Which of the following best describes operations security?
Which of the following best describes operations security?
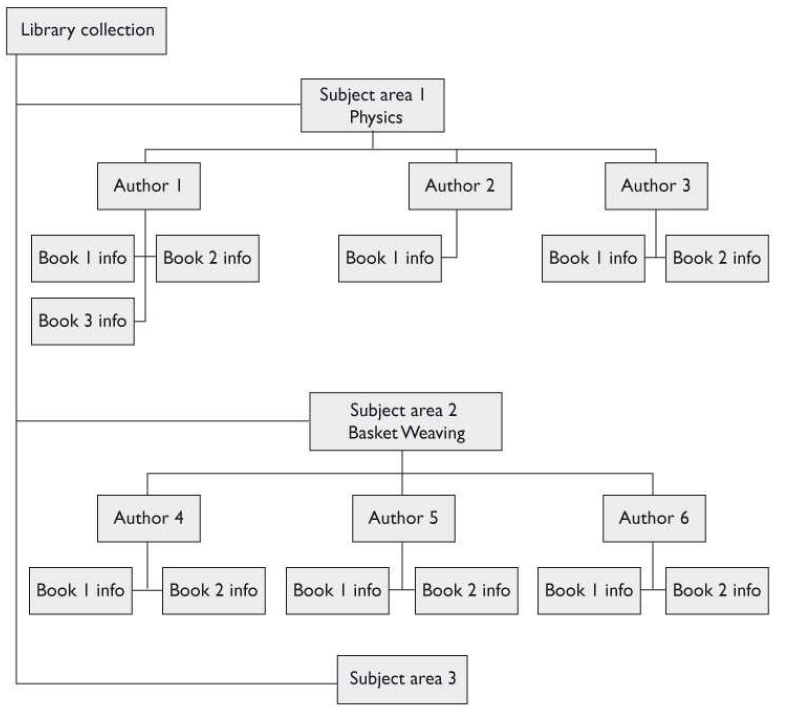
Which type does the graphic that follows illustrate?
Which of the following best describes the concept that this graphic is showing?
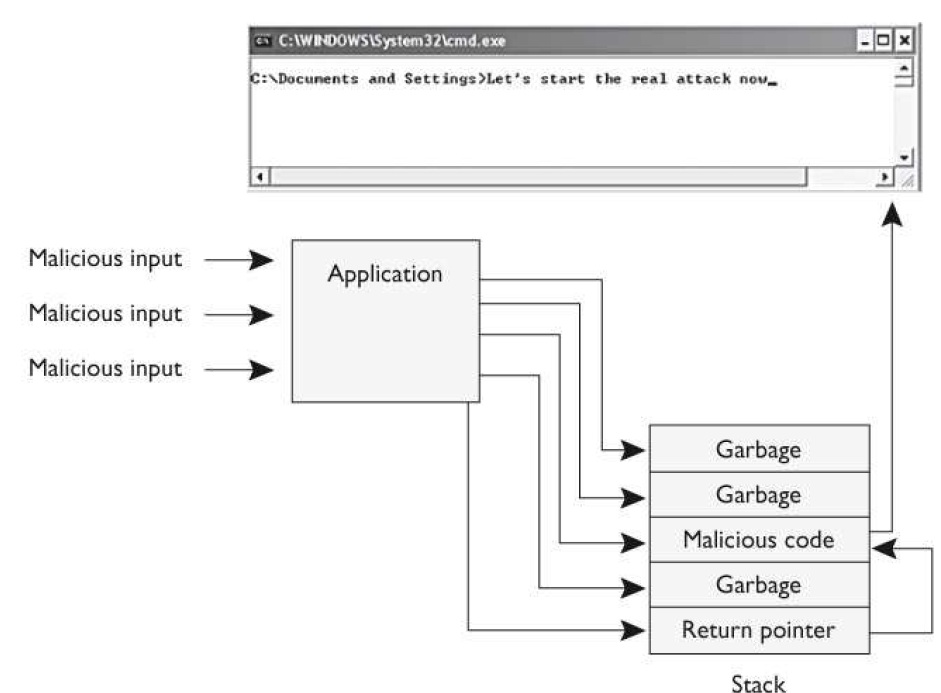
What attack does the graphic that follows illustrate?
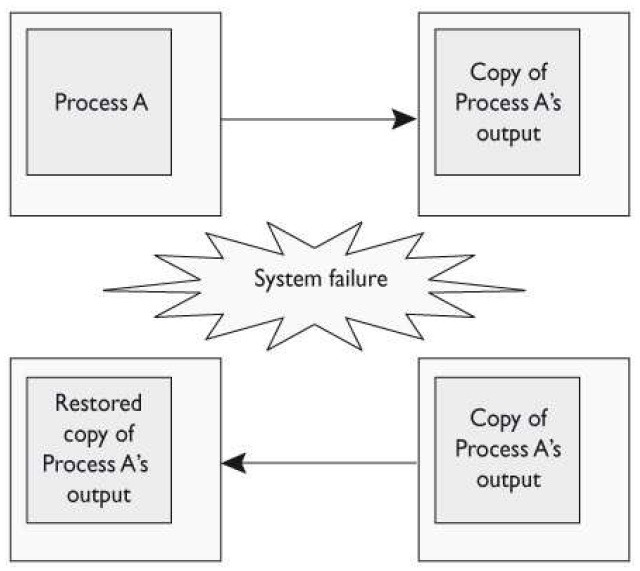
What type of protection method is illustrated in the graphic that follows?
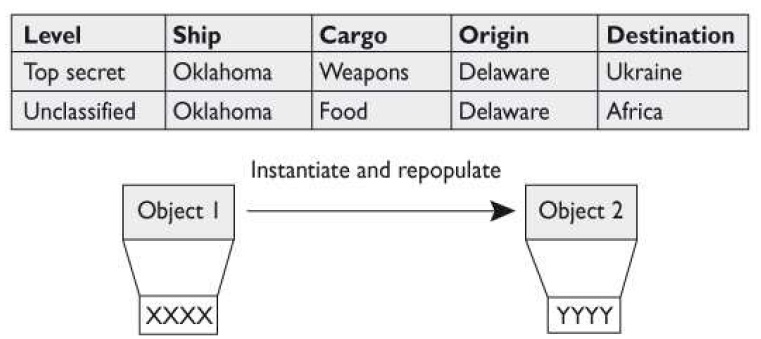
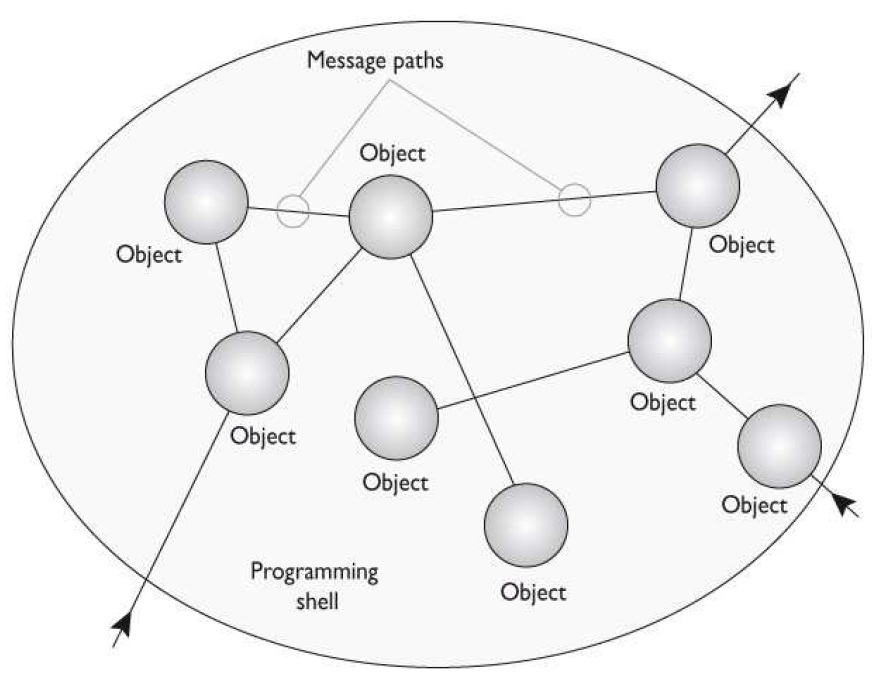
What object-oriented programming term, or concept, is illustrated in the graphic that follows?
Which of the following describes object-oriented programming deferred commitment?
Which of the following describes object-oriented programming deferred commitment?
Which of the following antivirus detection methods is the most recent to the industry and monitors suspicious
Which of the following antivirus detection methods is the most recent to the industry and monitors suspicious code as it executes within the operating system?
Of the following steps that describe the development of a botnet, which best describes the step that comes fir
Of the following steps that describe the development of a botnet, which best describes the step that comes first?
What type of cross-site scripting vulnerability is she exploiting?
Mary is creating malicious code that will steal a user’s cookies by modifying the original client-side Java script. What type of cross-site scripting vulnerability is she exploiting?