How can you ensure that the services that are not required are forever disabled on the Web servers without aff
You work as a network administrator for ABC.com. The ABC.com network consists of a single
Active Directory domain named ABC.com. There are currently 120 Web servers running Windows
2000 Server and are contained in an Organizational Unit (OU) named ABC_WebServers
ABC.com management took a decision to uABCrade all Web servers to Windows Server 2003.
You disable all services on the Web servers that are not required. After running the IIS Lockdown
Wizard on a recently deployed web server, you discover that services such as NNTP that are not
required are still enabled on the Web server.
How can you ensure that the services that are not required are forever disabled on the Web
servers without affecting the other servers on the network? Choose two.
How would you capture authentication event details on ABC-DC02 in the Minsk branch office?
You are working as the administrator at ABC.com. ABC.com has headquarters in London and
branch offices in Berlin, Minsk, and Athens. The Berlin, Minsk and Athens branch offices each
have a Windows Server 2003 domain controller named ABC-DC01, ABC-DC02 and ABC-DC03
respectively. All client computers on the ABC.com network run Windows XP Professional.
One morning users at the Minsk branch office complain that they are experiencing intermittent
problems authenticating to the domain. You believe that a specific client computer is the cause of
this issue and so need to discover the IP address client computer.
How would you capture authentication event details on ABC-DC02 in the Minsk branch office?
How would you ensure that all client computers can connect to the server and run the application?
You are working as the administrator at ABC.com. Part of you job description includes the
deployment of applications on the ABC.com network. To this end you operate by testing new
application deployment in a test environment prior to deployment on the production network.
The new application that should be tested requires 2 processors and 3 GB of RAM to run
successfully. Further requirements of this application also include shared folders and installation of
software on client computers. You install the application on a Windows Server 2003 Web Edition
computer and install the application on 30 test client computers.
During routine monitoring you discover that only a small amount of client computers are able to
connect and run the application. You decide to turn off the computers that are able to make a
connection and discover that the computers that failed to open the application can now run the
application.
How would you ensure that all client computers can connect to the server and run the application?
How can you ensure that the dial-up connection is initiated only from the partner company and that access is r
You are an Enterprise administrator for ABC.com. All servers on the corporate network run
Windows Server 2003 and all client computers run Windows XP.
The network contains a server named ABC-SR01 that has Routing and Remote Access service
and a modem installed which connects to an external phone line.
A partner company uses a dial-up connection to connect to ABC-SR01 to upload product and
inventory information. This connection happens between the hours of 1:00am and 2:00am every
morning and uses a domain user account to log on to ABC-SR01.
You have been asked by the security officer to secure the connection.
How can you ensure that the dial-up connection is initiated only from the partner company and that
access is restricted to just ABC-SR01? Choose three.
Which two of the following options should you perform?
You are an Enterprise administrator for ABC.com. The company consists of an Active Directory
domain called ad.ABC.com. All servers on the corporate network run Windows Server 2003. At
present there is no provision was made for Internet connectivity.
A server named ABC2 has the DNS server service role installed. The DNS zones on ABC2 are
shown below: 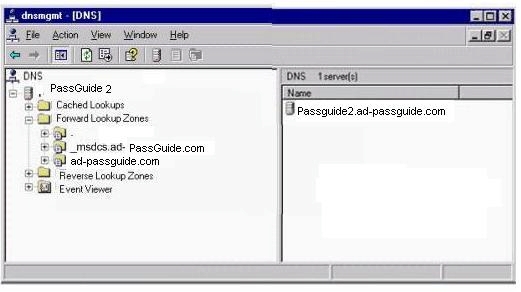
The corporate network also contains a UNIX-based DNS A server named ABC-SR25 hosts a
separate DNS zone on a separate network called ABC.com. ABC-SR25 provides DNS services to
the UNIX-based computers and is configured to run the latest version of BIND and the ABC.com
contains publicly accessible Web and mail servers.
The company has a security policy set, according to which, the resources located on the internal
network and the internal network’s DNS namespace should never be exposed to the Internet.
Besides this, according to the current network design, ABC-SR25 must attempt to resolve any
name resolution requests before sending them to name servers on the Internet.
The company plans to allow users of the internal network to access Internet-based resources. To
implement the security policy of the company, you decided to send all name resolution requests
for Internet-based resources from internal network computers through ABC2. You thus need to
devise a name resolution strategy for Internet access as well as configuring ABC2 so that it will
comply with the set criteria and restrictions.
Which two of the following options should you perform?
How would you apply the security templates so that the settings will be periodically enforced whilst ensuring
You are working as the administrator at ABC.com. The network consists of a single Active
Directory domain named ABC.com with the domain functional level set at Windows Server 2003.
All network servers run Windows Server 2003 and all client computers run Windows XP
Professional.
The ABC.com domain is divided into organizational units (OU). All the resource servers are
contained in an OU named ABC_SERVERS and the workstations are contained in an OU named
ABC_CLIENTS. All resource servers operate at near capacity during business hours. All
workstations have low resource usage during business hours.
You received instructions to configure baseline security templates for the resource servers and the
workstations. To this end you configured two baseline security templates named
ABC_SERVERS.inf and ABC_CLIENTS.inf respectively. The ABC_SERVERS.inf template
contains many configuration settings. Applying the ABC_SERVERS.inf template would have a
performance impact on the servers. The ABC_CLIENTS.inf contains just a few settings so
applying this template would not adversely affect the performance of the workstations.
How would you apply the security templates so that the settings will be periodically enforced whilst
ensuring that the solution reduces the impact on the resource servers? Choose three.
What can you do to mitigate the clusters most obvious security vulnerability?
You are working as the administrator at ABC.com. The ABC.com network consists of a single
Active Directory domain named ABC.com. The ABC.com network contains a DMZ that contains a
two-node Network Load Balancing cluster, which is located in a data centre that is physically
impenetrable to unauthorized persons.
The cluster servers run Windows Server 2003 Web Edition and host an e-commerce website. The
NLB cluster uses a virtual IP address that can be accessed from the Internet.
What can you do to mitigate the clusters most obvious security vulnerability?
How can you add a port rule to the cluster nodes?
You are working for a administrator for ABC.com. The ABC.com network consists of a single
Active Directory domain named ABC.com. All the servers on the network run Windows Server
2003 servers.
You have configured four servers in a network load balancing cluster. You need to enable the
cluster in unicast mode although each server only has one network card. After your configuration,
the NLB cluster has successfully converged.
You discover that you can optimize the use of the cluster by moving a specific application to each
node of the cluster. However for this application to execute, all the nodes of the cluster must be
configured by a Network Load Balancing Port Rule.
When you open Network Load Balancing Manager on one of the NLB nodes, you receive a
message saying that Network Load Balancing Manager is unable to see the other nodes in the
cluster.
How can you add a port rule to the cluster nodes?
How should you configure Group Policy for the ABC_Admin and ABC_Sales OU?
You are working as an administrator for ABC.com. The network consists of a single Active
Directory domain named ABC.com. All server run Windows Server 2003 and all client computer
run Windows XP Professional.
The ABC.com departments are organized into organizational units (OUs). The Administration OU
is named ABC_ADMIN, and the Sales OU is named ABC_SALES. All file servers for all
departments are located in their respective OUs. The ABC_SALES OU is a child OU of the
ABC_ADMIN OU.
A new ABC.com written security policy states that servers in the ABC_ADMIN OU should be
highly secure. All communications with ABC-ADMIN servers should be encrypted. The security
policy also states that auditing should be enabled for file and folder deletion on Sales servers.
Communications with the Sales servers should not be encrypted.
How should you configure Group Policy for the ABC_Admin and ABC_Sales OU? Choose three.
What should you do to automate the process of collecting information on existing vulnerabilities for each comp
You are working as an administrator at ABC.com. The ABC.com network consists of a single
Active Directory domain named ABC.com which contains Windows Server 2003 servers Windows
XP Professional client computers.
You want to improve network security and need to pinpoint all computers that have the known
vulnerabilities.
What should you do to automate the process of collecting information on existing vulnerabilities for
each computer, on a nightly basis?

