Which of the following frameworks defines ERM as a process, effected by an entity’s board of directors,
Which of the following frameworks defines ERM as a process, effected by an entity’s board of
directors, management, and other personnel, applied in strategy setting and across the
enterprise?
Which of the following would be MOST effective in successfully implementing restrictive password policies?
Which of the following would be MOST effective in successfully implementing restrictive password
policies?
What risk identification method is Mary likely using?
Mary is a project manager in her organization. On her current project she is working with her
project team and other key stakeholders to identify the risks within the project. She is currently
aiming to create a comprehensive list of project risks so she is using a facilitator to help generate
ideas about project risks. What risk identification method is Mary likely using?
True or false?
Atomicity enforces data integrity by ensuring that a transaction is either completed in its entirely or
not at all. Atomicity is part of the ACID test reference for transaction processing. True or false?
what risk response?
You are the project manager of the HJK project for your organization. You and the project team
have created risk responses for many of the risk events in the project. A teaming agreement is an
example of what risk response?
Drag and drop the ITIL processes that focus on service operation, i.e. operational processes in Service Suppor
DRAG DROP
The Information Technology Infrastructure Library (ITIL) is a set of concepts and policies for
managing information technology (IT) infrastructure, development, and operations. Drag and drop
the ITIL processes that focus on service operation, i.e. operational processes in Service Support,
in the correct places.
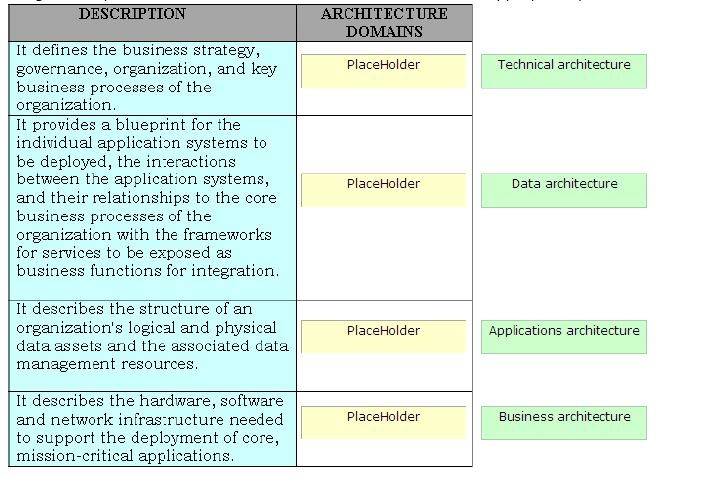
Drag and drop the various architecture domains for TOGAF at the appropriate places.
Which of the following concepts is a semi-standard structured report supported by proven design methods and au
Which of the following concepts is a semi-standard structured report supported by proven design
methods and automation tools that can be used by managers to keep track of the execution of
activities by staff within their control and monitor the consequences arising from these actions?
When designing an information security quarterly report to management, the MOST important element to be consid
When designing an information security quarterly report to management, the MOST important
element to be considered should be the:
Which of the following is an administrative control?
Which of the following is an administrative control?