configuration
All computers in the finance department run a custom application suite named App1.
Several users in the sales department install an application named App2. App2 runs as a
service and logs on by using the credentials of the user who installed the application.
###EndCaseStudy###
Humongous Insurance users who work at Fabrikam report that when they move between different
wireless networks, they are prompted to manually reconnect to the VPN. You need to ensure that
the users can automatically reconnect to the VPN when they move between wireless networks.
What should you request?
What should you recommend?
###BeginCaseStudy###
Case Study: 11
Baldwin Museum of Science Scenario:
You are an enterprise desktop support technician for the Baldwin Museum of Science. The
Baldwin Museum of Science is located in Dublin. The museum has 2,000 employees. All
employees have laptop computers that have cellular connections. The museum has a main
office and three satellite offices.
Active Directory Configuration
The network contains an Active Directory forest. The forest contains a domain named
Baldwinmuseumofscience.com. The relevant group policy information is shown in the following table.
Server Configuration
All servers are located in the main office and run Windows Server 2008 R2. The relevant
servers are configured as shown in the following table.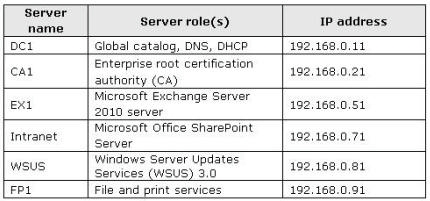
Users access the network remotely by using a DirectAccess connection.
Client Computer Information
All client computers run Windows 7 Enterprise (x86). The client computers are configured to
receive Windows Updates from http://WSUS.
Application Configuration
All users run Microsoft Office Outlook 2010 and use Outlook Anywhere. Users access the
intranet Web site by using the URL http://intranet.
The museum hosts several Web sites that use the domain suffix fineartschool.net.
Corporate Security Policy
The corporate security policy states that all updates on client computers must be installed
from the internal WSUS server.
###EndCaseStudy###
Users report that they can only access the fineartschool.net Web servers by entering the full URL to
the servers. You need to recommend a solution that allows users to access the Web servers by using
single label names. Your solution must ensure that users can access the intranet Web server by using
the URL http://intranet. What should you recommend?
What should you request?
###BeginCaseStudy###
Case Study: 11
Baldwin Museum of Science Scenario:
You are an enterprise desktop support technician for the Baldwin Museum of Science. The
Baldwin Museum of Science is located in Dublin. The museum has 2,000 employees. All
employees have laptop computers that have cellular connections. The museum has a main
office and three satellite offices.
Active Directory Configuration
The network contains an Active Directory forest. The forest contains a domain named
Baldwinmuseumofscience.com. The relevant group policy information is shown in the following table.
Server Configuration
All servers are located in the main office and run Windows Server 2008 R2. The relevant
servers are configured as shown in the following table.
Users access the network remotely by using a DirectAccess connection.
Client Computer Information
All client computers run Windows 7 Enterprise (x86). The client computers are configured to
receive Windows Updates from http://WSUS.
Application Configuration
All users run Microsoft Office Outlook 2010 and use Outlook Anywhere. Users access the
intranet Web site by using the URL http://intranet.
The museum hosts several Web sites that use the domain suffix fineartschool.net.
Corporate Security Policy
The corporate security policy states that all updates on client computers must be installed
from the internal WSUS server.
###EndCaseStudy###
A new printer is installed on FP1 and is shared as Printer1. Users report that they receive an error
when they try to connect to \\FP1\Printer1, and that after they click OK they are prompted for a
printer driver. The server administrator confirms that the printer is functioning correctly and that he
can print a test page. You need to ensure that users are able to connect to the new printer
successfully. Your solution must minimize administrative effort. What should you request?
What should you request?
###BeginCaseStudy###
Case Study: 11
Baldwin Museum of Science Scenario:
You are an enterprise desktop support technician for the Baldwin Museum of Science. The
Baldwin Museum of Science is located in Dublin. The museum has 2,000 employees. All
employees have laptop computers that have cellular connections. The museum has a main
office and three satellite offices.
Active Directory Configuration
The network contains an Active Directory forest. The forest contains a domain named
Baldwinmuseumofscience.com. The relevant group policy information is shown in the following table.
Server Configuration
All servers are located in the main office and run Windows Server 2008 R2. The relevant
servers are configured as shown in the following table.
Users access the network remotely by using a DirectAccess connection.
Client Computer Information
All client computers run Windows 7 Enterprise (x86). The client computers are configured to
receive Windows Updates from http://WSUS.
Application Configuration
All users run Microsoft Office Outlook 2010 and use Outlook Anywhere. Users access the
intranet Web site by using the URL http://intranet.
The museum hosts several Web sites that use the domain suffix fineartschool.net.
Corporate Security Policy
The corporate security policy states that all updates on client computers must be installed
from the internal WSUS server.
###EndCaseStudy###
Twenty new laptop computers are joined to the domain. Users of the new laptops report that they
can access the Exchange server, but they cannot access file shares or internal Web sites when they
are outside of the office. Other remote users can access file shares and internal Web sites when they
are outside of the office. You need to ensure that users of the new laptops can access file shares and
Web sites on the internal network when they are outside of the office. What should you request?
What should you request?
###BeginCaseStudy###
Case Study: 11
Baldwin Museum of Science Scenario:
You are an enterprise desktop support technician for the Baldwin Museum of Science. The
Baldwin Museum of Science is located in Dublin. The museum has 2,000 employees. All
employees have laptop computers that have cellular connections. The museum has a main
office and three satellite offices.
Active Directory Configuration
The network contains an Active Directory forest. The forest contains a domain named
Baldwinmuseumofscience.com. The relevant group policy information is shown in the following table.
Server Configuration
All servers are located in the main office and run Windows Server 2008 R2. The relevant
servers are configured as shown in the following table.
Users access the network remotely by using a DirectAccess connection.
Client Computer Information
All client computers run Windows 7 Enterprise (x86). The client computers are configured to
receive Windows Updates from http://WSUS.
Application Configuration
All users run Microsoft Office Outlook 2010 and use Outlook Anywhere. Users access the
intranet Web site by using the URL http://intranet.
The museum hosts several Web sites that use the domain suffix fineartschool.net.
Corporate Security Policy
The corporate security policy states that all updates on client computers must be installed
from the internal WSUS server.
###EndCaseStudy###
The help desk technicians discover that Windows Defender definitions are not up-to-date on client
computers. The help desk technicians report that other critical updates are applied to the client
computers. You need to ensure that all client computers have the latest Windows Defender
definitions. Your solution must comply with the corporate security policy. What should you request?
What should you request?
###BeginCaseStudy###
Case Study: 11
Baldwin Museum of Science Scenario:
You are an enterprise desktop support technician for the Baldwin Museum of Science. The
Baldwin Museum of Science is located in Dublin. The museum has 2,000 employees. All
employees have laptop computers that have cellular connections. The museum has a main
office and three satellite offices.
Active Directory Configuration
The network contains an Active Directory forest. The forest contains a domain named
Baldwinmuseumofscience.com. The relevant group policy information is shown in the following table.
Server Configuration
All servers are located in the main office and run Windows Server 2008 R2. The relevant
servers are configured as shown in the following table.
Users access the network remotely by using a DirectAccess connection.
Client Computer Information
All client computers run Windows 7 Enterprise (x86). The client computers are configured to
receive Windows Updates from http://WSUS.
Application Configuration
All users run Microsoft Office Outlook 2010 and use Outlook Anywhere. Users access the
intranet Web site by using the URL http://intranet.
The museum hosts several Web sites that use the domain suffix fineartschool.net.
Corporate Security Policy
The corporate security policy states that all updates on client computers must be installed
from the internal WSUS server.
###EndCaseStudy###
The help desk technicians discover that some computers have not installed the latest updates for
Windows. The Windows Update log files on the computers show that to complete the installation of
several updates the computers must be restarted. You need to ensure that future updates are
successfully installed on all computers. What should you request?
What should you recommend that the users do?
###BeginCaseStudy###
Case Study: 12
Tailspin Toys
Scenario:
Background
You are the desktop support technician for Tailspin Toys. Tailspin Toys manufacturers and
distributes children’s toys. The network environment includes a server infrastructure running
on Windows Server 2003 Service Pack (SP) 2 and Windows Server 2008 R2, Active
Directory with the forest and domain levels set at Windows Server 2003, and Active
Directory Certificate Services (AD CS) running on Windows Server 2008 R2. The company
has a Microsoft Enterprise Agreement (EA) with Software Assurance (SA). The company
sites, network connectivity, and site technologies are shown in the following table.
The company’s domain controller layout and details are shown in the following table.
The company’s client computer configuration details are shown in the following table.
The company uses Microsoft SharePoint 2010 as the company intranet and as a document
repository for company-related Microsoft Office documents. The URL for the intranet is
intranet.tailspintoys.com. There is a Group Policy object (GPO) that applies to all client
computers that allows employees who are connected to the corporate network to go to the
intranet site without having to enter authentication information.
All users are using Microsoft Internet Explorer 8. All users have enabled the Internet
Explorer SmartScreen Filter and the Internet Explorer phishing filter. All of the desktop
support technicians are members of a security group named Desktop Admins. The Desktop
Admins group is a member of the local Administrators group on all client computers. The
desktop support technicians use the Microsoft Diagnostics and Recovery Toolset to perform
various troubleshooting and repairs.
All Windows 7 client computers have a directory named tailspintoys\scripts in the root of the
operating system drive. The directory contains four unique .vbs files named scriptl.vbs,
script2.vbs, script3.vbs, and script4.vbs.
Software Environment
• An existing GPO named AppLockdown applies to Windows 7 machines and uses
AppLocker to ensure that:
No .bat files are allowed to be run by users and rules are enforced
• An existing GPO named RestrictApps applies to Windows XP client computers and
uses a Software Restriction Policy to ensure that:
No .bat files are allowed to be run by users and rules are enforced
Data Protection Environment
• Some users at the Manufacturing site use EFS to encrypt data.
• A user account named EFSAdmin has been designated as the Data Recovery Agent
(DRA).
• The DRA certificate and private key are stored on a portable USB hard drive.
As part of the yearly security compliance audits, a vendor is due to arrive at Tailspin Toys in
a month to perform the yearly audit. To prepare for the audit, management has asked you to
participate in an internal review of the company’s existing security configurations related to
network security and data security. The management team has issued the following
requirements:
New software requirements
• All installation programs must be digitally signed.
• Minimum permissions must be granted for installation of programs.
Internet Explorer requirements
• Users must not be able to bypass certificate warnings.
• Users must not be able to add Internet Explorer add-ons unless the add-ons are
approved by IT.
Data protection requirements
• All portable storage devices must use a data encryption technology. The solution must
meet the following requirements:
Allow all users a minimum of read access to the encrypted data while working from their
company client computers.
Encrypt entire contents of portable storage devices.
Minimize administrative overhead for users as files and folders are added to the portable
storage devices.
• Recovery information for client computer hard drives must be centrally stored and
protected with data encryption.
###EndCaseStudy###
Users at the Manufacturing site must have a secondary method of decrypting their existing files if
they lose access to their certificate and private key or if the EFS Admin’s certificate is not available.
You need to recommend a solution to ensure that a secondary method is available to users. The
solution must not require accessing or altering the existing encrypted files before decrypting them.
What should you recommend that the users do?
What should you recommend?
###BeginCaseStudy###
Case Study: 12
Tailspin Toys
Scenario:
Background
You are the desktop support technician for Tailspin Toys. Tailspin Toys manufacturers and
distributes children’s toys. The network environment includes a server infrastructure running
on Windows Server 2003 Service Pack (SP) 2 and Windows Server 2008 R2, Active
Directory with the forest and domain levels set at Windows Server 2003, and Active
Directory Certificate Services (AD CS) running on Windows Server 2008 R2. The company
has a Microsoft Enterprise Agreement (EA) with Software Assurance (SA). The company
sites, network connectivity, and site technologies are shown in the following table.
The company’s domain controller layout and details are shown in the following table.
The company’s client computer configuration details are shown in the following table.
The company uses Microsoft SharePoint 2010 as the company intranet and as a document
repository for company-related Microsoft Office documents. The URL for the intranet is
intranet.tailspintoys.com. There is a Group Policy object (GPO) that applies to all client
computers that allows employees who are connected to the corporate network to go to the
intranet site without having to enter authentication information.
All users are using Microsoft Internet Explorer 8. All users have enabled the Internet
Explorer SmartScreen Filter and the Internet Explorer phishing filter. All of the desktop
support technicians are members of a security group named Desktop Admins. The Desktop
Admins group is a member of the local Administrators group on all client computers. The
desktop support technicians use the Microsoft Diagnostics and Recovery Toolset to perform
various troubleshooting and repairs.
All Windows 7 client computers have a directory named tailspintoys\scripts in the root of the
operating system drive. The directory contains four unique .vbs files named scriptl.vbs,
script2.vbs, script3.vbs, and script4.vbs.
Software Environment
• An existing GPO named AppLockdown applies to Windows 7 machines and uses
AppLocker to ensure that:
No .bat files are allowed to be run by users and rules are enforced
• An existing GPO named RestrictApps applies to Windows XP client computers and
uses a Software Restriction Policy to ensure that:
No .bat files are allowed to be run by users and rules are enforced
Data Protection Environment
• Some users at the Manufacturing site use EFS to encrypt data.
• A user account named EFSAdmin has been designated as the Data Recovery Agent
(DRA).
• The DRA certificate and private key are stored on a portable USB hard drive.
As part of the yearly security compliance audits, a vendor is due to arrive at Tailspin Toys in
a month to perform the yearly audit. To prepare for the audit, management has asked you to
participate in an internal review of the company’s existing security configurations related to
network security and data security. The management team has issued the following
requirements:
New software requirements
• All installation programs must be digitally signed.
• Minimum permissions must be granted for installation of programs.
Internet Explorer requirements
• Users must not be able to bypass certificate warnings.
• Users must not be able to add Internet Explorer add-ons unless the add-ons are
approved by IT.
Data protection requirements
• All portable storage devices must use a data encryption technology. The solution must
meet the following requirements:
Allow all users a minimum of read access to the encrypted data while working from their
company client computers.
Encrypt entire contents of portable storage devices.
Minimize administrative overhead for users as files and folders are added to the portable
storage devices.
• Recovery information for client computer hard drives must be centrally stored and
protected with data encryption.
###EndCaseStudy###
You need to recommend a solution to back up BitLocker recovery information based on the
company’s existing data protection requirements. The solution must include the backup destination
and the solution prerequisites. What should you recommend? (Choose all that apply.)
Which service should you start on LAPTOP01?
###BeginCaseStudy###
Case Study: 12
Tailspin Toys
Scenario:
Background
You are the desktop support technician for Tailspin Toys. Tailspin Toys manufacturers and
distributes children’s toys. The network environment includes a server infrastructure running
on Windows Server 2003 Service Pack (SP) 2 and Windows Server 2008 R2, Active
Directory with the forest and domain levels set at Windows Server 2003, and Active
Directory Certificate Services (AD CS) running on Windows Server 2008 R2. The company
has a Microsoft Enterprise Agreement (EA) with Software Assurance (SA). The company
sites, network connectivity, and site technologies are shown in the following table.
The company’s domain controller layout and details are shown in the following table.
The company’s client computer configuration details are shown in the following table.
The company uses Microsoft SharePoint 2010 as the company intranet and as a document
repository for company-related Microsoft Office documents. The URL for the intranet is
intranet.tailspintoys.com. There is a Group Policy object (GPO) that applies to all client
computers that allows employees who are connected to the corporate network to go to the
intranet site without having to enter authentication information.
All users are using Microsoft Internet Explorer 8. All users have enabled the Internet
Explorer SmartScreen Filter and the Internet Explorer phishing filter. All of the desktop
support technicians are members of a security group named Desktop Admins. The Desktop
Admins group is a member of the local Administrators group on all client computers. The
desktop support technicians use the Microsoft Diagnostics and Recovery Toolset to perform
various troubleshooting and repairs.
All Windows 7 client computers have a directory named tailspintoys\scripts in the root of the
operating system drive. The directory contains four unique .vbs files named scriptl.vbs,
script2.vbs, script3.vbs, and script4.vbs.
Software Environment
• An existing GPO named AppLockdown applies to Windows 7 machines and uses
AppLocker to ensure that:
No .bat files are allowed to be run by users and rules are enforced
• An existing GPO named RestrictApps applies to Windows XP client computers and
uses a Software Restriction Policy to ensure that:
No .bat files are allowed to be run by users and rules are enforced
Data Protection Environment
• Some users at the Manufacturing site use EFS to encrypt data.
• A user account named EFSAdmin has been designated as the Data Recovery Agent
(DRA).
• The DRA certificate and private key are stored on a portable USB hard drive.
As part of the yearly security compliance audits, a vendor is due to arrive at Tailspin Toys in
a month to perform the yearly audit. To prepare for the audit, management has asked you to
participate in an internal review of the company’s existing security configurations related to
network security and data security. The management team has issued the following
requirements:
New software requirements
• All installation programs must be digitally signed.
• Minimum permissions must be granted for installation of programs.
Internet Explorer requirements
• Users must not be able to bypass certificate warnings.
• Users must not be able to add Internet Explorer add-ons unless the add-ons are
approved by IT.
Data protection requirements
• All portable storage devices must use a data encryption technology. The solution must
meet the following requirements:
Allow all users a minimum of read access to the encrypted data while working from their
company client computers.
Encrypt entire contents of portable storage devices.
Minimize administrative overhead for users as files and folders are added to the portable
storage devices.
• Recovery information for client computer hard drives must be centrally stored and
protected with data encryption.
###EndCaseStudy###
A user at the Headquarters site is able to run .bat files on LAPTOP01. However, you notice that the
AppLockdown GPO was successfully applied to the computer. You need to ensure that the user’s
computer complies with the existing AppLockdown GPO settings. Which service should you start on
LAPTOP01?

