which role can perform a restore operation in a non-Active Directory environment?
When using the IBM Tivoli Storage Manager FastBack (TSM FastBack) for Bare Machine
Recovery CD, which role can perform a restore operation in a non-Active Directory environment?
what advantage does the certification bring to IBM?
When the “Open Group” certifies an IBM product, what advantage does the certification bring to
IBM?
Can the unused partition on the operating system disk be added to the repository as an additional disk reposit
A server has two internal disks and each disk is 73 GB in size. The first disk is partitioned into 30
GB for the operating system, and has an unused partition of 43 GB. The second disk has been
used by IBM Tivoli Storage Manager FastBack as a disk repository. Can the unused partition on
the operating system disk be added to the repository as an additional disk repository?
What is the primary security requirement indicated by the customer statement?
In a conversation about business requirements, a customer states:
We are going through the latest big initiative right now. The focus is on time to market with new,
bigger and better Web-based business applications. We have no time for implementing stronger
security and we do not see how you can help us with this.” What is the primary security
requirement indicated by the customer statement?
Which level of cleanup configuration needs to be selected?
An enterprise maintains a high number of generations of snapshots, which use a lot of storage
space. In addition, there is a lot of network traffic. The enterprise needs to select a level of cleanup
that will recover space from old snapshot generations, with little impact on the bandwidth. Which
level of cleanup configuration needs to be selected?
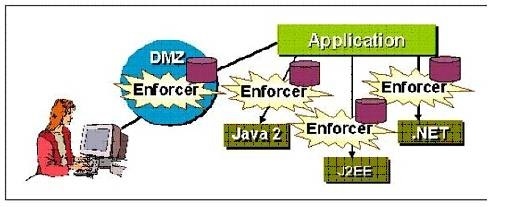
Which security scenario is indicated by the word "Enforcer" that appears several times in the exhibi
which IBM Tivoli Storage Manager FastBack for Bare Machine Recovery was performed never be left unmonitored?
Why should machines on which IBM Tivoli Storage Manager FastBack for Bare Machine Recovery
was performed never be left unmonitored?
Which protocol was developed jointly by IBM, Microsoft, and VeriSign?
Which protocol was developed jointly by IBM, Microsoft, and VeriSign?
How is the Administrative Command Line accessed?
How is the Administrative Command Line accessed?
Which term is used to denote such a system?
A business-partner of IBM, specializing in security products, is interested in setting up a specific
system configured to simulate a few common network services. They want to intentionally leave it
exposed to the external network access, in order to attract would-be attackers and study their
attack patterns. Which term is used to denote such a system?