which of the following ITIL processes?
Consumption statistics for individual cloud service offerings is used by which of the following ITIL processes?
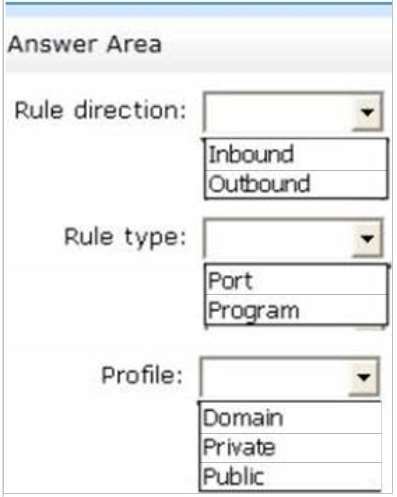
How should you configure the rule?
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains 25 servers. Allservers run Windows Server 2012 R2.
You need to create a Windows Firewall rule to prevent administrators from connecting to Remote Assistance
requests while they are logged on interactively to the servers.
How should you configure the rule?
To answer, select the appropriate options in the answer area.
Hot Area:
which of the following types of cloud?
A company Chef Information Officer (CIO) who wants to ensure rapid elasticity for the company’s cloud solution
would MOST likely choose which of the following types of cloud?
Which cmdlet should you use?
You have a server named Server1 that runs Windows Server 2012 R2.
Your network has IPSec policies configured.
You need to exempt ICMP and router discovery traffic from the IPSec rules in Windows Firewall with Advanced
Security.
Which cmdlet should you use?
Which of the following would be considered a major chal…
Virtual Desktop Interface (VDI) will present challenges for the network administrator as they move their users to
the cloud. Which of the following would be considered a major challenge?
What should you identify?
You have a Hyper-V host named server1 that runs windows server 2012 R2. Server1 host 50 virtual machines
that run Windows Server 2012 R2.
You enable and configure enhanced session mode on Server1.
You need to identify a new functionality available for the virtual machines hosted on server1.
What should you identify?
Which of the following describes the commonality betwee…
Which of the following describes the commonality between cloud computing and outsourcing?
Which cmdlet should you use?
You have a DNS server named DNS1 that runs windows server 2012 R2.
DNS1 is used to resolve the names of internet resources by using several DNS forwarders.
You need to prevent DNS1 from performing iterative queries if the DNS forwarders are unable to reslove the
queries.
Which cmdlet should you use?
which of the following is MOST important to acquire and…
From a risk assessment perspective, which of the following is MOST important to acquire and review before a
business integrates cloud computing into its existing environment?
You need to identify the settings that are prevented fr…
You have a server named Server1 that runs Windows Server 2012 R2.
You apply a security policy to server1 by using the Security Configuration Wizard (CWM).
You plan to roll back the security policy.
You need to identify the settings that are prevented from rolling back running the CWM
Witch settings should you identify.