How can this transport be configured to be encrypted?
A company has implemented a Web Service (WS) in IBM Sterling B2B Integrator (SBI). The WS is
using unencrypted HTTP as transport. The SBI is deployed as a single node instance. How can
this transport be configured to be encrypted?
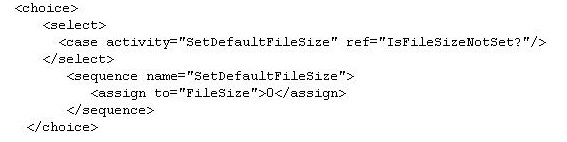
what will the value of "c" be in ProcessData when the Business Process (BP) completes successfully?
Where is this configured?
An inbound EDI process receives X12 and EDIFACT files where the functional group can contain
multiple X12 transaction sets or EDIFACT messages. However, it is a requirement of the backend
interface that will receive the translated data that only one transaction or message per file is
delivered to the interface. Where is this configured?
Which error will trigger the onFault in the BP?
Which feature can be used by the customer to reference the two FTP Client adapter instances by a common name i
A customer does a very large volume of outbound FTP sessions. To help facilitate the throughput
and provide load-balancing and fail over support, the customer created two FTP Client Adapter
instances associated with two Perimeter Servers deployed on two separate servers. Which feature
can be used by the customer to reference the two FTP Client adapter instances by a common
name in the Graphical Process Modeler (GPM) or BPML?
What happens if this BP already exists?
A developer is importing a Business Processes (BP) called ftp_CompanyA into production via
Resource Manager and Object Updates is set to Yes. What happens if this BP already exists?
Which adapter could be set to bootstrap when a file is found?
A company wants a Business Process (BP) to be triggered by the arrival of a file in a particular
folder. Which adapter could be set to bootstrap when a file is found?
Authentication of theA developer has been tasked with writing a communications process to connect to a partner
A developer has been tasked with writing a communications process to connect to a partner SFTP
server and get order files. Authentication of theA developer has been tasked with writing a
communications process to connect to a partner? SFTP server and get order files. Authentication
of the user is being performed by a key signature to the partner SFTP server.user is being
performed by a key signature to the partner? SFTP server. Which two keys are required for
establishing an SFTP session to the SFTP server? (Choose two.)
Which service would provide the optimal performance for the timing logic?
In an FTP pull scenario with many trading partners, if the expected file is not available at the
external FTP Server, the Business Process (BP) should reconnect and check for the file again
after about 15 – 30 minutes. Which service would provide the optimal performance for the timing
logic?