Which technique is most appropriate to use for the suitability test?
For the on-line portal a test will be planned that will focus on suitability. Which technique is most
appropriate to use for the suitability test?
Which of the following risk analysis techniques are you working with?
You are performing a quality risk analysis for a CSCI (Computer Software Configuration Item)
used to implement a CBIT (Continuous Built-In Test) module of a safety-critical system.
During the quality risk analysis you are trying to identify the ways in which failures of the CBIT
module can occur, for each of them trying to determine the potential causes and likely effects, and
the risk level (calculated as the product of three factors: severity, occurrence and detection).
Which of the following risk analysis techniques are you working with?
Which of the following statements is NOT correct?
Scenario “Tax system”
The tax system needs to be updated due to new legislation. For a person with a salary of less than
€ 20.000 and who is married, the tax needs to be re-calculated. If the person also has more than
two and less than five children, an additional 10% reduction is applicable.
A SUMI test has been performed on the user-interface of the tax system. The resulting SUMI
graph is presented below: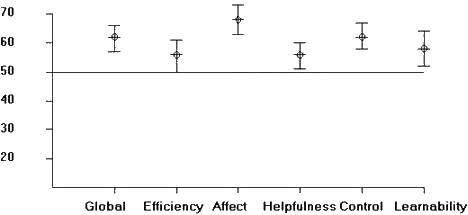
Which of the following statements is NOT correct?
You are currently performing a quality risk analysis using FME
You are working on a project to develop an authentication system for an e-commerce website.
This system provides two features: Registration and authentication. Two different development
teams develop these two features.
There is a high likelihood that the delivery of the authentication feature to the test team will be
three weeks later. To complete the registration the user must provide the following registration
inputs: Name, surname, birth date, fiscal code and he/she can select a username and a password.
A registered user can be a special user or a normal user. To be identified as a special user,
he/she must also provide, during the registration process, a voucher possibly received from the IT
department.
Access is granted only if a user is registered and the password is correct: In all other cases access
is denied. If the registered user is a special user and the password is wrong, a special warning is
shown on the system console.
You are currently performing a quality risk analysis using FMEA.
Based only on the given information, which of the following is NOT a product risk that could be
identified during the quality risk analysis?
Which of the following is a typical defect that boundary value analysis would identify?
Which of the following is a typical defect that boundary value analysis would identify?
Which of the following statements describing how identified product quality risks should be mitigated and mana
Which of the following statements describing how identified product quality risks should be
mitigated and managed, is true?
Which of the following practices is NOT part of exploratory testing?
The use of exploratory testing is also being considered. Which of the following practices is NOT
part of exploratory testing?
Which of the following statements about management of product quality risks in mature organizations with respe
Which of the following statements about management of product quality risks in mature
organizations with respect to the lifecycle, is true?
What is the BEST option regarding the level of detail and documentation required for test cases in the project
As a test analyst you are involved in the early stages of an acceptance test for a Product Data
Management system. You are asked to write test designs and test cases based on use cases. An
early version of the system is also already available. It is a known fact that on the implementation
level many things will change (including the user-interface). The tests will be carried by end-users
with much domain knowledge who have also been involved in the project defining the user
requirements and reviewing documentation.
What is the BEST option regarding the level of detail and documentation required for test cases in the project?
Which of the following criteria on test progress would enable the business to determine a likely ‘go live’
Which of the following criteria on test progress would enable the business to determine a likely ‘go live’ date?
(i) Number of tests planned versus number of tests executed
(ii) Number of high priority defects outstanding
(iii) The test team’s timesheets in order to show how much effort has been devoted to testing
(iv) Number of tests passed and number failed
(v) Number of defects found in each development area
(vi) The rate at which defects are being found

