Which of the following actions should you take?
You work as an administrator at ABC.com. The ABC.com network consists of a single domain named ABC.
com. All servers in the ABC.com domain, including domain controllers, have Windows Server 2012 installed.
ABC.com’s user accounts are located in an organizational unit (OU), named ABCStaff. ABC.com’s
managersbelong to a group, named ABCManagers.
You have been instructed to create a new Group Policy object (GPO) that should be linked to the ABCStaffOU,
but not affect ABC.com’s managers.
Which of the following actions should you take?
You need to ensure that you can manage Server2 fromServer1 by using Server Manager on Server1
You have two servers named Server1 and Server2 thatrun Windows Server 2012. Server1 and Server2 are
part of a workgroup.
On Server1, you add Server2 to Server Manager.
When you attempt to connect to Server2 from Server Manager, you receive the following error message:
“Credentials not valid.”
You need to ensure that you can manage Server2 fromServer1 by using Server Manager on Server1.
What should you do?
Select Yes if the statement can be shown to be truebased on the available information; otherwise select No.
HOTSPOT
You have a shared folder named Share1. The folder permissions of Share1 are configured as shown in the
Folder Permissions exhibit. (Refer to the Exhibit.) 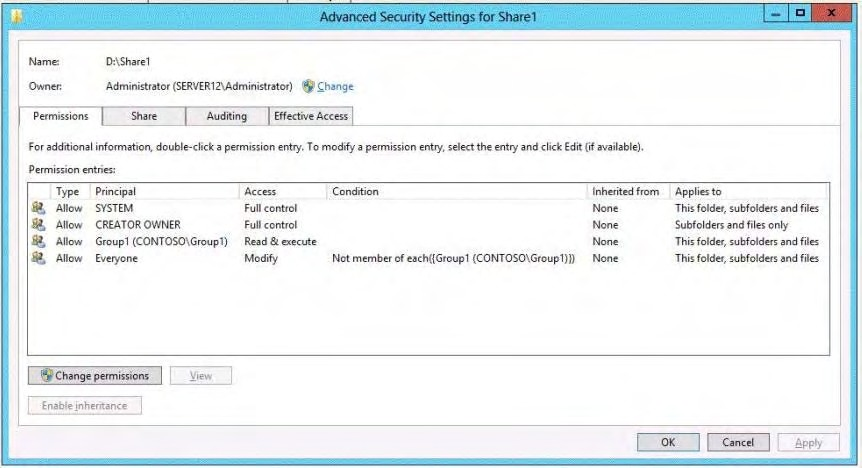
The Share permissions of Share1 are configured as shown in the Share Permissions exhibit. (Click the Exhibit
button.)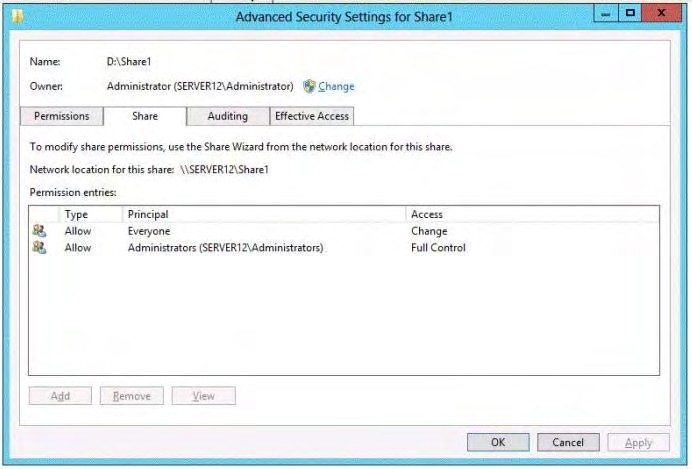
You have a group named Group1. The members of Group1 are shown in the Group1 exhibit. (Click the Exhibit
button.)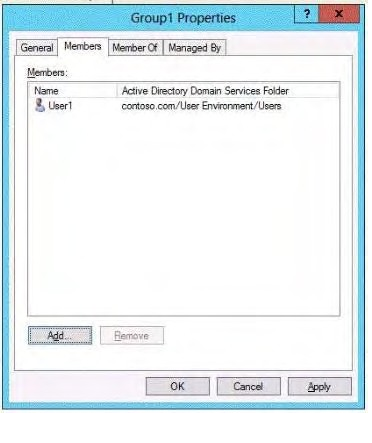
Select Yes if the statement can be shown to be truebased on the available information; otherwise select No.
Each correct selection is worth one point.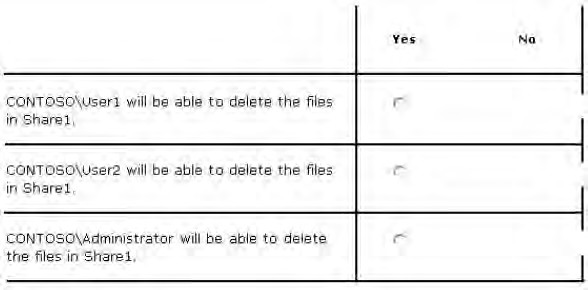
What should you identify?
You have a server named Server1 that runs a Server Core installation of Windows Server 2012 Standard.
You establish a Remote Desktop session to Server1.
You need to identify which task can be performed onServer1 from within the Remote Desktop session.
What should you identify?
Which tool should you use?
Your network contains an Active Directory domain named contoso.com. The domain contains two servers
named Server1 and Server2 that run Windows Server 2012.
You create a security template named Template1 by using the Security Templates snap-in.
You need to App1y Template1 to Server2.
Which tool should you use?
You need to ensure that the same set of custom starter GPOs are available in adatum.com
HOTSPOT
Your network contains two Active Directory forests named contoso.com and adatum.com. A two-way forest
trust exists between the forests.
You have custom starter Group Policy objects (GPOs)defined in contoso.com.
You need to ensure that the same set of custom starter GPOs are available in adatum.com.
In the table below, identify which action must be performed for the starter GPOs container in each forest. Make
only one selection in two of the rows. Each correctselection is worth one point.
Which settings should you modify from the Local Security Policy?
HOTSPOT
You have a server named Server1 that runs Windows Server 2012. Server1 is a member of a workgroup.
You need to ensure that only members of the Administrators group and members of a group named Group1
can log on locally to Server1.
Which settings should you modify from the Local Security Policy? To answer, select the appropriate settings in
the answer area.
Which authentication method should you configure inthe connection security rule?
You have a server named Server1. Server1 runs Windows Server 2012 and is located in a perimeter network.
You need to configure a custom connection security rule on Server1. The rule must encrypt network
communications across the Internet to a computer atanother company.
Which authentication method should you configure inthe connection security rule?
You need to prevent Group1 from being used to provide access to the resources in contoso.com
Your network contains two Active Directory forests named contoso.com and adatum.com.
All servers run Windows Server 2012.
A one-way external trust exists between contoso.comand adatum.com.
Adatum.com contains a universal group named Group1.
You need to prevent Group1 from being used to provide access to the resources in contoso.com.
What should you do?
Which type of group should you create?
Your network contains an Active Directory forest named contoso.com. The forest contains a child domain
named corp.contoso.com.
The network has Microsoft Exchange Server 2010 deployed.
You need to create a mail-enabled distribution group. Which type of group should you create?

