Of CPTED’s three main components, what is illustrated in the following photo?
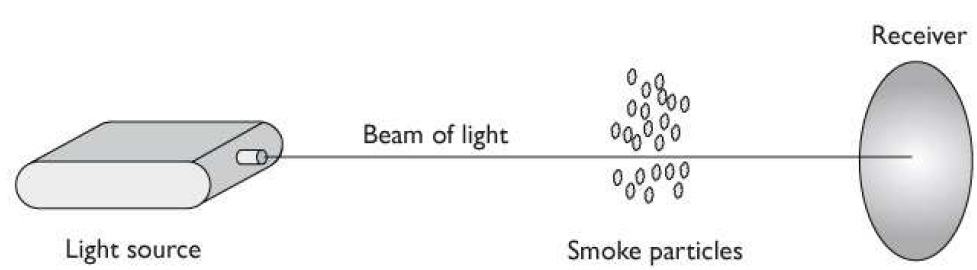
What type of detector is shown in the following graphic?
What type of fence detects if someone attempts to climb or cut it?
What type of fence detects if someone attempts to climb or cut it?
Which of the following is best to keep voltage steady and power clean?
A number of measures should be taken to help protect devices and the environment from electric power issues. Which of the following is best to keep voltage steady and power clean?
Which of the following steps comes first in the process of rolling out a security program?
Before an effective physical security program can be rolled out, a number of steps must be taken. Which of the following steps comes first in the process of rolling out a security program?
Which of the following is not true of IDSs?
Which of the following is not true of IDSs?
What locking mechanisms should he use for the primary and secondary server room entry doors?
David is preparing a server room at a new branch office. What locking mechanisms should he use for the primary and secondary server room entry doors?
Which of the following intrusion detection systems is the most appropriate for protecting the painting?
Sarah recently learned that the painting she inherited from a relative and hung in her downtown coffee shop is worth a lot of money. She is worried about its protection and wants to install an IDS. Which of the following intrusion detection systems is the most appropriate for protecting the painting?
Which of the following is not an important factor when choosing a location?
Paisley is helping her company identify potential site locations for a new facility. Which of the following is not an important factor when choosing a location?
What type of IDS emits a measurable magnetic field that it monitors for disruptions?
There are several types of volumetric IDSs. What type of IDS emits a measurable magnetic field that it monitors for disruptions?