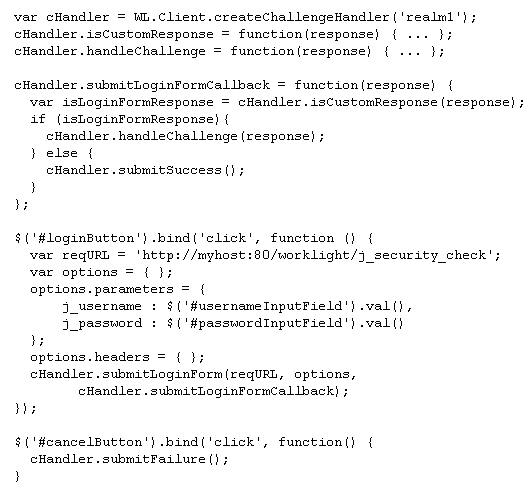
What is the problem with this challenge handler?
Which three components must be implemented when defining an authentication realm?
Which three components must be implemented when defining an authentication realm? (Choose
three.)
properties file to properly configure it for deployment to the production environment?
A developer is preparing a Worklight mobile application for deployment to a production
environment where the Worklight Server core database is stored on DB2 and must be accessed
using the WorklightDS data source.
Which database properly settings must the developer specify in the application’s worklight.
properties file to properly configure it for deployment to the production environment?
Which of the following is a significant cause of failure when using the technology-focused approach to BI Appl
Which of the following is a significant cause of failure when using the technology-focused
approach to BI Application development?
Which of the following describes how developers would validate their tests in the design step of the V-model?
The V-Model testing process specifies that developers should both verify and validate each test.
Which of the following describes how developers would validate their tests in the design step of
the V-model?
Which of the following describes the major steps in the deployment process for a Cognos 8 BI application and t
Which of the following describes the major steps in the deployment process for a Cognos 8 BI
application and their proper order?
Which of the following is correct regarding report execution requests?
Which of the following is correct regarding report execution requests?
Which of the following is correct regarding the processing of a PageDown high affinity request?
Which of the following is correct regarding the processing of a PageDown high affinity request?
Which service is required when a user views saved report output?
Which service is required when a user views saved report output?
what is the correct flow of the request?
If anonymous access is disabled, when a user accesses Cognos 8 BI, what is the correct flow of
the request?