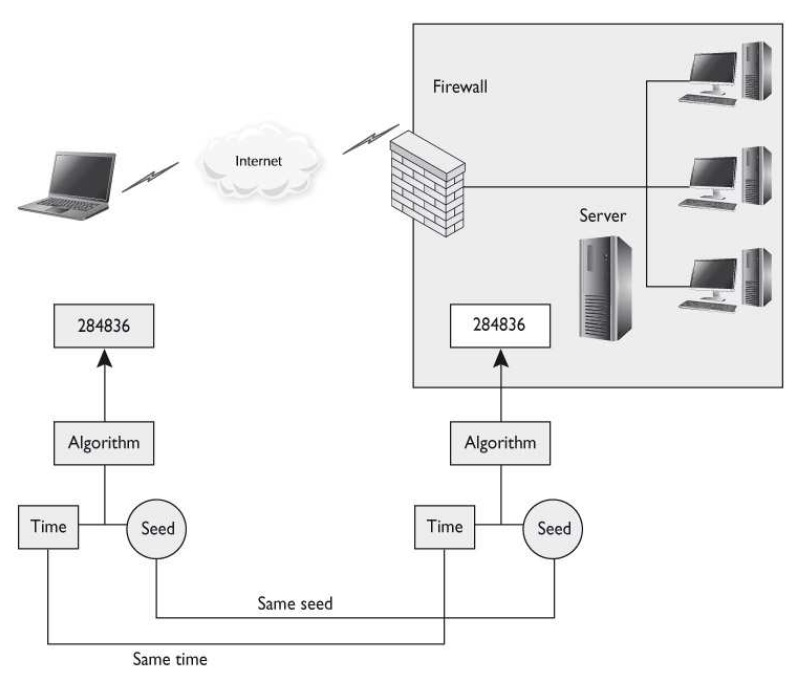
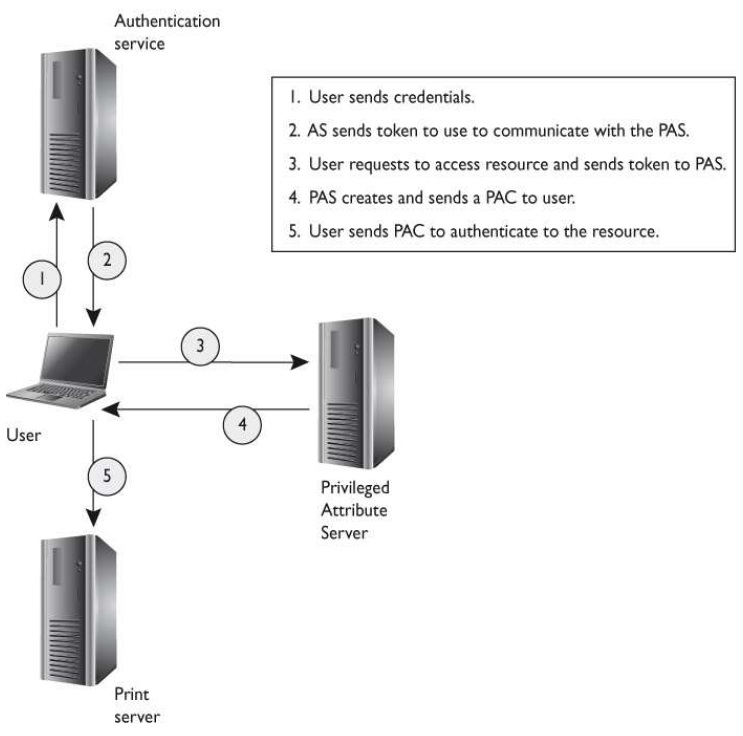
What is the main purpose of implementing and using a guard?
A guard is commonly used with a classified system. What is the main purpose of implementing and using a guard?
What is the purpose of base and limit registers?
What is the purpose of base and limit registers?
The Information Technology Security Evaluation Criteria was developed for which of the following?
The Information Technology Security Evaluation Criteria was developed for which of the following?
Which of the following best describes the security kernel?
Which of the following best describes the security kernel?
Which is the first level of the Orange Book that requires classification labeling of data?
Which is the first level of the Orange Book that requires classification labeling of data?
What security advantage does firmware have over software?
What security advantage does firmware have over software?
What feature enables code to be executed without the usual security checks?
What feature enables code to be executed without the usual security checks?
If an operating system allows sequential use of an object without refreshing it, what security issue can arise
If an operating system allows sequential use of an object without refreshing it, what security issue can arise?