Which command does the system administrator need to run to set the userId and password on the broker?
A company has the requirement to have their message flow application running on broker BRK1
communicate with the CICS Transaction Server. The message flow application contains CICSRequest
node that has security identity defined as mySecurityIdentity. The CICS Transaction server only
accepts the transactions from applications if they are sent by the userId user1 with password
password1. Which command does the system administrator need to run to set the userId and
password on the broker?
Which commands does the system administrator need to run to configure PKI at the execution group level?
A system administrator is configuring Public Key Infrastructure (PKI) for an execution group EG1 that
is deployed to broker BRK1. The development team informed the system administrator that their
requirement is to send the SOAP requests to an external web service provider. The provider only
receives https requests and requires to authenticate the broker requests as well. Which commands
does the system administrator need to run to configure PKI at the execution group level?
Which one of the following external security providers can the system administrator use?
A message flow needs to be secured based on the identity credentials. A system administrator is
asked to configure the message flow security for authorization, identity mapping and authentication.
Which one of the following external security providers can the system administrator use?
Which command does the system administer need to run to create the profile?
A system administrator has been asked to configure the security profile to the enterprise TFIM v6.2
security server. The profile is to be used by message flows for authentication mapping and
authorization from WebSphere Message Broker BRK1.
The TFIM server information provided is as follows: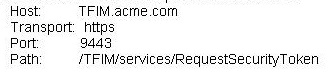
Which command does the system administer need to run to create the profile?
What did the system administrator miss?
A development team has been notified that all the requests serviced by their SOAPInput node
message flow will now contain wsse headers for authentication, encryption and signatures. The
system administrator created the security profile with authentication set to use LDAP and asked the
development team to associate the flow’s BAR file with the security profile and redeploy it to the
broker. When the requests were sent to the broker, they were not processed. What did the system
administrator miss?
The system administrator missed: 1. creating the policy set
What should the system administrator do to get the developer to understand the security exception?
A system administrator is asked to assist a developer who has setup a message flow that uses an
HTTP Input node to securely process SOAP messages deployed to run on LINUX broker BRK1. After
xdeploying the flow into the production environment, the application invoking the flow is receiving a
failure response. What should the system administrator do to get the developer to understand the
security exception? Have the developer:
Which of the following three tasks performed by the security manager require the use of TFIM?
A system administrator configures a message flow security to perform the end-to-end processing of
all identity credentials that are carried in a message through a message flow using IBM Tivoli
Federated Identity Manager (TFIM). Which of the following three tasks performed by the security
manager require the use of TFIM? (choose 3)
Which command does the system administrator need to run?
The broker administration security has been set up on a broker BRK1 for a developer dev1. In
addition to the existing security setting, a system administrator is asked to set security permissions
for data capture so that the developer can perform the record and replay actions on the broker.
Which command does the system administrator need to run?
What did the system administrator do wrong?
A system administrator was asked to create a security identity “ftp::FTP1” associated with a user
ftpuser1 and its password password1. The message flow containing the FileOutput node with the
correct ftp credentials has been deployed to the broker BRK1 on Linux system already. The system
administrator ran the command: mqsisetdbparms BRK1 -n ftp::FTP1 -u ftp\user1 -p password1 When
the transaction was processed, the output file was not generated on the ftp server and the failure
reported incorrect user credentials. What did the system administrator do wrong?
What does the system administrator need to do?
A company has multiple users that access broker using web user interface. The system administrator
of the company has been asked to define security for a group of users in such a way that user1 is
able to view all the broker resources, user2 is able to view and modify all the broker resources and
user3 is able to view and modify selected broker resources. What does the system administrator
need to do?

