Which of the following DoD directives defines DITSCAP as the standard C&A process for the Department of De
Which of the following DoD directives defines DITSCAP as the standard C&A process for the
Department of Defense?
Which of the following are the responsibilities of a custodian with regard to data in an information classific
Which of the following are the responsibilities of a custodian with regard to data in an information
classification program? Each correct answer represents a complete solution. Choose three.
Which of the following terms refers to the protection of data against unauthorized access?
Which of the following terms refers to the protection of data against unauthorized access?
Which of the following security challenges does DRM include?
Copyright holders, content providers, and manufacturers use digital rights management (DRM) in
order to limit usage of digital media and devices. Which of the following security challenges does
DRM include? Each correct answer represents a complete solution. Choose all that apply.
Which of the following describes the acceptable amount of data loss measured in time?
Which of the following describes the acceptable amount of data loss measured in time?
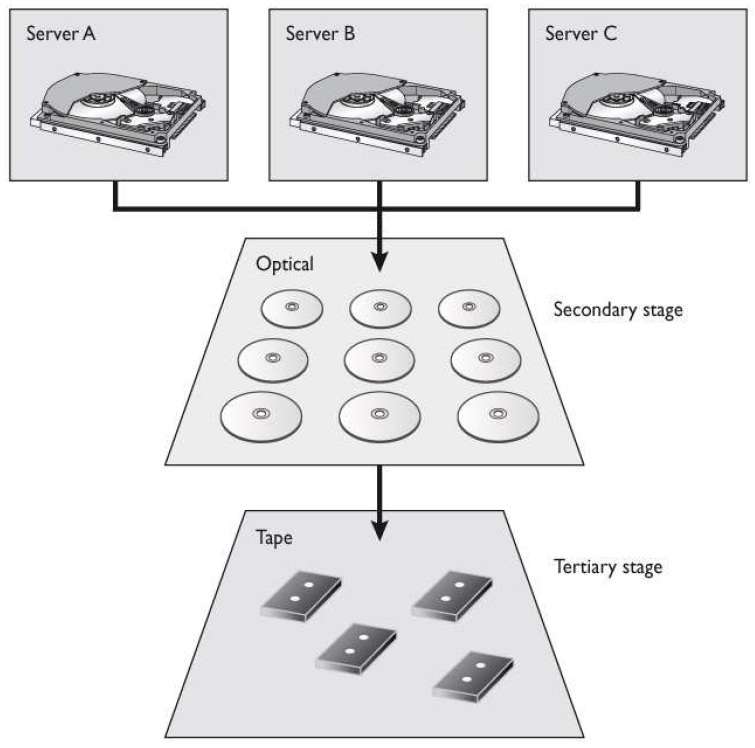
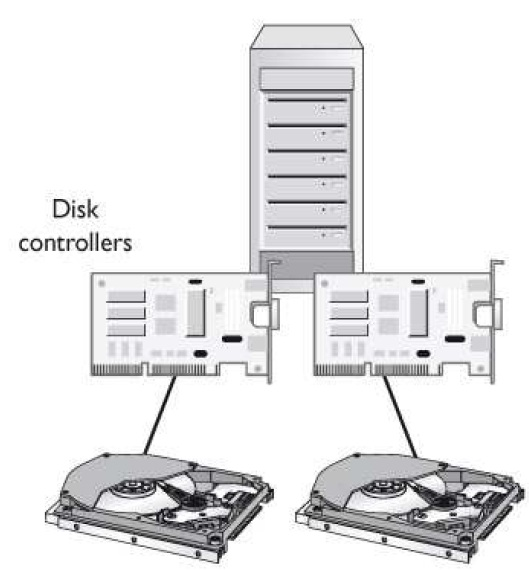
Which architecture does the graphic that follows represent?
What similar type of technology is shown in the graphic that follows?
What is parity information used for?
Which of the following is not one of those guidelines?
Guidelines should be followed to allow secure remote administration. Which of the following is not one of those guidelines?
What course of action should Brian take?
Brian, a security administrator, is responding to a virus infection. The antivirus application reports that a file has been infected with a dangerous virus and disinfecting it could damage the file. What course of action should Brian take?