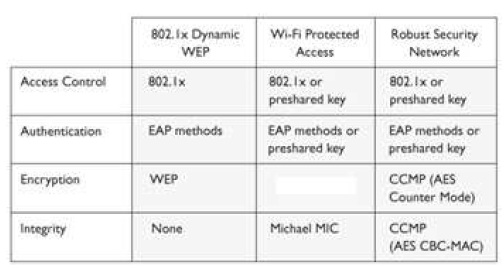
What type of security encryption component is missing from the table that follows?
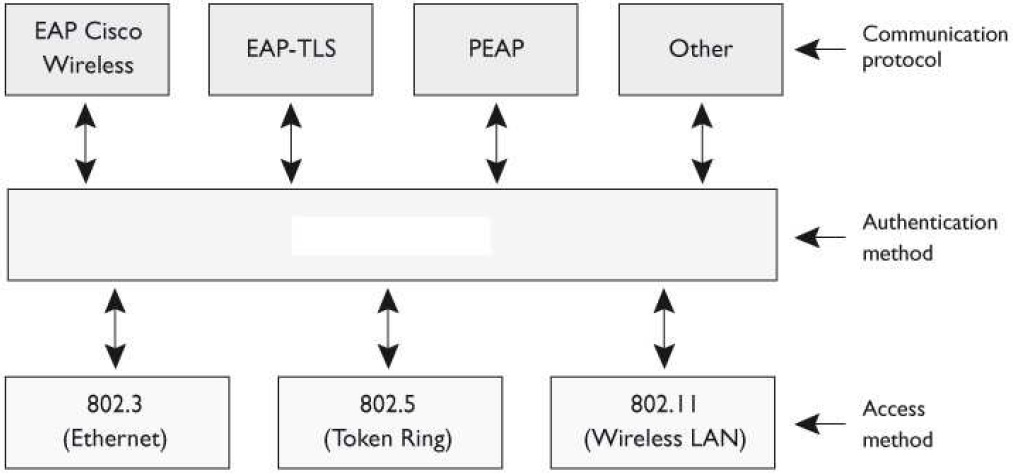
Which type is being shown in the graphic that follows?
Which of the following should not be included in his presentation?
Brad is a security manager at Thingamabobs Inc. He is preparing a presentation for his company’s executives on the risks of using instant messaging (IM) and his reasons for wanting to prohibit its use on the company network. Which of the following should not be included in his presentation?
What two prerequisites are needed for two different locations to communicate via satellite links?
Today, satellites are used to provide wireless connectivity between different locations. What two prerequisites are needed for two different locations to communicate via satellite links?
Which of the following is not a benefit of VoIP?
Which of the following is not a benefit of VoIP?
Which of the following best describes why e-mail spoofing is easily executed?
Which of the following best describes why e-mail spoofing is easily executed?
Which of the following best describes why this is done?
When an organization splits naming zones, the names of its hosts that are only accessible from an intranet are hidden from the Internet. Which of the following best describes why this is done?
Which of the following does not describe IP telephony security?
Which of the following does not describe IP telephony security?
Which of the following categories of routing protocols builds a topology database of the network?
Which of the following categories of routing protocols builds a topology database of the network?
Which of the following is a proprietary interior protocol that chooses the best path between the source and de
Both de facto and proprietary interior protocols are in use today. Which of the following is a proprietary interior protocol that chooses the best path between the source and destination?