Which four actions should you perform in sequence?
###BeginCaseStudy###
Topic 3, Northwind Traders
Overview
Northwind Traders is an IT services and hosting provider.
Northwind Traders has two main data centers in North America. The data centers are located in the
same city. The data centers connect to each other by using high-bandwidth, low-latency WAN links. Each
data center connects directly to the Internet.
Northwind Traders also has a remote office in Asia that connects to both of the North American data
centers by using a WAN link. The Asian office has 30 multipurpose servers.
Each North American data center contains two separate network segments. One network segment is
used to host the internal servers of Northwind Traders. The other network segment is used for the
hosted customer environments.
Existing EnvironmentActive Directory
The network contains an Active Directory forest named northwindtraders.com. The forest contains a
single domain. All servers run Windows Server 2012 R2.
Server Environment
The network has the following technologies deployed:
Service Provider Foundation
Windows Azure Pack for Windows Server
System Center 2012 R2 Virtual Machine Manager (VMM)
An Active Directory Rights Management Services (AD RMS) cluster
An Active Directory Certificate Services (AD CS) enterprise certification authority (CA)
All newly deployed servers will include the following components:
Dual 10-GbE Remote Direct Memory Access (RDMA)-capable network adapters
Dual 1-GbE network adapters
128 GB of RAM
Requirements
Business Goals
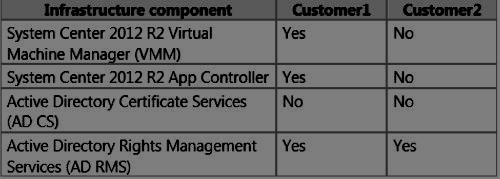
Northwind Traders will provide hosting services to two customers named Customer1 and Customer2.
The network of each customer is configured as shown in the following table.
Planned Changes
Northwind Traders plans to implement the following changes:
Deploy System Center 2012 R2 Operations Manager.
Deploy Windows Server 2012 R2 iSCSI and SMB-based storage.
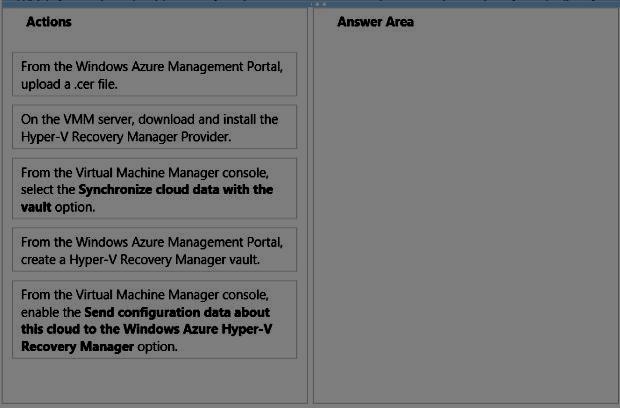
Implement Hyper-V Recovery Manager to protect virtual machines.
Deploy a certificate revocation list (CRL) distribution point (CDP) on the internal network.
For Customer 1, install server authentication certificates issued by the CA of Northwind Traders
on the virtual machine in the hosting networks.General Requirements
Northwind Traders identifies the following requirements:
Storage traffic must use dedicated adapters.
All storage and network traffic must be load balanced.
The amount of network traffic between the internal network and the hosting network must be
minimized.
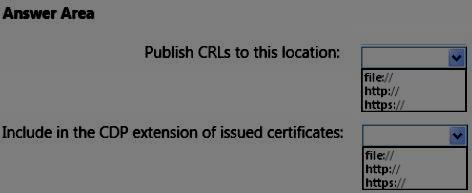
The publication of CRLs to CDPs must be automatic.
Each customer must use dedicated Hyper-V hosts.
Administrative effort must be minimized, whenever possible.
All servers and networks must be monitored by using Operations Manager.
Anonymous access to internal file shares from the hosting network must be prohibited.
All Hyper-V hosts must use Cluster Shared Volume (CSV) shared storage to host virtual
machines.
All Hyper-V storage and network traffic must remain available if single network adapter fails.
The Hyper-V hosts connected to the SMB-based storage must be able to make use of the
RDMA technology.
The number of servers and ports in the hosting environment to which the customer has access
must be minimized.
Customer1 Requirements
Northwind Traders identifies the following requirements for Customer1:
Customer1 must use SMB-based storage exclusively.
Customer1 must use App Controller to manage hosted virtual machines.
The virtual machines of Customer1 must be recoverable if a single data center fails.
Customer1 must be able to delegate self-service roles in its hosted environment to its users.
Customer1 must be able to check for the revocation of certificates issued by the CA of
Northwind Traders.
The users of Customer1 must be able to obtain use licenses for documents protected by the AD
RMS of Northwind Traders.
Certificates issued to the virtual machines of Customer1 that reside on the hosted networks
must be renewed automatically.
Customer2 Requirements
Northwind Traders identifies the following requirements for Customer2:
Customer2 must use iSCSI-based storage exclusively.
All of the virtual machines of Customer2 must be migrated by using a SAN transfer.
None of the metadata from the virtual machines of Customer2 must be stored in Windows
Azure.
The network configuration of the Hyper-V hosts for Customer2 must be controlled by using
logical switches. The only VMM network port profiles and classifications allowed by Customer2 must be lowbandwidth, medium-bandwidth, or high-bandwidth.
The users at Northwind Traders must be able to obtain use licenses for documents protected
by the AD RMS cluster of Customer2. Customer2 plans to decommission its AD RMS cluster
during the next year.
###EndCaseStudy###
DRAG DROP
You need to implement a Hyper-V Recovery Manager solution in the hosting environment of Northwind
Traders.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the
list of actions to the answer area and arrange them in the correct order.
What should you recommend?
###BeginCaseStudy###
Topic 3, Northwind Traders
Overview
Northwind Traders is an IT services and hosting provider.
Northwind Traders has two main data centers in North America. The data centers are located in the
same city. The data centers connect to each other by using high-bandwidth, low-latency WAN links. Each
data center connects directly to the Internet.
Northwind Traders also has a remote office in Asia that connects to both of the North American data
centers by using a WAN link. The Asian office has 30 multipurpose servers.
Each North American data center contains two separate network segments. One network segment is
used to host the internal servers of Northwind Traders. The other network segment is used for the
hosted customer environments.
Existing EnvironmentActive Directory
The network contains an Active Directory forest named northwindtraders.com. The forest contains a
single domain. All servers run Windows Server 2012 R2.
Server Environment
The network has the following technologies deployed:
Service Provider Foundation
Windows Azure Pack for Windows Server
System Center 2012 R2 Virtual Machine Manager (VMM)
An Active Directory Rights Management Services (AD RMS) cluster
An Active Directory Certificate Services (AD CS) enterprise certification authority (CA)
All newly deployed servers will include the following components:
Dual 10-GbE Remote Direct Memory Access (RDMA)-capable network adapters
Dual 1-GbE network adapters
128 GB of RAM
Requirements
Business Goals
Northwind Traders will provide hosting services to two customers named Customer1 and Customer2.
The network of each customer is configured as shown in the following table.
Planned Changes
Northwind Traders plans to implement the following changes:
Deploy System Center 2012 R2 Operations Manager.
Deploy Windows Server 2012 R2 iSCSI and SMB-based storage.
Implement Hyper-V Recovery Manager to protect virtual machines.
Deploy a certificate revocation list (CRL) distribution point (CDP) on the internal network.
For Customer 1, install server authentication certificates issued by the CA of Northwind Traders
on the virtual machine in the hosting networks.General Requirements
Northwind Traders identifies the following requirements:
Storage traffic must use dedicated adapters.
All storage and network traffic must be load balanced.
The amount of network traffic between the internal network and the hosting network must be
minimized.
The publication of CRLs to CDPs must be automatic.
Each customer must use dedicated Hyper-V hosts.
Administrative effort must be minimized, whenever possible.
All servers and networks must be monitored by using Operations Manager.
Anonymous access to internal file shares from the hosting network must be prohibited.
All Hyper-V hosts must use Cluster Shared Volume (CSV) shared storage to host virtual
machines.
All Hyper-V storage and network traffic must remain available if single network adapter fails.
The Hyper-V hosts connected to the SMB-based storage must be able to make use of the
RDMA technology.
The number of servers and ports in the hosting environment to which the customer has access
must be minimized.
Customer1 Requirements
Northwind Traders identifies the following requirements for Customer1:
Customer1 must use SMB-based storage exclusively.
Customer1 must use App Controller to manage hosted virtual machines.
The virtual machines of Customer1 must be recoverable if a single data center fails.
Customer1 must be able to delegate self-service roles in its hosted environment to its users.
Customer1 must be able to check for the revocation of certificates issued by the CA of
Northwind Traders.
The users of Customer1 must be able to obtain use licenses for documents protected by the AD
RMS of Northwind Traders.
Certificates issued to the virtual machines of Customer1 that reside on the hosted networks
must be renewed automatically.
Customer2 Requirements
Northwind Traders identifies the following requirements for Customer2:
Customer2 must use iSCSI-based storage exclusively.
All of the virtual machines of Customer2 must be migrated by using a SAN transfer.
None of the metadata from the virtual machines of Customer2 must be stored in Windows
Azure.
The network configuration of the Hyper-V hosts for Customer2 must be controlled by using
logical switches. The only VMM network port profiles and classifications allowed by Customer2 must be lowbandwidth, medium-bandwidth, or high-bandwidth.
The users at Northwind Traders must be able to obtain use licenses for documents protected
by the AD RMS cluster of Customer2. Customer2 plans to decommission its AD RMS cluster
during the next year.
###EndCaseStudy###
HOTSPOT
You need to recommend a configuration for the CA extensions of Northwind Traders that meets the
certificate revocation requirement of Customer1.
What should you recommend? To answer, select the appropriate prefix of the target location for the
each extension settings in the answer area.
which System Center 2012 Virtual Machine Manager (VMM) group should you assign Group1?
###BeginCaseStudy###
Topic 4, A.Datum Corporation
Overview
A) Datum Corporation is an accounting company.
The company has a main office and two branch offices. The main office is located in Miami. The branch
offices are located in New York and Seattle.
Existing Environment
Network Infrastructure
The network contains an Active Directory domain named adatum.com. All servers run Windows Server
2008 R2. The main office has the following servers and client computers:
Two domain controllers configured as DNS servers and DHCP servers
One file server that has multiples shares
One thousand client computers that run Windows 7
Each branch office has the following servers and client computers:
One domain controller configured as a DNS server and a DHCP server
Five hundred to 800 client computers that run Windows XP
Each office has multiple subnets. The network speed of the local area network (LAN) is 1 gigabit per
second. The offices connect to each other by using a WAN link. The main office is connected to the
Internet.
Current Issues
The WAN link between the Miami office and the Seattle office is a low bandwidth link with high latency.
The link will not be replaced for another year.
Requirements
Application Requirements
The company is developing an application named App1. App1 is a multi-tier application that will be sold
as a service to customers.
Each instance of App1 is comprised of the following three tiers:
A web front end
A middle tier that uses Windows Communication Foundation (WCF)
A Microsoft SQL Server 2008 R2 database on the back endEach tier will be hosted on one or more virtual machines. Multiple tiers cannot coexist on the same
virtual machine.
When customers purchase App1, they can select from one of the following service levels:
Standard: Uses a single instance of each virtual machine required by App1. If a virtual machine
becomes unresponsive, the virtual machine must be restarted.
Enterprise: Uses multiple instances of each virtual machine required by App1 to provide highavailability and fault tolerance.
All virtual hard disk (VHD) files for App1 will be stored in a file share. The VHDs must be available if a
server fails.
You plan to deploy an application named App2. App2 is comprised of the following two tiers:
A web front end
A dedicated SQL Server 2008 R2 database on the back end
App2 will be hosted on a set of virtual machines in a Hyper-V cluster in the Miami office. The virtual
machines will use dynamic IP addresses. A copy of the App2 virtual machines will be maintained in the
Seattle office.
App2 will be used by users from a partner company named Trey Research. Trey Research has a single
Active Directory domain named treyresearch.com. Treyresearch.com contains a server that has the
Active Directory Federation Services server role and all of the Active Directory Federation Services (AD
FS) role services installed.
Planned Changes
A) Datum plans to implement the following changes:
Replace all of the servers with new servers that run Windows Server 2012.
Implement a private cloud by using Microsoft System Center 2012 to host instances of App1.
In the Miami office, deploy four new Hyper-V hosts to the perimeter network.
In the Miami office, deploy two new Hyper-V hosts to the local network.
In the Seattle office, deploy two new Hyper-V hosts.
In the Miami office, implement a System Center 2012 Configuration Manager primary site that
has all of the system roles installed.
Implement a public key infrastructure (PKI).
Notification Requirements
A) Datum identifies the following notification requirements:
Help desk tickets must be created and assigned automatically when an instance of App1
becomes unresponsive. Customers who select the Enterprise service level must receive an email notification each time
a help desk ticket for their instance of App1 is opened or closed.
Technical Requirements
A) Datum identifies the following technical requirements:
Minimize costs whenever possible.
Minimize the amount of WAN traffic
Minimize the amount of administrative effort whenever possible.
Provide the fastest possible failover for the virtual machines hosting App2.
Ensure that administrators can view a consolidated report about the software updates in all of
the offices.
Ensure that administrators in the Miami office can approve updates for the client computers in
all of the offices.
Security Requirements
A) Datum identifies the following security requirements:
An offline root certification authority (CA) must be configured.
Client computers must be issued certificates by a server in their local office.
Changes to the CA configuration settings and the CA security settings must be logged.
Client computers must be able to renew certificates automatically over the Internet.
The number of permissions and privileges assigned to users must be minimized whenever
possible.
Users from a group named Group1 must be able to create new instances of App1 in the private
cloud.
Client computers must be issued new certificates when the computers are connected to the
local network only.
The virtual machines used to host App2 must use BitLocker Drive Encryption (BitLocker).
Users from Trey Research must be able to access App2 by using their credentials from
treyresearch.com.
###EndCaseStudy###
You need to recommend a solution that meets the security requirements for Group1.
To which System Center 2012 Virtual Machine Manager (VMM) group should you assign Group1?
Which Certificate Services role services should you recommend?
###BeginCaseStudy###
Topic 4, A.Datum Corporation
Overview
A) Datum Corporation is an accounting company.
The company has a main office and two branch offices. The main office is located in Miami. The branch
offices are located in New York and Seattle.
Existing Environment
Network Infrastructure
The network contains an Active Directory domain named adatum.com. All servers run Windows Server
2008 R2. The main office has the following servers and client computers:
Two domain controllers configured as DNS servers and DHCP servers
One file server that has multiples shares
One thousand client computers that run Windows 7
Each branch office has the following servers and client computers:
One domain controller configured as a DNS server and a DHCP server
Five hundred to 800 client computers that run Windows XP
Each office has multiple subnets. The network speed of the local area network (LAN) is 1 gigabit per
second. The offices connect to each other by using a WAN link. The main office is connected to the
Internet.
Current Issues
The WAN link between the Miami office and the Seattle office is a low bandwidth link with high latency.
The link will not be replaced for another year.
Requirements
Application Requirements
The company is developing an application named App1. App1 is a multi-tier application that will be sold
as a service to customers.
Each instance of App1 is comprised of the following three tiers:
A web front end
A middle tier that uses Windows Communication Foundation (WCF)
A Microsoft SQL Server 2008 R2 database on the back endEach tier will be hosted on one or more virtual machines. Multiple tiers cannot coexist on the same
virtual machine.
When customers purchase App1, they can select from one of the following service levels:
Standard: Uses a single instance of each virtual machine required by App1. If a virtual machine
becomes unresponsive, the virtual machine must be restarted.
Enterprise: Uses multiple instances of each virtual machine required by App1 to provide highavailability and fault tolerance.
All virtual hard disk (VHD) files for App1 will be stored in a file share. The VHDs must be available if a
server fails.
You plan to deploy an application named App2. App2 is comprised of the following two tiers:
A web front end
A dedicated SQL Server 2008 R2 database on the back end
App2 will be hosted on a set of virtual machines in a Hyper-V cluster in the Miami office. The virtual
machines will use dynamic IP addresses. A copy of the App2 virtual machines will be maintained in the
Seattle office.
App2 will be used by users from a partner company named Trey Research. Trey Research has a single
Active Directory domain named treyresearch.com. Treyresearch.com contains a server that has the
Active Directory Federation Services server role and all of the Active Directory Federation Services (AD
FS) role services installed.
Planned Changes
A) Datum plans to implement the following changes:
Replace all of the servers with new servers that run Windows Server 2012.
Implement a private cloud by using Microsoft System Center 2012 to host instances of App1.
In the Miami office, deploy four new Hyper-V hosts to the perimeter network.
In the Miami office, deploy two new Hyper-V hosts to the local network.
In the Seattle office, deploy two new Hyper-V hosts.
In the Miami office, implement a System Center 2012 Configuration Manager primary site that
has all of the system roles installed.
Implement a public key infrastructure (PKI).
Notification Requirements
A) Datum identifies the following notification requirements:
Help desk tickets must be created and assigned automatically when an instance of App1
becomes unresponsive. Customers who select the Enterprise service level must receive an email notification each time
a help desk ticket for their instance of App1 is opened or closed.
Technical Requirements
A) Datum identifies the following technical requirements:
Minimize costs whenever possible.
Minimize the amount of WAN traffic
Minimize the amount of administrative effort whenever possible.
Provide the fastest possible failover for the virtual machines hosting App2.
Ensure that administrators can view a consolidated report about the software updates in all of
the offices.
Ensure that administrators in the Miami office can approve updates for the client computers in
all of the offices.
Security Requirements
A) Datum identifies the following security requirements:
An offline root certification authority (CA) must be configured.
Client computers must be issued certificates by a server in their local office.
Changes to the CA configuration settings and the CA security settings must be logged.
Client computers must be able to renew certificates automatically over the Internet.
The number of permissions and privileges assigned to users must be minimized whenever
possible.
Users from a group named Group1 must be able to create new instances of App1 in the private
cloud.
Client computers must be issued new certificates when the computers are connected to the
local network only.
The virtual machines used to host App2 must use BitLocker Drive Encryption (BitLocker).
Users from Trey Research must be able to access App2 by using their credentials from
treyresearch.com.
###EndCaseStudy###
You need to recommend which Certificate Services role service must be deployed to the perimeter
network. The solution must meet the security requirements.
Which Certificate Services role services should you recommend?
What should you include in the recommendation?
###BeginCaseStudy###
Topic 4, A.Datum Corporation
Overview
A) Datum Corporation is an accounting company.
The company has a main office and two branch offices. The main office is located in Miami. The branch
offices are located in New York and Seattle.
Existing Environment
Network Infrastructure
The network contains an Active Directory domain named adatum.com. All servers run Windows Server
2008 R2. The main office has the following servers and client computers:
Two domain controllers configured as DNS servers and DHCP servers
One file server that has multiples shares
One thousand client computers that run Windows 7
Each branch office has the following servers and client computers:
One domain controller configured as a DNS server and a DHCP server
Five hundred to 800 client computers that run Windows XP
Each office has multiple subnets. The network speed of the local area network (LAN) is 1 gigabit per
second. The offices connect to each other by using a WAN link. The main office is connected to the
Internet.
Current Issues
The WAN link between the Miami office and the Seattle office is a low bandwidth link with high latency.
The link will not be replaced for another year.
Requirements
Application Requirements
The company is developing an application named App1. App1 is a multi-tier application that will be sold
as a service to customers.
Each instance of App1 is comprised of the following three tiers:
A web front end
A middle tier that uses Windows Communication Foundation (WCF)
A Microsoft SQL Server 2008 R2 database on the back endEach tier will be hosted on one or more virtual machines. Multiple tiers cannot coexist on the same
virtual machine.
When customers purchase App1, they can select from one of the following service levels:
Standard: Uses a single instance of each virtual machine required by App1. If a virtual machine
becomes unresponsive, the virtual machine must be restarted.
Enterprise: Uses multiple instances of each virtual machine required by App1 to provide highavailability and fault tolerance.
All virtual hard disk (VHD) files for App1 will be stored in a file share. The VHDs must be available if a
server fails.
You plan to deploy an application named App2. App2 is comprised of the following two tiers:
A web front end
A dedicated SQL Server 2008 R2 database on the back end
App2 will be hosted on a set of virtual machines in a Hyper-V cluster in the Miami office. The virtual
machines will use dynamic IP addresses. A copy of the App2 virtual machines will be maintained in the
Seattle office.
App2 will be used by users from a partner company named Trey Research. Trey Research has a single
Active Directory domain named treyresearch.com. Treyresearch.com contains a server that has the
Active Directory Federation Services server role and all of the Active Directory Federation Services (AD
FS) role services installed.
Planned Changes
A) Datum plans to implement the following changes:
Replace all of the servers with new servers that run Windows Server 2012.
Implement a private cloud by using Microsoft System Center 2012 to host instances of App1.
In the Miami office, deploy four new Hyper-V hosts to the perimeter network.
In the Miami office, deploy two new Hyper-V hosts to the local network.
In the Seattle office, deploy two new Hyper-V hosts.
In the Miami office, implement a System Center 2012 Configuration Manager primary site that
has all of the system roles installed.
Implement a public key infrastructure (PKI).
Notification Requirements
A) Datum identifies the following notification requirements:
Help desk tickets must be created and assigned automatically when an instance of App1
becomes unresponsive. Customers who select the Enterprise service level must receive an email notification each time
a help desk ticket for their instance of App1 is opened or closed.
Technical Requirements
A) Datum identifies the following technical requirements:
Minimize costs whenever possible.
Minimize the amount of WAN traffic
Minimize the amount of administrative effort whenever possible.
Provide the fastest possible failover for the virtual machines hosting App2.
Ensure that administrators can view a consolidated report about the software updates in all of
the offices.
Ensure that administrators in the Miami office can approve updates for the client computers in
all of the offices.
Security Requirements
A) Datum identifies the following security requirements:
An offline root certification authority (CA) must be configured.
Client computers must be issued certificates by a server in their local office.
Changes to the CA configuration settings and the CA security settings must be logged.
Client computers must be able to renew certificates automatically over the Internet.
The number of permissions and privileges assigned to users must be minimized whenever
possible.
Users from a group named Group1 must be able to create new instances of App1 in the private
cloud.
Client computers must be issued new certificates when the computers are connected to the
local network only.
The virtual machines used to host App2 must use BitLocker Drive Encryption (BitLocker).
Users from Trey Research must be able to access App2 by using their credentials from
treyresearch.com.
###EndCaseStudy###
You need to recommend a storage solution for the App1 VHDs. The solution must minimize downtime if
a Hyper-V host fails.
What should you include in the recommendation?
Which System Center 2012 components should you include in the recommendation?
###BeginCaseStudy###
Topic 4, A.Datum Corporation
Overview
A) Datum Corporation is an accounting company.
The company has a main office and two branch offices. The main office is located in Miami. The branch
offices are located in New York and Seattle.
Existing Environment
Network Infrastructure
The network contains an Active Directory domain named adatum.com. All servers run Windows Server
2008 R2. The main office has the following servers and client computers:
Two domain controllers configured as DNS servers and DHCP servers
One file server that has multiples shares
One thousand client computers that run Windows 7
Each branch office has the following servers and client computers:
One domain controller configured as a DNS server and a DHCP server
Five hundred to 800 client computers that run Windows XP
Each office has multiple subnets. The network speed of the local area network (LAN) is 1 gigabit per
second. The offices connect to each other by using a WAN link. The main office is connected to the
Internet.
Current Issues
The WAN link between the Miami office and the Seattle office is a low bandwidth link with high latency.
The link will not be replaced for another year.
Requirements
Application Requirements
The company is developing an application named App1. App1 is a multi-tier application that will be sold
as a service to customers.
Each instance of App1 is comprised of the following three tiers:
A web front end
A middle tier that uses Windows Communication Foundation (WCF)
A Microsoft SQL Server 2008 R2 database on the back endEach tier will be hosted on one or more virtual machines. Multiple tiers cannot coexist on the same
virtual machine.
When customers purchase App1, they can select from one of the following service levels:
Standard: Uses a single instance of each virtual machine required by App1. If a virtual machine
becomes unresponsive, the virtual machine must be restarted.
Enterprise: Uses multiple instances of each virtual machine required by App1 to provide highavailability and fault tolerance.
All virtual hard disk (VHD) files for App1 will be stored in a file share. The VHDs must be available if a
server fails.
You plan to deploy an application named App2. App2 is comprised of the following two tiers:
A web front end
A dedicated SQL Server 2008 R2 database on the back end
App2 will be hosted on a set of virtual machines in a Hyper-V cluster in the Miami office. The virtual
machines will use dynamic IP addresses. A copy of the App2 virtual machines will be maintained in the
Seattle office.
App2 will be used by users from a partner company named Trey Research. Trey Research has a single
Active Directory domain named treyresearch.com. Treyresearch.com contains a server that has the
Active Directory Federation Services server role and all of the Active Directory Federation Services (AD
FS) role services installed.
Planned Changes
A) Datum plans to implement the following changes:
Replace all of the servers with new servers that run Windows Server 2012.
Implement a private cloud by using Microsoft System Center 2012 to host instances of App1.
In the Miami office, deploy four new Hyper-V hosts to the perimeter network.
In the Miami office, deploy two new Hyper-V hosts to the local network.
In the Seattle office, deploy two new Hyper-V hosts.
In the Miami office, implement a System Center 2012 Configuration Manager primary site that
has all of the system roles installed.
Implement a public key infrastructure (PKI).
Notification Requirements
A) Datum identifies the following notification requirements:
Help desk tickets must be created and assigned automatically when an instance of App1
becomes unresponsive. Customers who select the Enterprise service level must receive an email notification each time
a help desk ticket for their instance of App1 is opened or closed.
Technical Requirements
A) Datum identifies the following technical requirements:
Minimize costs whenever possible.
Minimize the amount of WAN traffic
Minimize the amount of administrative effort whenever possible.
Provide the fastest possible failover for the virtual machines hosting App2.
Ensure that administrators can view a consolidated report about the software updates in all of
the offices.
Ensure that administrators in the Miami office can approve updates for the client computers in
all of the offices.
Security Requirements
A) Datum identifies the following security requirements:
An offline root certification authority (CA) must be configured.
Client computers must be issued certificates by a server in their local office.
Changes to the CA configuration settings and the CA security settings must be logged.
Client computers must be able to renew certificates automatically over the Internet.
The number of permissions and privileges assigned to users must be minimized whenever
possible.
Users from a group named Group1 must be able to create new instances of App1 in the private
cloud.
Client computers must be issued new certificates when the computers are connected to the
local network only.
The virtual machines used to host App2 must use BitLocker Drive Encryption (BitLocker).
Users from Trey Research must be able to access App2 by using their credentials from
treyresearch.com.
###EndCaseStudy###
You need to recommend a solution that meets the notification requirements.
Which System Center 2012 components should you include in the recommendation?
Which changes should you identify?
###BeginCaseStudy###
Topic 4, A.Datum Corporation
Overview
A) Datum Corporation is an accounting company.
The company has a main office and two branch offices. The main office is located in Miami. The branch
offices are located in New York and Seattle.
Existing Environment
Network Infrastructure
The network contains an Active Directory domain named adatum.com. All servers run Windows Server
2008 R2. The main office has the following servers and client computers:
Two domain controllers configured as DNS servers and DHCP servers
One file server that has multiples shares
One thousand client computers that run Windows 7
Each branch office has the following servers and client computers:
One domain controller configured as a DNS server and a DHCP server
Five hundred to 800 client computers that run Windows XP
Each office has multiple subnets. The network speed of the local area network (LAN) is 1 gigabit per
second. The offices connect to each other by using a WAN link. The main office is connected to the
Internet.
Current Issues
The WAN link between the Miami office and the Seattle office is a low bandwidth link with high latency.
The link will not be replaced for another year.
Requirements
Application Requirements
The company is developing an application named App1. App1 is a multi-tier application that will be sold
as a service to customers.
Each instance of App1 is comprised of the following three tiers:
A web front end
A middle tier that uses Windows Communication Foundation (WCF)
A Microsoft SQL Server 2008 R2 database on the back endEach tier will be hosted on one or more virtual machines. Multiple tiers cannot coexist on the same
virtual machine.
When customers purchase App1, they can select from one of the following service levels:
Standard: Uses a single instance of each virtual machine required by App1. If a virtual machine
becomes unresponsive, the virtual machine must be restarted.
Enterprise: Uses multiple instances of each virtual machine required by App1 to provide highavailability and fault tolerance.
All virtual hard disk (VHD) files for App1 will be stored in a file share. The VHDs must be available if a
server fails.
You plan to deploy an application named App2. App2 is comprised of the following two tiers:
A web front end
A dedicated SQL Server 2008 R2 database on the back end
App2 will be hosted on a set of virtual machines in a Hyper-V cluster in the Miami office. The virtual
machines will use dynamic IP addresses. A copy of the App2 virtual machines will be maintained in the
Seattle office.
App2 will be used by users from a partner company named Trey Research. Trey Research has a single
Active Directory domain named treyresearch.com. Treyresearch.com contains a server that has the
Active Directory Federation Services server role and all of the Active Directory Federation Services (AD
FS) role services installed.
Planned Changes
A) Datum plans to implement the following changes:
Replace all of the servers with new servers that run Windows Server 2012.
Implement a private cloud by using Microsoft System Center 2012 to host instances of App1.
In the Miami office, deploy four new Hyper-V hosts to the perimeter network.
In the Miami office, deploy two new Hyper-V hosts to the local network.
In the Seattle office, deploy two new Hyper-V hosts.
In the Miami office, implement a System Center 2012 Configuration Manager primary site that
has all of the system roles installed.
Implement a public key infrastructure (PKI).
Notification Requirements
A) Datum identifies the following notification requirements:
Help desk tickets must be created and assigned automatically when an instance of App1
becomes unresponsive. Customers who select the Enterprise service level must receive an email notification each time
a help desk ticket for their instance of App1 is opened or closed.
Technical Requirements
A) Datum identifies the following technical requirements:
Minimize costs whenever possible.
Minimize the amount of WAN traffic
Minimize the amount of administrative effort whenever possible.
Provide the fastest possible failover for the virtual machines hosting App2.
Ensure that administrators can view a consolidated report about the software updates in all of
the offices.
Ensure that administrators in the Miami office can approve updates for the client computers in
all of the offices.
Security Requirements
A) Datum identifies the following security requirements:
An offline root certification authority (CA) must be configured.
Client computers must be issued certificates by a server in their local office.
Changes to the CA configuration settings and the CA security settings must be logged.
Client computers must be able to renew certificates automatically over the Internet.
The number of permissions and privileges assigned to users must be minimized whenever
possible.
Users from a group named Group1 must be able to create new instances of App1 in the private
cloud.
Client computers must be issued new certificates when the computers are connected to the
local network only.
The virtual machines used to host App2 must use BitLocker Drive Encryption (BitLocker).
Users from Trey Research must be able to access App2 by using their credentials from
treyresearch.com.
###EndCaseStudy###
You are evaluating the deployment of a multi-site Hyper-V failover cluster in the Miami office and the
Seattle office to host App2.
You need to identify which changes must be made to support the use of the multi-site cluster.
Which changes should you identify?
What should you include in the recommendation?
###BeginCaseStudy###
Topic 4, A.Datum Corporation
Overview
A) Datum Corporation is an accounting company.
The company has a main office and two branch offices. The main office is located in Miami. The branch
offices are located in New York and Seattle.
Existing Environment
Network Infrastructure
The network contains an Active Directory domain named adatum.com. All servers run Windows Server
2008 R2. The main office has the following servers and client computers:
Two domain controllers configured as DNS servers and DHCP servers
One file server that has multiples shares
One thousand client computers that run Windows 7
Each branch office has the following servers and client computers:
One domain controller configured as a DNS server and a DHCP server
Five hundred to 800 client computers that run Windows XP
Each office has multiple subnets. The network speed of the local area network (LAN) is 1 gigabit per
second. The offices connect to each other by using a WAN link. The main office is connected to the
Internet.
Current Issues
The WAN link between the Miami office and the Seattle office is a low bandwidth link with high latency.
The link will not be replaced for another year.
Requirements
Application Requirements
The company is developing an application named App1. App1 is a multi-tier application that will be sold
as a service to customers.
Each instance of App1 is comprised of the following three tiers:
A web front end
A middle tier that uses Windows Communication Foundation (WCF)
A Microsoft SQL Server 2008 R2 database on the back endEach tier will be hosted on one or more virtual machines. Multiple tiers cannot coexist on the same
virtual machine.
When customers purchase App1, they can select from one of the following service levels:
Standard: Uses a single instance of each virtual machine required by App1. If a virtual machine
becomes unresponsive, the virtual machine must be restarted.
Enterprise: Uses multiple instances of each virtual machine required by App1 to provide highavailability and fault tolerance.
All virtual hard disk (VHD) files for App1 will be stored in a file share. The VHDs must be available if a
server fails.
You plan to deploy an application named App2. App2 is comprised of the following two tiers:
A web front end
A dedicated SQL Server 2008 R2 database on the back end
App2 will be hosted on a set of virtual machines in a Hyper-V cluster in the Miami office. The virtual
machines will use dynamic IP addresses. A copy of the App2 virtual machines will be maintained in the
Seattle office.
App2 will be used by users from a partner company named Trey Research. Trey Research has a single
Active Directory domain named treyresearch.com. Treyresearch.com contains a server that has the
Active Directory Federation Services server role and all of the Active Directory Federation Services (AD
FS) role services installed.
Planned Changes
A) Datum plans to implement the following changes:
Replace all of the servers with new servers that run Windows Server 2012.
Implement a private cloud by using Microsoft System Center 2012 to host instances of App1.
In the Miami office, deploy four new Hyper-V hosts to the perimeter network.
In the Miami office, deploy two new Hyper-V hosts to the local network.
In the Seattle office, deploy two new Hyper-V hosts.
In the Miami office, implement a System Center 2012 Configuration Manager primary site that
has all of the system roles installed.
Implement a public key infrastructure (PKI).
Notification Requirements
A) Datum identifies the following notification requirements:
Help desk tickets must be created and assigned automatically when an instance of App1
becomes unresponsive. Customers who select the Enterprise service level must receive an email notification each time
a help desk ticket for their instance of App1 is opened or closed.
Technical Requirements
A) Datum identifies the following technical requirements:
Minimize costs whenever possible.
Minimize the amount of WAN traffic
Minimize the amount of administrative effort whenever possible.
Provide the fastest possible failover for the virtual machines hosting App2.
Ensure that administrators can view a consolidated report about the software updates in all of
the offices.
Ensure that administrators in the Miami office can approve updates for the client computers in
all of the offices.
Security Requirements
A) Datum identifies the following security requirements:
An offline root certification authority (CA) must be configured.
Client computers must be issued certificates by a server in their local office.
Changes to the CA configuration settings and the CA security settings must be logged.
Client computers must be able to renew certificates automatically over the Internet.
The number of permissions and privileges assigned to users must be minimized whenever
possible.
Users from a group named Group1 must be able to create new instances of App1 in the private
cloud.
Client computers must be issued new certificates when the computers are connected to the
local network only.
The virtual machines used to host App2 must use BitLocker Drive Encryption (BitLocker).
Users from Trey Research must be able to access App2 by using their credentials from
treyresearch.com.
###EndCaseStudy###
You need to recommend a solution to maintain a copy of App2. The solution must meet the application
requirements and must minimize additional hardware purchases.
What should you include in the recommendation?
Solution: You recommend a scale-out file server that uses an SMB share.Does this meet the goal?
###BeginCaseStudy###
Topic 4, A.Datum Corporation
Overview
A) Datum Corporation is an accounting company.
The company has a main office and two branch offices. The main office is located in Miami. The branch
offices are located in New York and Seattle.
Existing Environment
Network Infrastructure
The network contains an Active Directory domain named adatum.com. All servers run Windows Server
2008 R2. The main office has the following servers and client computers:
Two domain controllers configured as DNS servers and DHCP servers
One file server that has multiples shares
One thousand client computers that run Windows 7
Each branch office has the following servers and client computers:
One domain controller configured as a DNS server and a DHCP server
Five hundred to 800 client computers that run Windows XP
Each office has multiple subnets. The network speed of the local area network (LAN) is 1 gigabit per
second. The offices connect to each other by using a WAN link. The main office is connected to the
Internet.
Current Issues
The WAN link between the Miami office and the Seattle office is a low bandwidth link with high latency.
The link will not be replaced for another year.
Requirements
Application Requirements
The company is developing an application named App1. App1 is a multi-tier application that will be sold
as a service to customers.
Each instance of App1 is comprised of the following three tiers:
A web front end
A middle tier that uses Windows Communication Foundation (WCF)
A Microsoft SQL Server 2008 R2 database on the back endEach tier will be hosted on one or more virtual machines. Multiple tiers cannot coexist on the same
virtual machine.
When customers purchase App1, they can select from one of the following service levels:
Standard: Uses a single instance of each virtual machine required by App1. If a virtual machine
becomes unresponsive, the virtual machine must be restarted.
Enterprise: Uses multiple instances of each virtual machine required by App1 to provide highavailability and fault tolerance.
All virtual hard disk (VHD) files for App1 will be stored in a file share. The VHDs must be available if a
server fails.
You plan to deploy an application named App2. App2 is comprised of the following two tiers:
A web front end
A dedicated SQL Server 2008 R2 database on the back end
App2 will be hosted on a set of virtual machines in a Hyper-V cluster in the Miami office. The virtual
machines will use dynamic IP addresses. A copy of the App2 virtual machines will be maintained in the
Seattle office.
App2 will be used by users from a partner company named Trey Research. Trey Research has a single
Active Directory domain named treyresearch.com. Treyresearch.com contains a server that has the
Active Directory Federation Services server role and all of the Active Directory Federation Services (AD
FS) role services installed.
Planned Changes
A) Datum plans to implement the following changes:
Replace all of the servers with new servers that run Windows Server 2012.
Implement a private cloud by using Microsoft System Center 2012 to host instances of App1.
In the Miami office, deploy four new Hyper-V hosts to the perimeter network.
In the Miami office, deploy two new Hyper-V hosts to the local network.
In the Seattle office, deploy two new Hyper-V hosts.
In the Miami office, implement a System Center 2012 Configuration Manager primary site that
has all of the system roles installed.
Implement a public key infrastructure (PKI).
Notification Requirements
A) Datum identifies the following notification requirements:
Help desk tickets must be created and assigned automatically when an instance of App1
becomes unresponsive. Customers who select the Enterprise service level must receive an email notification each time
a help desk ticket for their instance of App1 is opened or closed.
Technical Requirements
A) Datum identifies the following technical requirements:
Minimize costs whenever possible.
Minimize the amount of WAN traffic
Minimize the amount of administrative effort whenever possible.
Provide the fastest possible failover for the virtual machines hosting App2.
Ensure that administrators can view a consolidated report about the software updates in all of
the offices.
Ensure that administrators in the Miami office can approve updates for the client computers in
all of the offices.
Security Requirements
A) Datum identifies the following security requirements:
An offline root certification authority (CA) must be configured.
Client computers must be issued certificates by a server in their local office.
Changes to the CA configuration settings and the CA security settings must be logged.
Client computers must be able to renew certificates automatically over the Internet.
The number of permissions and privileges assigned to users must be minimized whenever
possible.
Users from a group named Group1 must be able to create new instances of App1 in the private
cloud.
Client computers must be issued new certificates when the computers are connected to the
local network only.
The virtual machines used to host App2 must use BitLocker Drive Encryption (BitLocker).
Users from Trey Research must be able to access App2 by using their credentials from
treyresearch.com.
###EndCaseStudy###
You need to recommend which type of clustered file server and which type of file share must be used in
the Hyper-V cluster that hosts App2. The solution must meet the technical requirements and the
security requirements.
Solution: You recommend a scale-out file server that uses an SMB share.Does this meet the goal?
Does this meet the goal?
###BeginCaseStudy###
Topic 4, A.Datum Corporation
Overview
A) Datum Corporation is an accounting company.
The company has a main office and two branch offices. The main office is located in Miami. The branch
offices are located in New York and Seattle.
Existing Environment
Network Infrastructure
The network contains an Active Directory domain named adatum.com. All servers run Windows Server
2008 R2. The main office has the following servers and client computers:
Two domain controllers configured as DNS servers and DHCP servers
One file server that has multiples shares
One thousand client computers that run Windows 7
Each branch office has the following servers and client computers:
One domain controller configured as a DNS server and a DHCP server
Five hundred to 800 client computers that run Windows XP
Each office has multiple subnets. The network speed of the local area network (LAN) is 1 gigabit per
second. The offices connect to each other by using a WAN link. The main office is connected to the
Internet.
Current Issues
The WAN link between the Miami office and the Seattle office is a low bandwidth link with high latency.
The link will not be replaced for another year.
Requirements
Application Requirements
The company is developing an application named App1. App1 is a multi-tier application that will be sold
as a service to customers.
Each instance of App1 is comprised of the following three tiers:
A web front end
A middle tier that uses Windows Communication Foundation (WCF)
A Microsoft SQL Server 2008 R2 database on the back endEach tier will be hosted on one or more virtual machines. Multiple tiers cannot coexist on the same
virtual machine.
When customers purchase App1, they can select from one of the following service levels:
Standard: Uses a single instance of each virtual machine required by App1. If a virtual machine
becomes unresponsive, the virtual machine must be restarted.
Enterprise: Uses multiple instances of each virtual machine required by App1 to provide highavailability and fault tolerance.
All virtual hard disk (VHD) files for App1 will be stored in a file share. The VHDs must be available if a
server fails.
You plan to deploy an application named App2. App2 is comprised of the following two tiers:
A web front end
A dedicated SQL Server 2008 R2 database on the back end
App2 will be hosted on a set of virtual machines in a Hyper-V cluster in the Miami office. The virtual
machines will use dynamic IP addresses. A copy of the App2 virtual machines will be maintained in the
Seattle office.
App2 will be used by users from a partner company named Trey Research. Trey Research has a single
Active Directory domain named treyresearch.com. Treyresearch.com contains a server that has the
Active Directory Federation Services server role and all of the Active Directory Federation Services (AD
FS) role services installed.
Planned Changes
A) Datum plans to implement the following changes:
Replace all of the servers with new servers that run Windows Server 2012.
Implement a private cloud by using Microsoft System Center 2012 to host instances of App1.
In the Miami office, deploy four new Hyper-V hosts to the perimeter network.
In the Miami office, deploy two new Hyper-V hosts to the local network.
In the Seattle office, deploy two new Hyper-V hosts.
In the Miami office, implement a System Center 2012 Configuration Manager primary site that
has all of the system roles installed.
Implement a public key infrastructure (PKI).
Notification Requirements
A) Datum identifies the following notification requirements:
Help desk tickets must be created and assigned automatically when an instance of App1
becomes unresponsive. Customers who select the Enterprise service level must receive an email notification each time
a help desk ticket for their instance of App1 is opened or closed.
Technical Requirements
A) Datum identifies the following technical requirements:
Minimize costs whenever possible.
Minimize the amount of WAN traffic
Minimize the amount of administrative effort whenever possible.
Provide the fastest possible failover for the virtual machines hosting App2.
Ensure that administrators can view a consolidated report about the software updates in all of
the offices.
Ensure that administrators in the Miami office can approve updates for the client computers in
all of the offices.
Security Requirements
A) Datum identifies the following security requirements:
An offline root certification authority (CA) must be configured.
Client computers must be issued certificates by a server in their local office.
Changes to the CA configuration settings and the CA security settings must be logged.
Client computers must be able to renew certificates automatically over the Internet.
The number of permissions and privileges assigned to users must be minimized whenever
possible.
Users from a group named Group1 must be able to create new instances of App1 in the private
cloud.
Client computers must be issued new certificates when the computers are connected to the
local network only.
The virtual machines used to host App2 must use BitLocker Drive Encryption (BitLocker).
Users from Trey Research must be able to access App2 by using their credentials from
treyresearch.com.
###EndCaseStudy###
You need to recommend which type of clustered file server and which type of file share must be used in
the Hyper-V cluster that hosts App2. The solution must meet the technical requirements and the
security requirements.
Solution: You recommend a scale-out file server that uses an NFS share.
Does this meet the goal?